
Streamlining von Sicherheitsvorgängen mit den KI-gestützten Aktivitätsberichten von WebADM
Rationalisierung der Sicherheitsabläufe mit den KI-gesteuerten Aktivitätsberichten von WebADM
Sicherheitsteams verbringen unzählige Stunden mit der Analyse von Protokolldateien, um nach Mustern zu suchen, die auf Bedrohungen oder Compliance-Probleme hindeuten könnten. Dieser manuelle Prozess ist nicht nur zeitaufwändig, sondern auch zunehmend unpraktisch, da Unternehmen täglich Millionen von Authentifizierungs- und Zugangsereignissen generieren. Mit der Veröffentlichung von WebADM Version 2.4 führt RCDevs eine bahnbrechende Funktion ein, die die Art und Weise, wie IT- und Sicherheitsteams mit ihren Zugriffs- und Aktivitätsdaten umgehen, grundlegend verändert: AI-gestützte Tätigkeitsberichte.
Diese innovative Funktion nutzt modernste Sprachmodelle wie OpenAI GPT-4o, Google Gemini, Anthropic Claude und DeepSeek, um automatisch Berichte in natürlicher Sprache aus komplexen Protokolldaten zu generieren und so die traditionellen Barrieren zwischen Rohdaten und verwertbaren Informationen zu beseitigen.
Was sind KI-gestützte Tätigkeitsberichte?
Die KI-gesteuerten Aktivitätsberichte von WebADM stellen einen Paradigmenwechsel gegenüber den herkömmlichen Methoden der Protokollanalyse dar. Anstatt dass Administratoren Tausende von Protokolleinträgen manuell durchforsten oder komplexe SQL-Abfragen schreiben müssen, ermöglicht diese Funktion die Erstellung umfassender, von Menschen lesbarer Berichte durch einfache natürlichsprachliche Eingabeaufforderungen.
