
Warum die Zentralisierung des Zugangs wichtig ist: Die Rolle von WebADM
Warum die Zentralisierung des Zugangs wichtig ist: Die Rolle von WebADM
Viele Unternehmen sind heute auf eine Vielzahl digitaler Systeme angewiesen, um ihre tägliche Arbeit zu erledigen. Diese Systeme stammen oft von verschiedenen Anbietern und dienen unterschiedlichen Funktionen, wie z. B. Kommunikation, Datenspeicherung und Unternehmensverwaltung. Die Koordinierung des Zugriffs über diese Systeme hinweg kann schwierig sein, da jedes System seinen eigenen Ansatz für die Benutzerauthentifizierung und -kontrolle verwendet. WebADM bietet einen zentralen Rahmen, der es Unternehmen ermöglicht, den Zugriff auf eine konsistente und organisierte Weise zu verwalten, wodurch die Notwendigkeit, separate Authentifizierungsprozesse für jedes System zu pflegen, verringert wird.
Wenn die Zugriffsverwaltung dezentralisiert bleibt, erhöht sich der Verwaltungsaufwand, es kommt zu Inkonsistenzen bei den Sicherheitsverfahren und die Übersicht über die Benutzeraktivitäten wird eingeschränkt. Mit der Zeit können diese Herausforderungen zu folgenden Problemen führen unnötiges Risiko, betriebliche Ineffizienz, und größere Schwierigkeiten bei der Erfüllung der Anforderungen.
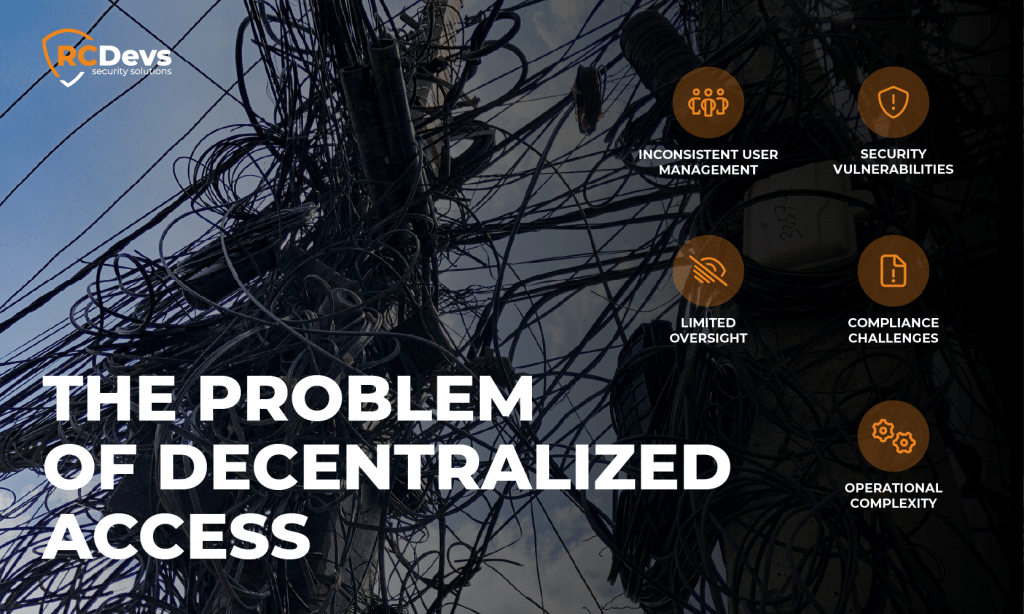
Das Problem des dezentralen Zugangs
Wenn Authentifizierung und Zugangskontrolle von jeder Anwendung oder jedem System unabhängig voneinander gehandhabt werden, ergeben sich mehrere Herausforderungen:
Inkonsistente Benutzerverwaltung
Jedes System führt oft seine eigene Liste von Benutzern und Anmeldedaten. Dies führt zur Duplizierung von Daten, zu Schwierigkeiten beim Aktualisieren oder Entfernen von Benutzern und zu einer erhöhten Fehlerwahrscheinlichkeit. Ein Benutzer, der das Unternehmen verlässt, hat möglicherweise immer noch Zugang zu einem oder mehreren Systemen, wenn die Löschung nicht konsequent durchgeführt wird.
Sicherheitsschwachstellen
Verschiedene Systeme können unterschiedliche Kennwortrichtlinien, Authentifizierungsmethoden oder Zugangsregeln durchsetzen. Ohne eine einheitliche Richtlinie können einige Systeme zu Schwachstellen in der gesamten Sicherheitsstruktur werden. Angreifer nutzen solche Unstimmigkeiten häufig aus, um sich unbefugten Zugang zu verschaffen.
