
Höherer Standard für PAM: Benutzerzugriffsgenehmigungen
Die Messlatte für PAM höher legen: Benutzerzugriffsgenehmigungen
Mit OpenOTP / WebADM können Sie jetzt Folgendes verlangen Zulassungen bevor Benutzer auf sensible Systeme zugreifen können. Sie können Genehmigungsberechtigte pro Anwendungsrichtlinie definieren, festlegen, wie viele Genehmigungen erforderlich sind, Genehmigungszeitfenster festlegen, Genehmigungen einmalig oder an die IP eines Benutzers binden und bestimmte Benutzer ausschließen (in eine Liste aufnehmen). Genehmigungen können automatisch erzwungen oder an Bedingungen geknüpft werden (z. B. ungewöhnliches Land, nicht in einer bestimmten LDAP-Gruppe). Mit E-Mail-Benachrichtigungen bleiben alle Beteiligten auf dem Laufenden. Kombiniert mit OpenOTP Netzwerkzugang (NAC)Sie können sogar Genehmigungen für neue MAC-Adressen verlangen, die Ihrem Netzwerk beitreten. Oh, und WebADM-Richtlinien können jetzt E-Mail-Benachrichtigungen bei Zugriff auslösen und sogar Benutzerzustimmungen oder Unterschriften sammeln.
Warum Zulassungen für PAM?
Das Privileged Access Management (PAM) stützt sich seit langem auf MFA, zeitgebundene Konten und rollenbasierte Kontrollen. Hochwertige Ziele - SSH, Verwaltungskonsolen, VPN-Zugangspunkte - benötigen jedoch immer noch einen Kontrollpunkt, der von Menschen bedient werden kann, wenn das Risiko ansteigt. Das ist es, was Benutzerzugang Genehmigungen bringt OpenOTP / WebADM: eine einfache, überprüfbare, richtliniengesteuerte Möglichkeit, eine Sitzung anzuhalten und zu überprüfen, bevor sie durchgelassen wird.
Betrachten Sie es als just-in-time, just-enough Zugang mit einem zusätzlichen Gehirn.
Was ist neu: Genehmigungen, je nach Politik
Genehmigungen werden konfiguriert per Anwendungsrichtlinie im WebADM. Für jede Anwendung (SSH, VPN, Admin-Portal, etc.) können Sie angeben:
- Anzahl der Genehmigenden: Einzelner Genehmiger oder mehrseitige Genehmigung (z. B. 2 von 3 Administratoren).
- Genehmigungszeitpunkt: Ein Gültigkeitsfenster (z. B. 30 Minuten, 4 Stunden). Nach Ablauf der Gültigkeit ist die Genehmigung nicht mehr gültig.
- Einmalige Genehmigungen: Kennzeichnen Sie Genehmigungen als einmalig verbrauchbar; jeder neue Zugriff erfordert eine neue Genehmigung.
- IP-Genehmigungen pro Benutzer: Binden Sie die Genehmigung an die Quell-IP des Benutzers. Wenn sich die IP ändert, gilt die Genehmigung nicht mehr.
- Erlaubnisliste für Benutzer (auch Whitelisting genannt): Nehmen Sie wohlverstandene Konten von der Genehmigungspflicht aus, während Sie die Richtlinie für andere beibehalten.
Beispielszenarien
- Produktion SSH erfordert Verwaltungsgenehmigungen.
- VPN bedarf der Genehmigung außerhalb der offiziellen Arbeitszeiten.
- Verwaltungskonsole für Anwendungen erfordert eine Freigabe durch den Manager für eskalierte Aufgaben.

Bedingte Durchsetzung: Genehmigungen, wenn das Risiko ungewöhnlich ist
Genehmigungen müssen nicht "immer eingeschaltet" sein. Sie können schalten Sie sie nur ein, wenn etwas ungewöhnlich aussieht. Zum Beispiel, lassen Sie die Politik zu verlangen:
- Die Mitgliedschaft in einer bestimmte LDAP-Gruppe (z.B. prod-ops)
- Herkunft aus erlaubten Ländern oder Unternehmens-IP-Bereiche
Wenn eine Anfrage erfüllt nicht diese Bedingungen - z. B. dass der Benutzer nicht in der richtigen Gruppe ist oder aus einem unerwarteten Land kommt - wird WebADM eine Genehmigung auslösen anstatt stillschweigend zu blockieren oder automatisch zuzulassen. Dies hält die Reibung für den normalen, regelkonformen Zugriff gering, während Anhebung der Messlatte für ungewöhnliche Muster.
