
Mehr Sicherheit durch OpenOTP Token
Mehr Sicherheit in OpenOTP Token
Angreifer haben neue Möglichkeiten entwickelt, die Push-basierte Authentifizierung zu missbrauchen. Techniken wie Bombardierung (Überflutung des Benutzers mit Anmeldeanfragen), Müdigkeitsanfälle (in der Hoffnung, dass der Nutzer eine Anfrage aus Verärgerung genehmigt), und zufällige Zulassungen (ein versehentliches Antippen des Bildschirms) werden immer häufiger. Bei diesen Angriffen werden eher menschliche Fehler ausgenutzt als die Verschlüsselung geknackt.
Wenn sich die Authentifizierung auf eine einfache "Genehmigen"-Taste beschränkt, können Angreifer diese Schwäche ausnutzen. Um diesen Bedrohungen zu begegnen, muss die Authentifizierung für legitime Nutzer einfach bleiben, aber auch bewusste, kontextbezogene Entscheidungen erzwingen.
Die neueste Version von OpenOTP-Token führt mehrere neue Mechanismen ein, die die Push-basierte Authentifizierung stärken und sowohl Benutzern als auch Administratoren eine genauere Kontrolle über die Anmeldesicherheit ermöglichen.

Eingebaute Sicherheitsmerkmale von OpenOTP Token
Vor diesen Aktualisierungen, OpenOTP-Token bereits mehrere Schutzschichten enthalten. Die Anwendung bietet eine Anti-Phishing-Anzeige die eine Weltkarte, die die Quelle der Anmeldeanfrage mit dem aktuellen Standort des Telefons vergleichtDadurch wird es für die Benutzer einfacher, verdächtige Aktivitäten zu erkennen. Es führt auch Geolokalisierungsanalyse zwischen der letzten erfolgreichen Anmeldung und dem neuen Versuch, wobei geprüft wird, ob die Entfernung und die Reisezeit physikalisch möglich sind.
Für die Authentifizierung selbst unterstützt OpenOTP Token Push-Benachrichtigungen für eine schnelle Genehmigung, regelmäßige einmalige Passwörter für systemübergreifende Kompatibilität und gesprochene einmalige Passwörter zur Unterstützung der freihändigen oder sehbehinderten Nutzung.
Neue Funktionen in OpenOTP Token
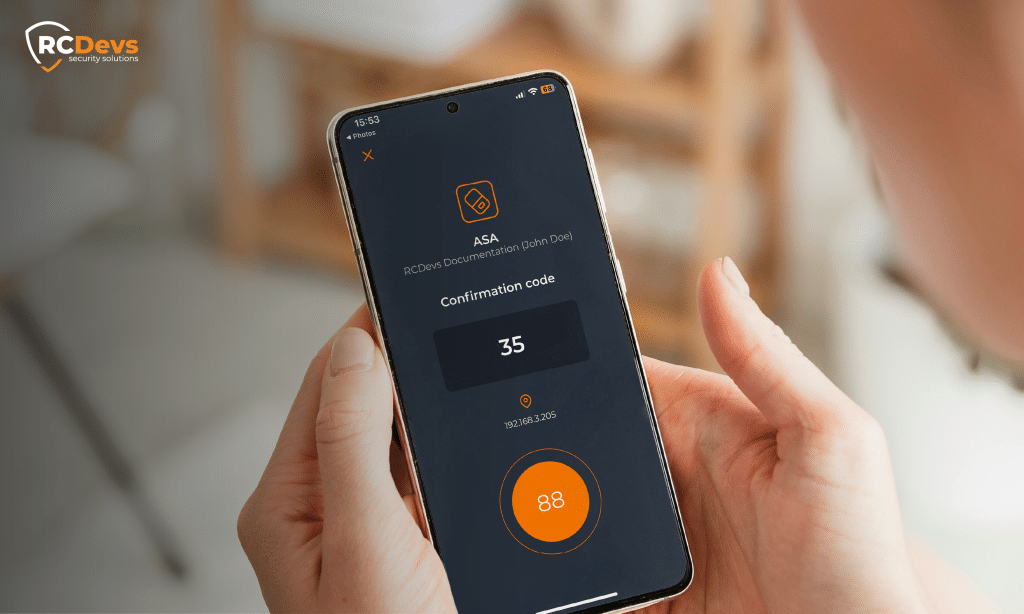
1. Bestätigungscode
Bei der Genehmigung einer Push-Anforderung wird der Benutzer nun aufgefordert, eine kurze Bestätigungscode (2 bis 4 Ziffern), der auf dem Anmeldebildschirm angezeigt wird. Die Authentifizierung wird nur abgeschlossen, wenn derselbe Code in der mobilen Anwendung eingegeben wird.