Das System sammelt Protokolldaten von verschiedenen integrierten Systemen - einschließlich VPN-Zugang, physischen Badging-Systemen, Client-Anwendungen und Netzwerk-Zugangskontrollgeräten - und verarbeitet diese Informationen mit Hilfe fortschrittlicher KI-Modelle, um detaillierte, kontextbezogene Berichte zu erstellen, die auf die spezifischen betrieblichen Anforderungen zugeschnitten sind.
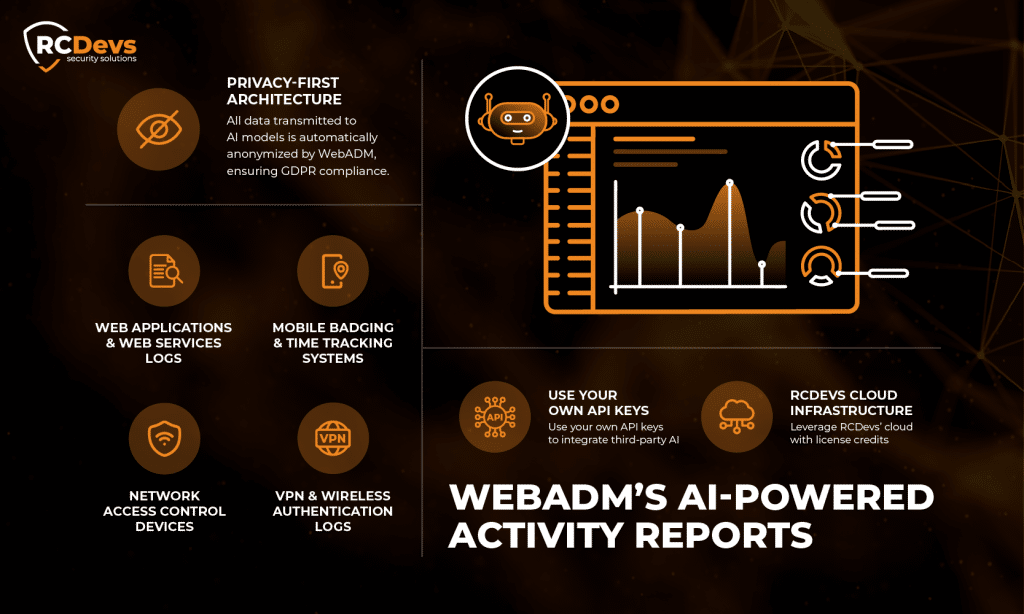
Schlüsselkompetenzen
Umfassende Datenintegration
Die Plattform sammelt Daten aus verschiedenen Quellen, darunter:
- Protokolle von Webanwendungen und Webdiensten
- Mobile Ausweis- und Zeiterfassungssysteme
- Netzzugangskontrollgeräte
- VPN- und drahtlose Authentifizierungsprotokolle
Umfassend Verarbeitung natürlicher Sprache
Administratoren können Berichtsanforderungen mit einfachen englischen Aufforderungen wie z. B.:
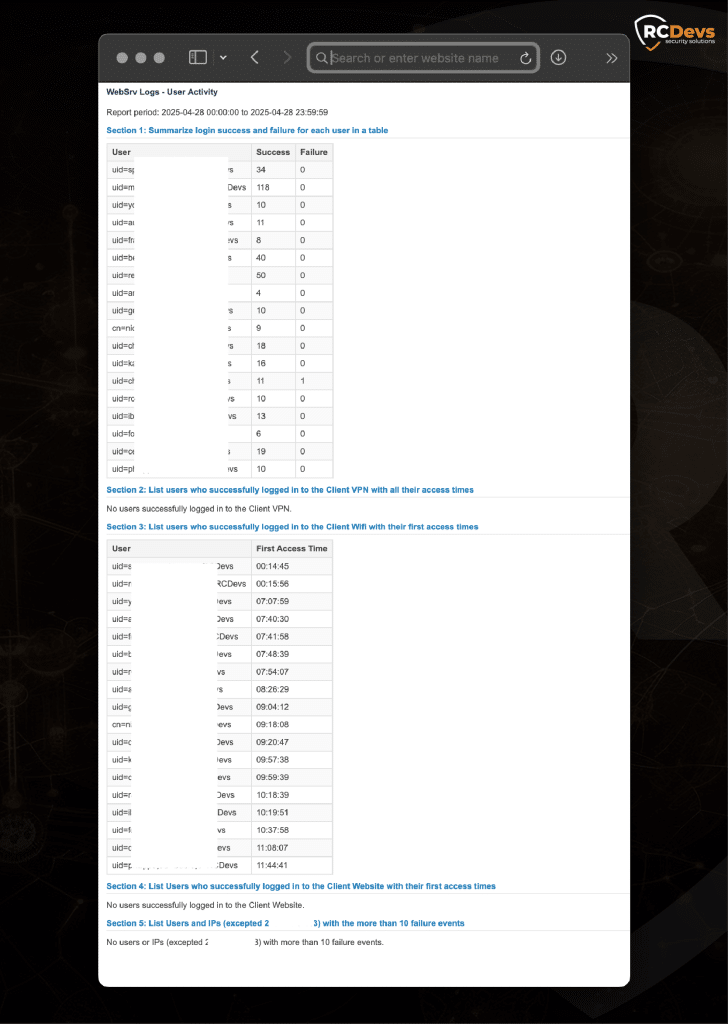
- "Zusammenfassung der Erfolgs- und Misserfolgsraten bei der Anmeldung für alle Benutzer.
- "Benutzer, die auf das VPN zugegriffen haben, mit ihren Verbindungszeiten auflisten"
- "IP-Adressen mit mehr als 10 Authentifizierungsfehlern identifizieren"
Datenschutzorientierte Architektur
Alle an die KI-Modelle übermittelten Daten werden von WebADM automatisch anonymisiert, um die Einhaltung der GDPR-Richtlinien zu gewährleisten und sensible Unternehmensdaten zu schützen, während die Genauigkeit und der Nutzen der Berichte erhalten bleiben.