Begrenzte Aufsicht
Wenn Zugriffsereignisse über viele Systeme verteilt sind, wird es schwierig, sie zu überwachen und zu überprüfen. Sicherheitsteams haben möglicherweise keinen vollständigen Überblick über alle Authentifizierungsaktivitäten. Dieser Mangel an Transparenz erschwert die Erkennung von ungewöhnlichen Zugriffen oder potenziellen Verstößen.
Compliance-Herausforderungen
Vorschriften und Normen erfordern oft genaue Aufzeichnungen über Benutzerzugriffe und -aktivitäten. Das Sammeln und Korrelieren von Daten aus mehreren Systemen nimmt viel Zeit in Anspruch und kann zu unvollständigen Berichten führen.
Operative Komplexität
Jedes neue System, das dem Unternehmen hinzugefügt wird, bringt zusätzliche Arbeit für die Administratoren mit sich. Sie müssen die Authentifizierung konfigurieren, die Benutzer verwalten und die Übereinstimmung mit den bestehenden Richtlinien sicherstellen. Mit der Zeit erhöht sich dadurch der Wartungsaufwand.
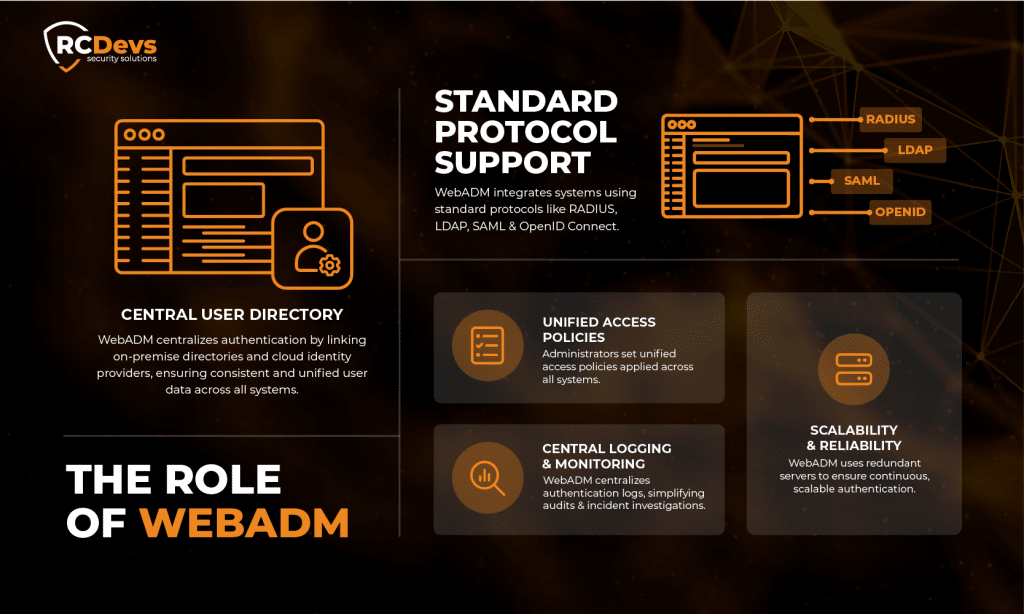
Die Rolle von WebADM
WebADM ist ein Rahmenwerk, das zentralisierte Authentifizierung und Zugangskontrolle. Es ermöglicht allen angeschlossenen Systemen, sich auf einen einzigen Verifizierungspunkt zu verlassen, anstatt getrennte Authentifizierungsprozesse zu unterhalten.
Indem WebADM als zentrale Zugriffsinstanz fungiert, kann reduziert Doppelarbeit und Inkonsistenz und gleichzeitig die Aufsicht zu verbessern.
Zentrales Benutzerverzeichnis
WebADM verbindet sich mit bestehenden Verzeichnisdienste wie LDAP oder Active Directory. Es ersetzt sie nicht, sondern bietet einen einzigen Kanal, über den die Authentifizierung abgewickelt wird. Dadurch wird sichergestellt, dass alle angeschlossenen Systeme auf dieselben Benutzerinformationen verweisen. Zusätzlich zu den Verzeichnissen vor Ort kann WebADM auch mit Cloud-Identität und Zugangsmanagement-Plattformen und Identitätsanbieter wie Entra ID, Google Workspace, Duo, Okta und Ping Identity, Dadurch können sowohl lokale als auch Cloud-basierte Systeme über einen einzigen Authentifizierungsrahmen verwaltet werden.
Unterstützung von Standardprotokollen
WebADM kommuniziert mit anderen Systemen über weit verbreitete Authentifizierungsstandards, darunter RADIUS, LDAP, SAML und OpenID Connect. Dies ermöglicht die Integration mit einer Vielzahl von Anwendungen und Infrastrukturen, ohne dass diese einzeln geändert werden müssen.