Dadurch wird sichergestellt, dass der Benutzer, der die Anfrage genehmigt, physisch bei der Anmeldesitzung anwesend ist und versehentliche Genehmigungen verhindert werden. Administratoren können auch die Funktion Bestätigungscode für alle AuthentifizierungenDiese Schutzmaßnahme gilt überall.
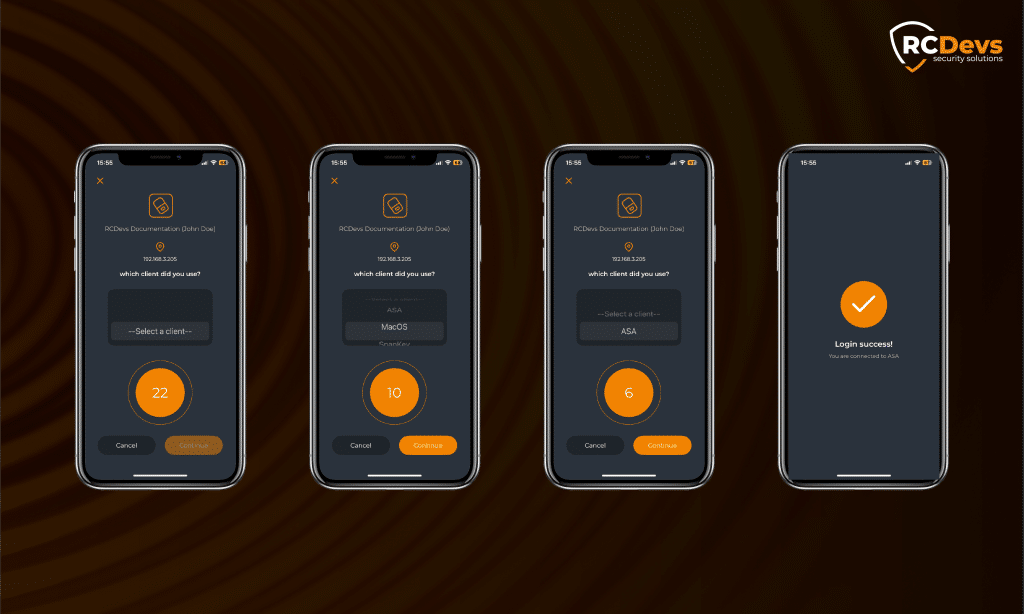
2. Auswahl der Kundenpolitik
Mit Auswahl der Kundenpolitikmüssen die Benutzer nun explizit die Option System oder Dienstleistung bei dem sie sich anmelden, wenn sie eine Push-Benachrichtigung erhalten. Zum Beispiel kann die mobile Anwendung Folgendes präsentieren drei Möglichkeiten wie zum Beispiel Windows-Anmeldung, macOS-Anmeldung, oder VPN.
Der Benutzer muss das richtige System auswählen, das seinem Anmeldeversuch entspricht. Wenn die falsche Option gewählt wird, schlägt die Authentifizierung fehl.
Dies verhindert, dass Angreifer blinde Genehmigungen missbrauchen und zwingt den Benutzer, den genauen Kontext der Anmeldung zu bestätigen.
