
The Illusion of Digital Sovereignty: Why Europe Must Reclaim Control of its Identities
The Illusion of Digital Sovereignty: Why Europe Must Reclaim Control of its Identities
I. The Brutal Awakening
Throughout 2025 and into the turbulent opening months of 2026, escalating geopolitical tensions have shattered the illusion of cloud services as “neutral utilities.” The European Commission’s 2025 State of the Digital Decade report, confirmed what industry experts had been warning: Europe remains critically dependent on non-European providers across its entire digital stack.
The scale is staggering. Cristina Caffarra, founder of the Eurostack Foundation, estimates that 90 percent of Europe’s digital infrastructure, cloud, compute, and software, is now controlled by foreign companies. The Australian Strategic Policy Institute’s analysis of 64 critical technologies reveals an even starker reality: Europe leads in none. While China dominates 57 and other nations control the remainder, Europe has ceded technological leadership entirely.
As Mario Draghi warned in his landmark September 2024 report on European Competitiveness, this systemic dependence threatens not just productivity, but operational autonomy itself. Without decisive action to reclaim technological capabilities, Europe faces what Draghi described as “a slow agony” of eroding sovereignty.
The Identity Bottleneck
This deficit is most acute in Identity and Access Management (IAM). Unlike static data storage, authentication is the foundational layer of control. When the authority to authenticate your users resides in infrastructure subject to foreign legal orders, your operational continuity becomes hostage to decisions made in distant capitals. Identity is no longer just a security feature; it is a single point of failure where jurisdictional risk meets technical vulnerability.
From Regulation to Reality
Europe’s response has been swift. With the full transposition of NIS2 Directive and the application of DORA, identity management is now officially designated as critical infrastructure. These regulations mandate that Operators of Essential Services (OES) demonstrate “Offline Functional Continuity.” For energy grids, hospitals, and banks, dependence on authentication flows subject to foreign legal reach is no longer just a risk, it is a compliance failure.
The question is no longer why sovereignty is needed, but how to transform these mandates into operational reality.
II. The Regulatory Imperative Drives Action and European Initiatives Multiply
Regulatory Imperative
The implementation of the NIS2 Directive and the Digital Operational Resilience Act (DORA) has transformed digital sovereignty from political aspiration to legal obligation. These frameworks mandate that Operators of Essential Services and financial institutions demonstrate operational continuity independent of third-party dependencies, including the ability to maintain authentication capabilities during external service disruptions.
This regulatory imperative is driving concrete action across Europe. According to The Register’s December 2025 investigation into Europe’s infrastructure migrations, public authorities are moving from compliance assessments to actual architectural transformation.

European Initiatives Multiply
According to The Register’s December 2025 investigation into Europe’s infrastructure migrations, a wave of concrete action is underway. From Austria to Germany, from France to international institutions, public authorities are executing targeted migrations away from foreign-controlled infrastructure—particularly for identity and authentication systems.
Austria: Ministry Sets the Precedent
Austria’s Federal Ministry for Economy, Energy and Tourism completed a migration of 1,200 employees to Nextcloud, a European open-source collaboration platform, in just four months. The decision was not cost-driven but compliance-driven. As the ministry’s CISO Florian Zinnagl explained to The Register, “It was never about saving money. It was about maintaining control over our own data and our own systems.” Several other Austrian ministries have since begun implementing Nextcloud.
Germany: State-Level Transformation
In Schleswig-Holstein, Germany is undertaking an even more ambitious project. The state is migrating 30,000 civil servants from proprietary systems to open-source European alternatives including LibreOffice, Nextcloud, Open Xchange, and Thunderbird. As of late 2025, over 24,000 employees had completed the transition.
The project’s success has catalyzed broader European collaboration. In July 2025, Germany, France, Italy, and the Netherlands established the European Digital Infrastructure Consortium for Digital Commons to jointly develop and scale sovereign digital tools like OpenDesk, an open-source office and collaboration suite delivered by the German Centre for Digital Sovereignty (ZenDiS).