Flexible Bereitstellungsoptionen
Unternehmen können wählen, ob sie ihre eigenen KI-API-Schlüssel für Modelle von Drittanbietern verwenden oder die Cloud-Infrastruktur von RCDevs über Guthaben nutzen, die an Kundenlizenzen gebunden sind.
Praktische Anwendungen und Anwendungsfälle
Überwachung der Netzwerksicherheit
Stellen Sie sich ein Szenario vor, in dem ein Unternehmen Authentifizierungsmuster in seiner gesamten Netzwerkinfrastruktur überwachen muss. Mit KI-gestützten Aktivitätsberichten können Administratoren automatisierte Berichte erstellen, die:
- Erkennen Sie verdächtige Muster: Automatische Erkennung und Meldung von IP-Adressen oder Benutzerkonten, die ein ungewöhnliches Authentifizierungsverhalten aufweisen, z. B. mehrere fehlgeschlagene Anmeldeversuche oder Zugriff von unerwarteten geografischen Standorten.
- VPN-Nutzung verfolgen: Erstellen Sie umfassende Zusammenfassungen von VPN-Zugriffsmustern, die IT-Teams helfen, Trends bei der Fernarbeit zu verstehen und potenzielle Sicherheitsrisiken zu erkennen.
- Drahtlosen Zugang überwachen: Analysieren Sie die WiFi-Authentifizierungsprotokolle, um die ersten erfolgreichen Verbindungszeiten pro Benutzer zu ermitteln und so ein besseres Verständnis der Ankunftsmuster der Mitarbeiter und der Netzwerknutzung zu erhalten.
Mitarbeiteranwesenheit und Compliance
Für Unternehmen, die integrierte Badging-Systeme verwenden, können KI-gestützte Aktivitätsberichte die Zeiterfassung und Anwesenheitskontrolle verändern:
- Automatisierte Anwesenheitsübersichten: Erstellen Sie tägliche Berichte mit den Ankunftszeiten der Mitarbeiter, den Anwesenheitsindikatoren im Büro und den geografischen Standorten auf der Grundlage der GeoIP-Auflösung.
- Benachrichtigungen bei verspäteter Ankunft: Automatische Erkennung und Meldung von Mitarbeitern, die nach bestimmten Zeiten eintreffen, mit anpassbaren Warnschwellen.
- Überwachung der Ausweiseinhaltung: Erkennen Sie Benutzer, die sich einloggen, aber nicht ausloggen, und identifizieren Sie so mögliche Richtlinienverstöße oder vergessene Check-Outs.
Reaktion auf Vorfälle
Wenn es zu Sicherheitsvorfällen kommt, ist ein schneller Zugriff auf relevante Informationen entscheidend. KI-gestützte Aktivitätsberichte ermöglichen:
- Schnelle Bewertung der Bedrohung: Erstellen Sie schnell Berichte über bestimmte Zeiträume, Benutzerkonten oder IP-Adressen, die in potenzielle Sicherheitsvorfälle verwickelt sind.
- Erkennung von Mustern: Identifizieren Sie subtile Muster in Zugriffsprotokollen, die auf anhaltende Bedrohungen oder Insider-Risiken hindeuten könnten.
- Compliance-Berichterstattung: Erstellen Sie prüfungsreife Berichte, die die Einhaltung von Sicherheitsrichtlinien und gesetzlichen Vorschriften belegen.
