
Tiefe Einblicke: Zwei-Wege-Identitätssynchronisierung mit WebADM und Cloud-IAM-Anbietern
Vertiefung: Zwei-Wege-Identitätssynchronisierung mit WebADM und Cloud-IAM-Anbietern
In unserem letzten Blog, IAM-Management der nächsten Generation für Mixed Cloud Enterprise AD - Der RCDevs-Ansatzhaben wir das Konzept der Synchronisierung von Verzeichnissen in beide Richtungen als eine Kernfunktion der einheitlichen IAM-Plattform von WebADM. In diesem Folgebeitrag werfen wir einen genaueren Blick darauf, wie WebADM Folgendes ermöglicht bidirektionale Synchronisation zwischen lokalen Verzeichnissen wie Active Directory und Cloud-basierten Identitätsanbietern wie Microsoft Entra ID, Okta, Google Workspace, Duo und anderen.
In dieser Einführung wird erläutert, wie WebADM die Identitäts- und MFA-Verwaltung in hybriden Umgebungen umgestaltet und es Unternehmen ermöglicht, die Konsistenz zu wahren, die Sicherheit zu verbessern und die Abläufe über mehrere Verzeichnissysteme hinweg zu optimieren.
Native Integration mit führenden Identitätsanbietern
WebADM bietet native Integration mit einer breiten Palette von cloudbasierten und lokalen Identitätsplattformen, darunter:
- Microsoft Entra ID (Azure Active Directory)
- Microsoft Active Directory (AD)
- Duo-Sicherheit
- Google Arbeitsbereich
- Okta
- Ping-Identität
- OneLogin
Unabhängig davon, ob Ihr Unternehmen einen einzigen Anbieter nutzt oder in einer föderierten Multi-Cloud-Umgebung arbeitet, gewährleistet WebADM eine einfache Synchronisierung und Kontrolle.
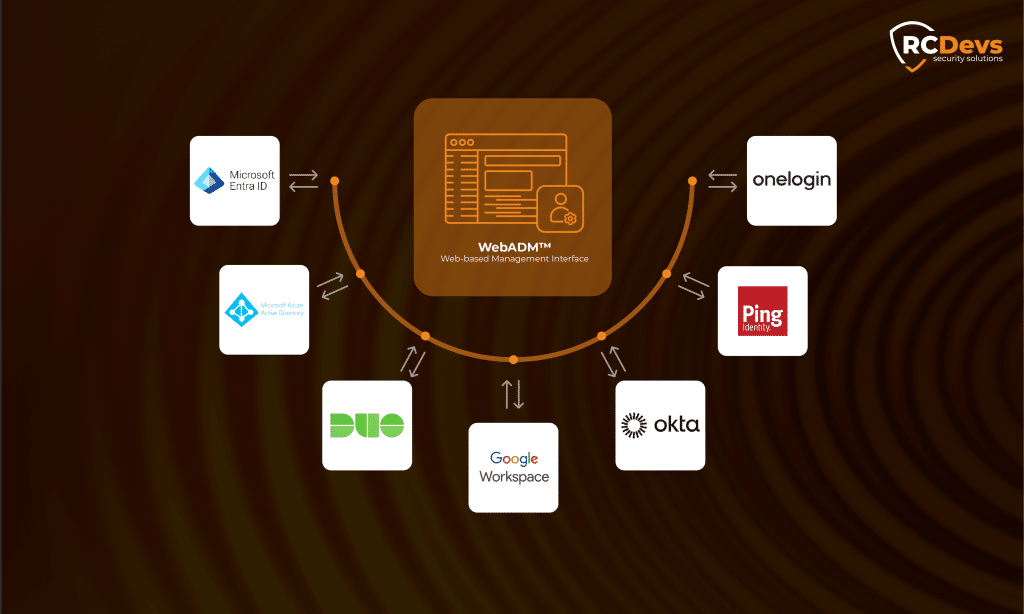
Zwei-Wege-Identitätssynchronisierung
Im Gegensatz zu vielen IAM-Lösungen, die nur einseitige Benutzerimporte anbieten, WebADM unterstützt die vollständige Synchronisierung von Verzeichnissen in beide Richtungen. Mit dieser Funktion können in WebADM vorgenommene Aktualisierungen (z. B. Benutzer-Metadaten, MFA-Zuweisungen oder Gruppenmitgliedschaften) übernommen werden. an vorgelagerte Identitätsanbieter zurückgeschriebenwenn unterstützt.
Wesentliche Merkmale:
- Synchronisierung in Echtzeit oder nach Zeitplan um aktuelle Identitätsdaten zu gewährleisten
- LDAP(S) und native API-Unterstützung (Google Directory API, MS Graph API, Okta API usw.)
- Attributabbildung und -umwandlung für Schemakompatibilität
- Unterstützung von Delta Sync zur Leistungsoptimierung
- Einheitliche Verzeichnisansicht über die Abstraktion von Verzeichnislinks
Synchronisierung von Benutzern und Gruppen
WebADM ermöglicht die Synchronisierung von Benutzern und Gruppen über Verzeichnisse hinweg in beide Richtungen:
- Importieren Sie Benutzer und Gruppen aus Cloud-IAMs in das LDAP-Verzeichnis von WebADM (RCDevs Directory oder OpenLDAP)
- Spiegeln von Änderungen, die in WebADM vorgenommen wurden, zurück in das ursprüngliche Cloud-Verzeichnis, sofern zulässig
- Aufrechterhaltung eines einheitlichen Identitätsstatus über alle Plattformen hinweg
- Aktivieren Sie Sicherung und Wiederherstellung von Cloud-IAM-Benutzern über lokale LDAP-Snapshots
Diese bidirektionale Synchronisierung gewährleistet die Geschäftskontinuität im Falle eines Ausfalls des Cloud-Dienstes und vereinfacht die Verwaltung des Benutzerlebenszyklus.