3. Strategien gegen einfache Push-Risiken
Push-Benachrichtigungen sind praktisch, können aber auch missbraucht werden, wenn sie zu einfach sind. OpenOTP enthält jetzt mehrere Strategien, um sie zu stärken:
- Simple Push deaktivieren: Sie können die Einfaches Drücken Funktion über WebADM-Client-Richtlinien und erzwingen einen auf Herausforderungen basierenden Authentifizierungsprozess. Dadurch wird sichergestellt, dass der Benutzer die Anmeldung nicht genehmigen kann, selbst wenn ein Angreifer Zugriff auf die Anmeldedaten des Benutzers erhält. Stattdessen erhält der Benutzer eine Push-Benachrichtigung mit einem angezeigten OTP, das in der Client-Anwendung eingegeben werden muss.
- Aktivieren Sie die Bestätigungscode-Methode: Wenn Sie diese Methode aktivieren, wird in der mobilen App ein Code angezeigt, nachdem der Benutzer die Anmeldung bestätigt hat. Der Benutzer muss dann den Code in die OTP-Abfrage in der Client-Anwendung eingeben, was eine zusätzliche Sicherheitsebene darstellt. Dies kann global unter OpenOTP oder per Client-Richtlinie konfiguriert werden.
- Aktivieren Sie die Eingabeaufforderung für Richtlinien: Wenn diese Option aktiviert ist, werden bei der Anmeldeanfrage drei Richtlinien angezeigt. Der Benutzer muss diejenige auswählen, die dem System entspricht, bei dem er sich anmeldet. Für diese Funktion müssen mindestens drei Client Policies auf dem WebADM-Server konfiguriert werden. Die Richtlinien werden auf der Grundlage der "Friendly Name"-Einstellung der Client-Richtlinie angezeigt.
Zusammengenommen machen diese Schritte die Push-Authentifizierung durchdachter und viel schwieriger auszunutzen.
4. Zusätzliche Sicherheitsverbesserungen
Es wurden zwei zusätzliche Schutzmaßnahmen hinzugefügt:
Obligatorisches Badging für öffentliche Systeme
- Mit dieser Funktion wird ein orts- und gerätebezogenes Badging-Verfahren das den Benutzerzugang jederzeit sperrt, es sei denn, es tritt ein Badge-In-Ereignis ein. Im Gegensatz zu einem Standard-Push ist das Badging-System integriert mit Active Directory (AD), LDAP und Netzwerkzugangskontrolle (NAC) um einen stärkeren Basisschutz zu gewährleisten.
- Die wichtigsten Aspekte sind:
- AD-Benutzerkonto standardmäßig gesperrt: Das Verzeichniskonto bleibt auf LDAP-Ebene gesperrt, bis sich der Benutzer einloggt.
- Beschränkter Netzzugang für Benutzer: Der Netzwerkzugang wird gesperrt, bis das Badging durchgeführt wurde, mit optionaler NAC-Integration.
- Politikgesteuerte Durchsetzung: Administratoren können auf Anwendungs-, Gruppen- oder Untergruppenebene ein "Badging" erzwingen und so eine fein abgestufte Kontrolle gewährleisten.
- Steuerung auf Geräteebene: Benutzergeräte bleiben gesperrt, bis ein Badge-In-Ereignis eintritt, wiederum unterstützt durch die NAC-Integration.
- Automatische Entriegelung: Ein erfolgreicher Badge-In schaltet automatisch das AD-Konto frei und gewährt Netzwerkzugang.
- Dynamische Gruppenzuweisung: Gruppen können automatisch erstellt werden, um Rechte auf Systemen wie Unix- oder Samba-Dateiservern zu vergeben.
- Standortdurchsetzung: Badge-in-Veranstaltungen können eingeschränkt werden durch geografische Zonen oder LänderDadurch wird die Angriffsfläche verringert, wenn niemand physisch vor Ort ist (z. B. nachts oder während der Ferien).