Kurz gesagt: Genehmigungen können sein automatisch oder Bedingt-Ihre Entscheidung.
End-to-End-Flow: was der Benutzer und der Genehmiger sehen
- Benutzer beantragt Zugang zu einer geschützten Anwendung (SSH, VPN, Admin UI).
- Bewertung der Politik läuft: Tageszeit, Gruppenzugehörigkeit, Geo/IP, Gerätestatus (falls zutreffend).
- Wenn die Politik es verlangt, die Genehmigung wird beantragt.
- Genehmigende erhalten eine E-Mail mit den Einzelheiten der Anfrage und den Links zu den Aktionen.
- Benutzer erhält eine E-Mail die Bestätigung, dass die Genehmigung noch aussteht.
- Genehmigende(r) genehmigen oder lehnen ab. Wenn ein Mehrfachgenehmigungsverfahren konfiguriert ist, muss der erforderliche Schwellenwert eingehalten werden.
- Benutzer wird benachrichtigt des Ergebnisses (genehmigt oder abgelehnt). Bei Genehmigung kann der Benutzer innerhalb der angegebenen Genehmigungszeitfenster. Ist die Genehmigung einmalig oder IP-gebunden, wird sie entsprechend verbraucht.
Alles ist angemeldet. für die Prüfung: wer beantragte, wer genehmigte, wann, woher und warum (falls vorhanden).
Politische Optionen auf einen Blick
- Liste der Genehmigenden pro Antrag - Legen Sie flexibel Genehmigende fest (Administratoren, Manager, Bereitschaftsdienste).
- Quorum - 1 von N, 2 von N, usw.
- TTL (Genehmigungszeit) - Kontrollieren Sie, wie lange die Genehmigung gültig bleibt.
- Einmalig vs. wiederverwendbar - Wählen Sie, ob Genehmigungen bei der ersten Verwendung verbraucht werden sollen.
- IP-gebunden - Binden Sie die Genehmigung an die Quell-IP für die Sitzungsintegrität.
- Erlaubnisliste - Umgehung von Genehmigungen für bestimmte Benutzer oder Dienstkonten.
- Bedingte Auslöser - LDAP-Gruppenprüfungen, Länder-/Regionenfilter, Geschäftszeiten und mehr.
- E-Mail-Benachrichtigungen - Automatische E-Mails an Antragsteller und Genehmigende sorgen für Transparenz.
Beispiele für politische Ideen
1) Produktions-SSH: "Zwei-Personen-Regel"
- Auslöser: Jeder SSH-Zugang zu prod-Hosts.
- Genehmiger: SRE auf Abruf + Plattformleitung; Quorum: 2 von 2.
- TTL: 1 Stunde; einmalig: aktiviert; IP-gebunden: aktiviert.
- Erlaubnisliste: Keine.
2) VPN: Kontrolle nach Geschäftsschluss
- Auslöser: Zugang außerhalb von 08:00-18:00 Uhr Ortszeit.
- Genehmiger: Sicherheitsbeauftragter; Quorum: 1 von 1.
- TTL: 4-8 Stunden; einmalig: aktiviert.
- Bedingt: Keine Genehmigung während der Geschäftszeiten, wenn MFA + Mitarbeiter LDAP-Gruppe.
3) Verwaltungskonsole: Manager-Bestätigung
- Auslöser: Beantragt die Administratorrolle in der Anwendung.
- Genehmiger: Teamleiter; Quorum: 1 von 1.
- TTL2 Stunden.
- Erlaubnisliste: Leiter der Plattform.
OpenOTP NAC Integration: Freigaben für neue MAC Adressen
Wenn Sie OpenOTP verbinden Netzwerkzugriffskontrolle (NAC)können Sie die Genehmigungen auf den Netzrand:
- Neue MAC-Adresse erscheint in einem geschützten Segment.
- WebADM/OpenOTP stellt einen Antrag auf Genehmigung an bestimmte Netzwerkadministratoren.
- Nach der Genehmigung ist der MAC autorisiertund das Gerät kann fortfahren.
Dies reduziert das Hin und Her mit Ticketsystemen und macht es ganz einfach um Ihre NAC-Infrastruktur sauber zu halten, ohne die Kontrolle zu verlieren.
