Spankey Campaign
Manage your
SSh Key Life-Cycle
Into WebADM

Manage UNIX and Linux based operating systems
What is SSH?
Secure Shell (SSH) offers a secure way for a person or device to gain access to one system (or server) from another. It replaces the standard username and password with a trusted SSH key pair to provide simpler and more secure ongoing access to remote systems. This ongoing access can cover activities like system administration, automated processes, and managing mission-critical network infrastructure. SSH is the de-facto way for administrators to manage UNIX and Linux based operating systems, with enterprises around the world relying on it every day, which makes poorly managed SSH controls a gaping hole in security and business risk of the highest magnitude.
How keys are securely stored and managed
Why Is SSH Key Management So important?
Most SSH deployments use private/public key pairs to authenticate user access. Key pairs are in many senses more secure than passwords, but they open a whole new Pandora’s box to enterprises: key management, the need to control how keys are securely stored and managed, from creation to revocation and deletion. Without proper key management, UNIX and Linux logins in an enterprise go ungoverned, lacking oversight on which key belongs to which identity and if the connections established with the keys comply with company’s policies and guidelines. In practice, this means that an unknown identity may log in to a critical production system with a key that is not even known to exist.
SSH key management is essential to maintaining security since the entire SSH protocol, and therefore the security of it, is built around public and private key pairs. Proper SSH key management protects against critical risks that can lead to system failures or allow important information to fall into the wrong hands.
SSH key management is essential to maintaining security since the entire SSH protocol, and therefore the security of it, is built around public and private key pairs. Proper SSH key management protects against critical risks that can lead to system failures or allow important information to fall into the wrong hands.
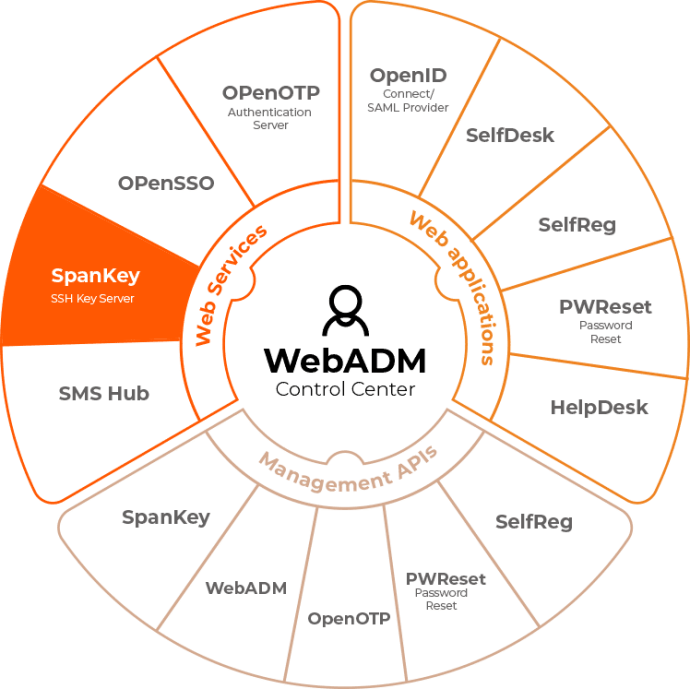
RCDevs SPANKEY
Manage your SSH Key through our Identity & Access Management platform (Webadm)
RCDevs SpanKey is an SSH key life-cycle management solution that makes SSH key-based controls and governance exceptionally easy and effortless, combining them with the existing standard Identity Management solutions. Unlike most SSH key management solutions, SpanKey does not depend on heavy to deploy key vaults, but operates together with a standard LDAP/AD, with user-to-key and key-to-host associations intuitively managed in LDAP/AD accounts and groups. SpanKey provides a centralized and complete SSH key life-cycle management solution with only subtle changes needed to an LDAP/AD.
Voice biometrics is a unique feature by RCDevs which relies on machine learning technologies which
is able to analyze the human voice fingerprints at a cryptographic level.
Voice biometrics is a unique feature by RCDevs which relies on machine learning technologies which
is able to analyze the human voice fingerprints at a cryptographic level.

A BETTER WAY TO MANAGE SSH KEYS
Ssh key management made easy
No more need to manage SSH authorizations by hand or with scripts. User-to-key, key-to-host and key-to-user associations are conveniently managed at the level of LDAP/AD accounts and groups. SpanKey is the only SSH key management solution fully to support organizational hierarchy and controls of LDAP/AD, without added key vaults or third party entitlements engines needed.
A few more things you need to know to
Get the best out of SpanKey
Graphical Session Recording
With SpanKey, terminal sessions are monitored and recorded. Idle sessions get automatically locked after a configurable time and a user password prompt is used for unlocking. But more important, terminal user sessions are recorded in live into the WebADM secure record database. Session are stored encrypted on either the SQL database or a NAS mount. For audit and investigation purposes, you can also re-play terminal sessions with the session player within WebADM. SpanKey is able to record a one day SSH session in 3 MBytes only! So unlike with competitior solutions where recording gets quickly heavy in storage size, SpanKey lets you keep your audit information for a years without requiring extra terabytes.

Automated Public Key Expiration
Expiring SSH keys after a fixed amount of time is required for ensuring a certain level of trust for the user keys and to comply with ISO or PCI regulations. When SpanKey is configured with key expiration, the users are automatically notified upon expiration of their public. An email is sent with a renewal link allowing them to self-renew their just-expired public key.
Fixed issues with MountPoints having an empty LDAP base DN.
Fixed license expiration issues with trial licenses.
Fixed issues with MountPoints having an empty LDAP base DN.
Fixed license expiration issues with trial licenses.
To request an online demo, you only have to create your account or contact us.
Online Demos are available for free to let you try RCDevs multi-factor in 5 minutes and authenticate with your mobile or Yubikey.