International Institutions Take Action
Even international bodies are recognizing the vulnerability of dependence on foreign infrastructure. The International Criminal Court in The Hague announced in late 2025 its migration to OpenDesk. The decision followed an incident in which the court’s chief prosecutor was temporarily unable to access critical communication systems, an operational vulnerability that became untenable for an institution operating in a politically sensitive environment.
France: Strategic Infrastructure for Sensitive Data
France’s Ministry of Economics and Finance completed NUBO, an OpenStack-based private cloud initiative designed specifically to handle sensitive data and services. Unlike general-purpose cloud migrations, NUBO represents a targeted approach: maintain control over the most critical assets while potentially consuming commodity services from external providers for less sensitive workloads.
A Grassroots Movement with Growing Momentum
These cases illustrate that while a complete break from foreign hyperscalers may be unrealistic in the short term, targeted migrations for specific, high-risk applications, particularly identity and authentication infrastructure, are not only possible but actively being pursued across Europe.
The pattern is clear: organizations are moving from rhetoric to execution, from compliance checkbox exercises to genuine architectural transformation. What began as isolated initiatives is coalescing into a continent-wide trend, driven not by political ideology but by the practical realities of operational risk, regulatory obligations, and the fundamental recognition that authentication infrastructure cannot be treated as just another commodity service.
III. RCDevs: Sovereignty through Infrastructure
European • On-premise • AD-native
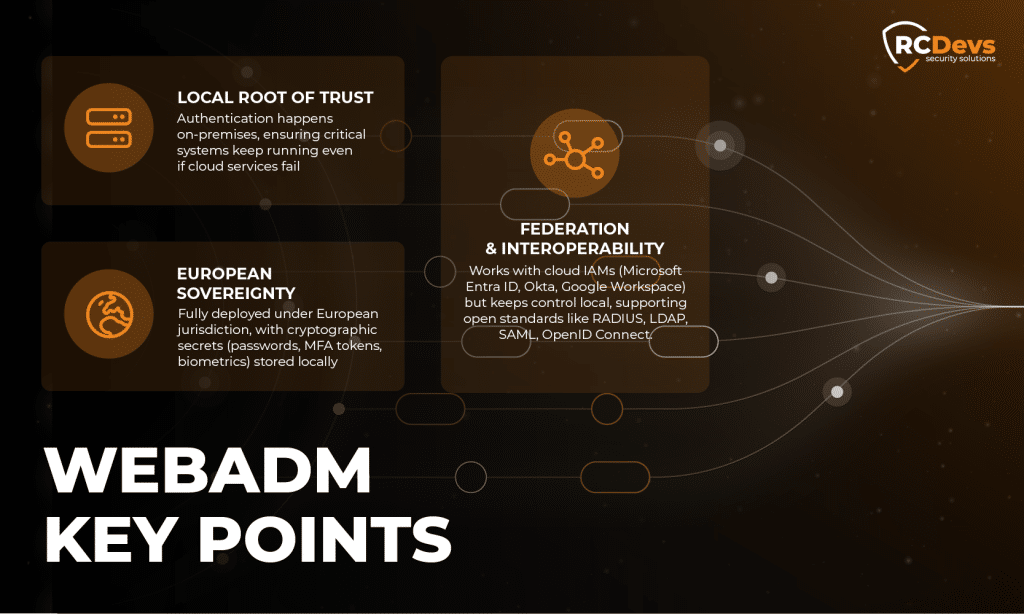
With over 15 years of expertise in identity and access management, Luxembourg-based RCDevs delivers on-premise solutions designed for European digital sovereignty. WebADM and OpenOTP integrate with existing identity infrastructure— including native Active Directory support—while ensuring that authentication authority remains under the organization’s direct control.
European Technology, architectural commitment
RCDevs has built its identity and access management solutions specifically for on-premises deployment. This isn’t just a technical choice—it’s an architectural commitment to sovereignty.