Vereinheitlichte Zugangsrichtlinien
Administratoren können Sicherheitsregeln und Zugangsvoraussetzungen festlegen an einer Stelle. Einmal definiert, gelten diese Richtlinien automatisch für alle angeschlossenen Systeme. Dies gewährleistet Konsistenz und reduziert die Möglichkeit schwacher Konfigurationen.
Zentrale Protokollierung und Überwachung
WebADM zeichnet alle Authentifizierungsanfragen und -ergebnisse auf. Sicherheits- und Compliance-Teams können diese Protokolle von einem Ort aus überprüfen, anstatt Daten von verschiedenen Systemen zu sammeln. Dies verbessert die Fähigkeit, Zugriffsaktivitäten zu prüfen und Vorfälle zu untersuchen.
Skalierbarkeit und Verlässlichkeit
WebADM unterstützt die verteilte und redundante Bereitstellung mit 2 Server für HA. Dadurch wird sichergestellt, dass die Authentifizierung auch dann verfügbar bleibt, wenn eine Komponente ausfällt, wobei eine Aktiv-Aktiv-Cluster. Je nach Infrastruktur und Bedarf des Unternehmens können weitere Server gekauft werden. Außerdem kann das System eine wachsende Zahl von Benutzern und Anfragen bewältigen, wenn das Unternehmen wächst.
Von der Fragmentierung zur zentralen Verwaltung
Der Übergang von unabhängigen Authentifizierungssystemen zu einem zentralisierten Modell bietet mehrere Vorteile.
Im Folgenden finden Sie einen einfachen Vergleich der beiden Ansätze:
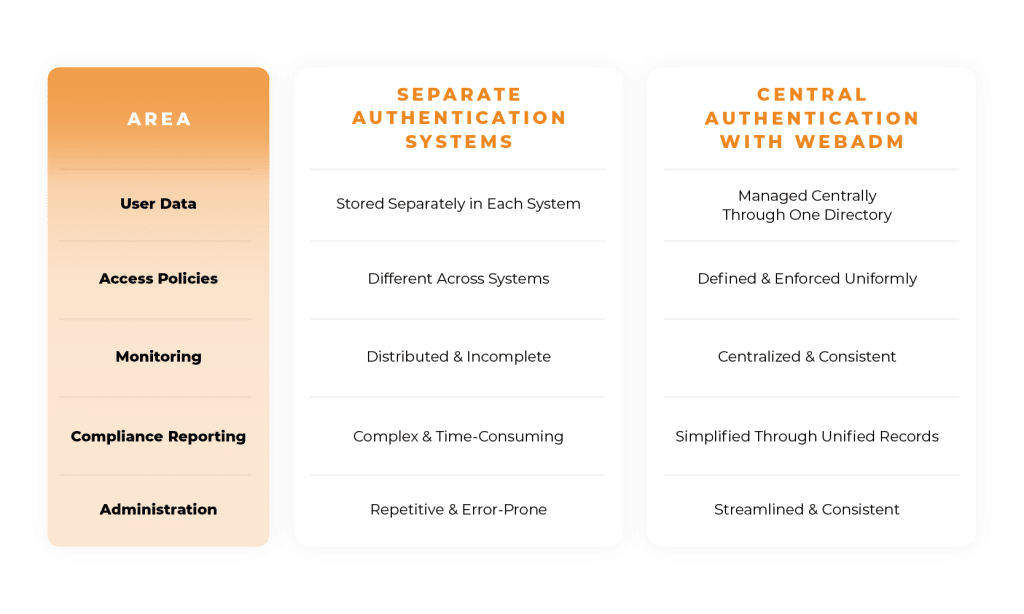
Durch die Verringerung der Fragmentierung und die Bereitstellung eines zentralen Kontrollpunkts erhalten Unternehmen eine klarere und besser verwaltbare Zugriffsstruktur.
Die Verwaltung des Zugriffs über mehrere Systeme hinweg ohne zentrale Koordination führt zu Komplexität und Risiken. Ein zentrales Authentifizierungs-Framework wie WebADM ermöglicht es Unternehmen, Zugriffsrichtlinien in ihrer gesamten Umgebung einheitlich zu definieren, zu überwachen und durchzusetzen.
Durch die Integration mit bestehenden Verzeichnissen und Standard-Authentifizierungsprotokollen, WebADM bietet eine strukturierter und transparenter Ansatz zur Verwaltung des Benutzerzugriffs. Es reduziert die Notwendigkeit, separate Tools zu pflegen, die ähnliche Funktionen ausführen, Einsparung von Zeit und Betriebskosten. Durch die Konsolidierung der Zugangsverwaltung in einem einzigen Rahmen können Unternehmen die Verwaltung vereinfachen, die Ressourceneffizienz zu verbessern und die Wahrscheinlichkeit von Sicherheitslücken zu verringern bei gleichzeitiger Einhaltung der gesetzlichen Anforderungen.