Ausführliche Konfigurationsanweisungen und Beispiele finden Sie in der vollständigen Dokumentation
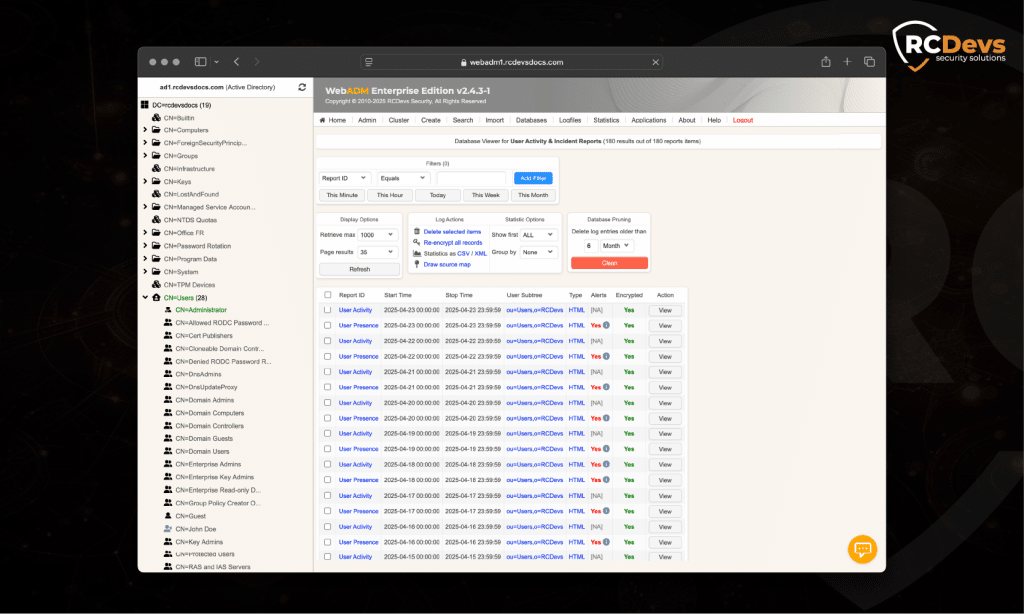
Verringerung der Ermüdung durch Alarme und manuelle Protokollanalyse
Die Krise der Alert Fatigue
Moderne IT- und Sicherheitsoperationen stehen vor einer noch nie dagewesenen Herausforderung: die Überwältigende Menge an Warnungen, Protokollen und Benachrichtigungen die durch die komplexe Infrastruktur von heute erzeugt werden. Dieses Phänomen, das gemeinhin als "Alarmmüdigkeit" bezeichnet wird, ist zu einem erheblichen Hindernis für eine wirksame Sicherheitsüberwachung und betriebliche Effizienz geworden.
Das Ausmaß des Problems
Unternehmensumgebungen erzeugen routinemäßig täglich Millionen von Protokolleinträgen über verschiedene Systeme hinweg - Firewalls, Authentifizierungsdienste, Anwendungsserver, Netzwerkgeräte und Endpunktschutzplattformen. Bei herkömmlichen Ansätzen müssen Sicherheitsanalysten diese Protokolle manuell überprüfen oder sich auf einfache Filtermechanismen verlassen, die oft mehr Rauschen als Signal erzeugen.
Menschliche Beschränkungen
Forschung zeigt immer wieder, dass die menschliche Aufmerksamkeit und Entscheidungsfähigkeit bei sich wiederholenden, umfangreichen Aufgaben deutlich nachlässt. Sicherheitsanalysten, die Stunden damit verbringen, ähnlich aussehende Protokolleinträge zu überprüfen, leiden unweigerlich unter verminderter Wachsamkeit und erhöhten Fehlerquoten, wodurch sie möglicherweise wichtige Sicherheitsereignisse übersehen.