Leistungen
- Schnelleres Onboarding für neue Geräte mit einem auditierbaren Pfad.
- Stärkere Kontrolle darüber, was Ihr Netz tatsächlich erreicht.
- Einheitliches Genehmigungsmodell für den Anwendungs- und Netzzugang.
E-Mail-Benachrichtigungen, Zustimmung und Unterschriften
Zwei weitere Verbesserungen auf Policy-Ebene:
- E-Mail-Benachrichtigungen bei Zugriff - WebADM-Richtlinien können jetzt E-Mail-Benachrichtigungen bei jedem Zugriff eines Benutzers eine Zielanwendung. Dies ist ideal für sensible Anwendungen, bei denen Sichtbarkeit wichtig ist, auch wenn keine Genehmigungen erforderlich sind.
- Zustimmung und Unterschrift des Benutzers - Sie können einbetten Zustimmungsaufforderungen und erfordern sogar eine Benutzerunterschrift als Teil der Zugangsrichtlinie. Denken Sie an die Bestätigung eines Produktionsänderungsfensters, die Zustimmung zu einer Datenverarbeitungsrichtlinie oder das Akzeptieren einer Einschränkung des Wartungsmodus.
Gemeinsam stärken diese Merkmale Rechenschaftspflicht und Rückverfolgbarkeitohne dass Sie gezwungen sind, externe Formulare oder spröde Workflows zusammenzukleben.
Betriebliche Tipps
- Rotationen der Genehmiger definieren: Wenn Sie einen Bereitschaftsdienst haben, machen Sie diese Gruppe zu einer Genehmigungsgruppe, damit die Abdeckung kontinuierlich ist.
- Zuerst bedingte Genehmigungen verwenden: Beginnen Sie mit Kontrollen mit geringen Reibungsverlusten (nach Geschäftsschluss, außerhalb der Länderliste, nicht in der LDAP-Gruppe), bevor Sie Genehmigungen für jeden Zugang einrichten.
- Bevorzugt einmalig + IP-gebunden für risikoreiche Aktionen: Sie schränkt die Wiederverwendung ein und beschränkt die Genehmigung auf die genaue Sitzung.
- Sparsam zulassen: Halten Sie die Ausnahmeliste kurz und übersichtlich. Nur Servicekonten und streng geprüfte Leads.
- Benachrichtigungsvolumen überwachen: Zu viele Emails = ignorierte Emails. Stimmen Sie die Bedingungen ab, damit die Signale sinnvoll bleiben.
Was dies für Ihre Sicherheitslage bedeutet
- Aufgabentrennung: Wenn ein weiterer Mensch abzeichnen muss, verringert sich das Risiko eines einzelnen Akteurs.
- Adaptive Reibung: Normaler, richtlinienkonformer Zugang bleibt unproblematisch; ungewöhnlicher Zugang wird strenger geprüft.
- Prüfbarkeit: Genehmigungen, Ablehnungen, Fenster, IP-Bindungen und Benachrichtigungen schaffen einen detaillierten Überblick.
- Konsistenz: Der Anwendungszugriff und der Netzwerkzugriff (über NAC) haben jetzt dieselbe Genehmigungsgrundlage.
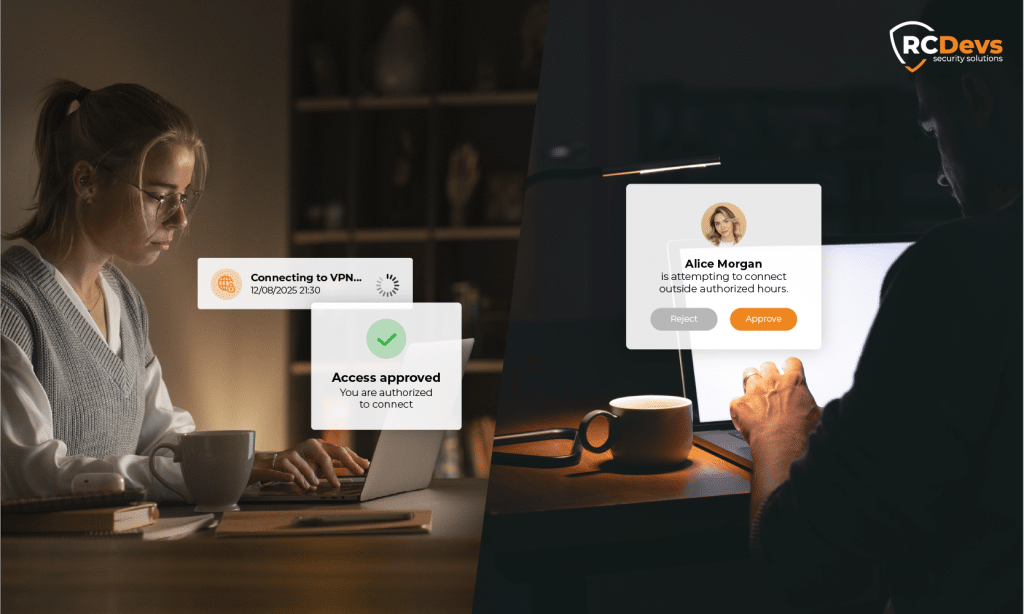
Beispiel einer Benutzerreise: VPN außerhalb der Arbeitszeiten
- Alice versucht, sich um 21:30 Uhr über VPN anzumelden.