Verzeichnisübergreifende Identitätsföderation
WebADM unterstützt Identitätsföderation über mehrere Verzeichnisquellen hinwegund ermöglicht den Administratoren Kopieren oder Bereitstellen von Benutzern aus einer Quelle in eine andere-zum Beispiel die Migration eines Benutzers von Microsoft AD zu Google Workspace oder umgekehrt.
Mit dieser Cross-Provisioning-Funktion können Sie:
- Konten über Verzeichnisse hinweg verbreiten
- Gruppenmitgliedschaften und MFA-Konfigurationen beibehalten
- Einfache Migration von Benutzern zwischen Plattformen
Übertragbarkeit von MFA-Tokens
Einer der leistungsfähigsten Aspekte der WebADM-Architektur ist, dass MFA tokens sind von der zugrunde liegenden Identitätsquelle entkoppelt. Dies macht die Portabilität von token über Verzeichnisse hinweg einfach.
Vorteile:
- Token wie TOTP, Push, U2F, oder WebAuthn bleiben an das Benutzerobjekt in WebADM gebunden, unabhängig vom Quellverzeichnis.
- Bei Migrationen (z. B. von Active Directory zu Entra ID) funktioniert dasselbe token weiterhin, ohne dass eine erneute Benutzerregistrierung erforderlich ist.
- Geringere Reibung für Endnutzer bei IAM-Systemübergängen.
Anwendungsfälle aus der realen Welt
Nehmen wir an, ein Unternehmen migriert Benutzer von Active Directory vor Ort zu Microsoft Entra ID:
- Ein Benutzer wird mit einem WebADM-ausgestellten TOTP token registriert, während er noch im AD ist.
- Der Benutzer wird zu Entra ID migriert.
- WebADM aktualisiert seine internen Einträge, um die neue Verzeichnisquelle wiederzugeben.
- Der Benutzer fährt fort, sich mit demselben token zu authentifizieren, ohne dass er etwas dafür tun muss.
Dadurch werden Ausfallzeiten vermieden, die Frustration der Benutzer verringert und eine konsistente und sichere Authentifizierung gewährleistet.
Authentifizierung bei der Konsolidierung von Identitätsanbietern
Ein Unternehmen konsolidiert mehrere Identitätsanbieter (IdPs) in einem einzigen, zentralisierten Microsoft Entra ID-Tenant:
- Ein Benutzer authentifiziert sich ursprünglich über einen SAML-basierten IdP, der in WebADM integriert ist. Die Organisation wechselt zu Microsoft Entra ID als einzigem Identitätsanbieter.
- WebADM wird so umkonfiguriert, dass es zur Benutzerauthentifizierung und für Verzeichnisabfragen auf Entra ID verweist.
- Das von WebADM ausgegebene U2F/FIDO2-Hardware token bleibt mit der Identität des Benutzers verknüpft, der sich nach dem Wechsel weiterhin mit seinem token authentifiziert - eine erneute Registrierung oder Benutzeraktion ist nicht erforderlich.
Dieser Ansatz gewährleistet einen reibungslosen Übergang, bewahrt die starke Authentifizierung und vermeidet eine Überlastung des Helpdesks bei groß angelegten Identitätsumwandlungen.
Aufrechterhaltung des mobilen MFA-Zugriffs bei der Migration von Mitarbeitern im Gesundheitswesen
Ein großer Gesundheitsdienstleister stellt sein klinisches und administratives Personal von einem alten LDAP-Verzeichnis auf Microsoft Entra ID um:
- Mitarbeiter, die sich zuvor mit der mobilen Push-basierten MFA-App von WebADM (z. B. OpenOTP Token) an kritischen Systemen authentifiziert haben.
- Während des Übergangs werden die Benutzeridentitäten zu Entra ID migriert, und WebADM aktualisiert seine Benutzerverzeichnisverbindung entsprechend.
- Da das mobile token sicher an die Identität des Benutzers gebunden ist, ist keine erneute Registrierung erforderlich.
- Die Mitarbeiter können sich mit demselben mobilen Push-Gerät token unterbrechungsfrei in elektronische Patientendatensysteme (EHR) und andere sensible Plattformen einloggen.
Dadurch wird die Kontinuität der Pflege sichergestellt, Ausfallzeiten bei der Authentifizierung während der Stoßzeiten im Krankenhaus vermieden und die Einhaltung von Sicherheitsstandards im Gesundheitswesen wie HIPAA gewährleistet.
Erweiterte Sync Engine-Funktionen
Die Synchronisations-Engine von WebADM umfasst:
- Benutzerdefinierte Sync-Anbieterund ermöglicht die Integration mit SQL-Datenbanken oder maßgeschneiderten Cloud-Diensten
- Unterstützung von Delta Sync um vollständige Datenreimporte zu vermeiden
- Ereignisgesteuerte Auslöser (z. B. Anlegen und Löschen von Benutzern oder Zuweisung von Gruppen)
- Einheitliche Durchsetzung von Richtlinien über logisch gruppierte Verzeichnisse
Mit der bidirektionalen Verzeichnissynchronisierung von WebADM erhalten Unternehmen die volle Kontrolle über Identität und Authentifizierung in Cloud- und On-Premise-Umgebungen, ohne die Benutzerfreundlichkeit oder Sicherheit zu beeinträchtigen. Diese Funktion vereinfacht nicht nur komplexe IAM-Vorgänge, sondern versetzt IT-Teams auch in die Lage, Benutzer, Gruppen und MFA mit unübertroffener Flexibilität, Ausfallsicherheit und Vertrauen in jedem Infrastrukturszenario zu verwalten.