Grundlegende Ursachen der Alert-Müdigkeit
Lautstärke Überlastung
Das exponentielle Wachstum der Datenerzeugung hat die Fähigkeit von Unternehmen, Informationen effektiv zu verarbeiten, überholt. Moderne Unternehmen müssen sich mit:
- Tausende von Authentifizierungsereignissen täglich
- Mehrere Sicherheitstools erzeugen sich überschneidende Warnungen
- Netzwerkzugriffsprotokolle von zahlreichen Geräten und Anwendungen
- Compliance-Anforderungen, die umfassende Prüfpfade erfordern
Schlechtes Signal-Rausch-Verhältnis
Herkömmlichen Warnsystemen mangelt es oft an Raffinesse bei der Unterscheidung zwischen Routineaktivitäten und echten Sicherheitsbedenken:
- Falsche Positivmeldungen: Legitime Aktivitäten, die aufgrund von zu weit gefassten Erkennungsregeln Sicherheitswarnungen auslösen
- Fehlender Kontext: Warnungen, die nicht genügend Hintergrundinformationen für eine schnelle Entscheidungsfindung liefern
- Doppelte Benachrichtigungen: Mehrere Systeme, die bei demselben Ereignis Alarm schlagen, führen zu redundanter Arbeitsbelastung
Unzureichende Prioritätensetzung
Viele Unternehmen tun sich schwer mit der Priorisierung von Warnmeldungen, was dazu führt:
- Kritische Bedrohungen versteckt unter Routinemeldungen
- Uneinheitliche Reaktionszeiten, die auf der Verfügbarkeit der Analysten und nicht auf der Schwere der Bedrohung basieren
- Schwierigkeiten bei der Festlegung klarer Eskalationsverfahren für verschiedene Alarmtypen
Systemkomplexität und mangelnde Ergonomie
Herkömmliche Sicherheitstools präsentieren Informationen oft in Formaten, die es nicht sind:
- Schwierig, schnell zu parsen
- Fehlender visueller Kontext oder Trendanalyse
- Erfordert Fachwissen zum effektiven Dolmetschen
- Zeitaufwändige Korrelationen zwischen mehreren Datenquellen
Umsetzung und erste Schritte
Die KI-gesteuerten Aktivitätsberichte von WebADM sind für eine unkomplizierte Implementierung in unterschiedlichen Unternehmensumgebungen konzipiert. Die Funktion unterstützt flexible Konfigurationsoptionen, die sich an unterschiedliche technische Architekturen und Sicherheitsanforderungen anpassen lassen.
Unternehmen können mit der Nutzung dieser Fähigkeit beginnen:
- Datenquellen konfigurieren: Verbindung bestehender Protokollquellen, einschließlich VPN-Systeme, Badging-Infrastruktur und Anwendungsserver
- Definition der Berichtsanforderungen: Verwendung natürlichsprachlicher Eingabeaufforderungen zur Angabe gewünschter Erkenntnisse und Warnbedingungen
- Automatisierte Planung einrichten: Festlegung regelmäßiger Zeitpläne für die Erstellung und Verteilung von Berichten
- Anpassen der Warnschwellenwerte: Definition von organisationsspezifischen Kriterien für automatische Benachrichtigungen
Die umfassende Dokumentation enthält detaillierte Konfigurationsbeispiele und Best Practices für gängige Anwendungsfälle, die eine schnelle Bereitstellung und sofortige Wertschöpfung gewährleisten.
Mehr als manuelle Protokollanalyse
Die KI-gesteuerten Aktivitätsberichte von WebADM stellen einen bedeutenden Fortschritt in der Identitäts- und Zugriffsmanagement-Technologie dar und sind eine direkte Antwort auf die kritischen Herausforderungen moderner IT- und Sicherheitsabläufe. Durch die Umwandlung komplexer Protokolldaten in verwertbare Informationen mittels natürlicher Sprachverarbeitung ermöglicht diese Funktion Unternehmen den Übergang von reaktiver Sicherheitsüberwachung zu proaktivem, erkenntnisgesteuertem Betrieb.
Die Kombination aus umfassender Datenintegration, intelligenter Analyse und datenschutzgerechtem Design macht diese Technologie zu einem Eckpfeiler für Unternehmen, die ihre Sicherheitslage verbessern und gleichzeitig die betriebliche Effizienz steigern wollen. Da der Umfang und die Komplexität von Unternehmensdaten weiter zunehmen, werden Lösungen wie KI-gestützte Aktivitätsberichte für die Aufrechterhaltung effektiver Sicherheitsabläufe und die Einhaltung gesetzlicher Vorschriften immer wichtiger.
Ausführliche Implementierungsanleitungen, Konfigurationsbeispiele und technische Spezifikationen finden Sie in der vollständigen Dokumentation der AI-gesteuerten Tätigkeitsberichte. Wenn Sie mehr über die umfassenden IAM-Funktionen von WebADM erfahren möchten, besuchen Sie www.rcdevs.com.