- Dieses System verlangt von den Nutzern ein "Badge", bevor die Authentifizierung überhaupt beginnen kann. reduziert das Belichtungsfenster für Angriffe wie Push-Bombing oder Credential Replay. Wenn niemand im Büro oder an einem genehmigten Standort anwesend ist, können keine Anmeldeversuche erfolgreich sein - selbst wenn Push-Benachrichtigungen berücksichtigt werden.
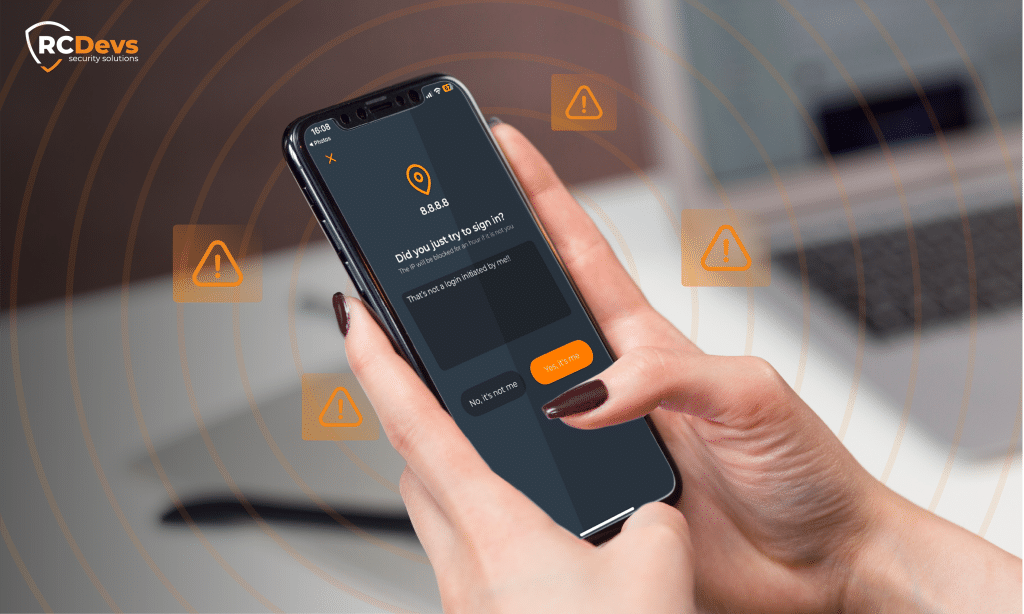
Meldung verdächtiger Logins
Wenn ein Benutzer eine Push-Anforderung erhält, die er nicht selbst initiiert hat, kann er sie zurückweisen und die Quelladresse für 60 Minuten blockieren, wobei automatisch eine Warnung für die Administratoren erzeugt wird.
Warum diese Updates wichtig sind
Diese Verbesserungen beheben direkt die Schwächen der einfachen Push-Authentifizierung:
- Versehentliche Genehmigungen werden reduziert mit Bestätigungscodes und Systemauswahl.
- Benutzer überprüfen den Kontext indem sie das System, bei dem sie sich anmelden, ausdrücklich auswählen.
- Phishing-Versuche sind leichter zu erkennen dank Karten und Geolokalisierungsprüfungen.
- Bei verdächtigem Verhalten kann sofort gehandelt werden durch Ablehnung und Blockierung von Anfragen.
- Administratoren haben Flexibilität um das richtige Gleichgewicht zwischen Benutzerfreundlichkeit und Sicherheit zu erreichen.
Die neueste Version von OpenOTP-Token macht die Push-basierte Authentifizierung bewusster und sicherer. Durch die Einführung von Bestätigungscodes, Systemauswahl und neuen Berichtsfunktionen wird sichergestellt, dass Benutzer nicht einfach unbewusst auf "Genehmigen" tippen können. In Kombination mit bestehenden Schutzmechanismen wie Anti-Phishing-Karten und Geolocation-Analyse bietet OpenOTP Token nun einen robusten und kontextbewussten Ansatz für moderne Authentifizierung.