- WebADM sieht es so außerhalb der Geschäftszeiten → Genehmigung erforderlich.
- Der Sicherheitsbeauftragte erhält eine E-Mail mit den Einzelheiten der Anfrage und dem Genehmigen/Ablehnen Aktion.
- Der Beamte stimmt zu; WebADM erfasst das Ereignis.
- Alice erhält eine erteilte Genehmigung E-Mail und können sich innerhalb der 30-minütige TTL.
- Wenn Alice die Verbindung trennt und nach der TTL wieder aufnimmt, benötigt sie eine weitere Genehmigung (da es sich einmalig).
Häufig gestellte Fragen
F: Ersetzt die Zulassung die MFA?
A: Nr. Zulassungen ergänzen MFA. Lassen Sie MFA aktiviert; verwenden Sie Genehmigungen als zusätzlichen, von Menschen geprüften Schritt für privilegierten oder ungewöhnlichen Zugriff.
F: Kann ich Genehmigungen je nach App an verschiedene Genehmiger weiterleiten?
A: Ja, Genehmigungslisten sind per Anwendungsrichtlinie. VPN kann zu Sicherheit, SSH zu SRE und App-Admin zu Managern gehören.
F: Was ist, wenn die Genehmiger das Zeitfenster verpassen?
A: Das TTL wird automatisch geschlossen. Die Anfrage läuft ab, und der Benutzer kann sie erneut stellen, falls sie noch benötigt wird.
F: Können Genehmigungen an die IP des Nutzers gebunden werden?
A: Ja, aktivieren IP-Zulassung pro Benutzer um die Autorisierung an die Herkunfts-IP zu binden.
F: Kann ich die Genehmigungen für einige Benutzer umgehen?
A: Ja, verwenden Sie Benutzer-Zulassungsliste für bestimmte Konten, die keiner Genehmigung bedürfen.
Erste Schritte
- Aktualisieren Sie auf den neuesten OpenOTP / WebADM-Build, der Folgendes enthält Benutzerzugang Genehmigungen.
- Identifizieren Sie die Zielanwendungen und gruppieren Sie sie nach Risiko und Empfindlichkeit.
- Entwurf von Politiken mit:
- Zustimmende Personen und Quorum,
- Genehmigung TTL, einmalig und/oder IP-gebunden,
- Bedingte Auslöser (LDAP-Gruppen, Länder, Geschäftszeiten),
- Benachrichtigungseinstellungen,
- Liste zulassen (falls unbedingt erforderlich).
- Beginnen Sie mit einem risikoarmen Pilotprojekt (z.B., VPN nach Geschäftsschluss), messen Sie die Auswirkungen und erweitern Sie dann auf SSH- und Verwaltungskonsolen in der Produktion.
Genehmigungen ermöglichen privilegierten Zugang messbar sicherer ohne die Teams in Tickets zu ertränken. Wenn Sie bereits mit OpenOTP / WebADM arbeiten, ist die Aktivierung nur ein kurzer Schritt mit großem Nutzen. Und mit der NAC-Integration können Sie die gleichen, vernünftigen Kontrollen auf den Netzwerkrand ausweiten.
Nächster Punkt: Führen Sie bedingte Genehmigungen ein, aktivieren Sie Zugriffsbenachrichtigungen für sensible Anwendungen und fügen Sie Zustimmungen/Unterschriften hinzu, wenn die Anerkennung von Richtlinien wichtig ist.