When you deploy RCDevs’ Identity hub WebADM within your organization:
European Jurisdiction, Full Control
- Authentication infrastructure runs on your servers, in your data centers, under European law
- No foreign cloud provider in the critical authentication path
- No exposure to extraterritorial legislation like the Cloud Act or FISA
- Cryptographic secrets (passwords, MFA tokens, biometric data) remain on your infrastructure, under your physical and legal control
Operational Independence from Foreign Cloud Dependencies
- Authentication decisions are made locally, not routed through foreign-controlled services
- If cloud IAMs hosted in foreign jurisdictions go offline, your critical systems continue to authenticate using local credentials
- VPN access, infrastructure login and sensitive applications operate independently of external connectivity
NIS2 and DORA Compliance by Design
- Demonstrates jurisdictional independence for Operators of Essential Services
- Provides the “offline functional continuity” required by resilience frameworks
- Maintains local “root of trust” as mandated for critical infrastructure
Hybrid Architecture without Dependency
WebADM doesn’t require you to abandon cloud IAMs overnight. It federates with Microsoft Entra ID, Okta, Google Workspace, and other cloud providers, but places the authentication authority within your perimeter.
Your users can remain in Entra ID for Microsoft 365 and SaaS applications. But when they authenticate to your VPN, your factory systems, your financial infrastructure, or your critical applications, that authentication flows through your local WebADM deployment.
The cloud IAMs become federated sources rather than controlling authorities. You consume their services where convenient, but you’re not operationally dependent on their availability or their compliance with foreign legal orders.
When External Connectivity is Severed
This architecture is designed for the scenario European decision-makers must now plan for: what happens if connectivity to foreign cloud services is disrupted, whether by cyberattack, infrastructure failure, or political decision.
With WebADM deployed on-premise:
- Your factories keep running
- Your banks continue operating
- Your hospitals maintain access to critical systems
- Your government services remain functional
Because authentication happens locally, independently of external dependencies. Security becomes a resilient European asset rather than a vulnerable foreign dependency.
IV. Operational Benefits Beyond Sovereignty
Beyond eliminating jurisdictional risk, on-premise European identity infrastructure delivers tangible operational advantages.
Resilience During Potential Cloud Provider Disruptions
When cloud IAM providers hosted in foreign jurisdictions experience outages, and they do, regularly, organizations dependent on those services for authentication are locked out.
WebADM‘s architecture ensures continuity when cloud IAM providers become unavailable. Through local password synchronization and federated identity management, organizations maintain authentication capabilities even during transatlantic connectivity failures or cloud service outages. VPN access, network authentication, and critical systems continue to operate using locally-maintained credentials and MFA flows, independently of external cloud IAM availability.
This “fail-safe” design means that factories, banks, and public services are not held hostage by the operational status of foreign cloud providers. Security becomes an independent asset rather than a vulnerable dependency.
Migration Efficiency through Token Portability
One of the hidden costs of IAM consolidation projects is MFA re-enrollment. When migrating users between identity providers, whether from on-premises AD to Entra ID, or from Okta to another platform, organizations typically face massive support costs as thousands of users must re-register their authentication tokens.
WebADM eliminates this friction through token portability. Because MFA tokens are stored and managed within WebADM’s meta-directory rather than individual IAMs, users retain their same TOTP or FIDO tokens throughout migrations. A user can be moved from AD to Entra ID, or from Okta to Google Workspace, without re-enrollment, significantly reducing user impact and helpdesk burden during large-scale IAM transformations.
European Ecosystem Interoperability
RCDevs has designed WebADM around open standards (RADIUS, LDAP, SAML, OpenID Connect), making it compatible with other European technologies that share sovereignty principles, whether Nextcloud for collaboration, European cloud providers, or other solutions built on European soil.
You’re not locked into a monolithic foreign vendor stack. You build a modular European technology foundation where components can be replaced without systemic disruption.
V. Conclusion: Securing the Cornerstone of the Enterprise
In 2026, the question for European decision-makers is simple: if connectivity to foreign cloud providers is severed tomorrow, does your organization still have the power to authenticate its users and operate its systems?
RCDevs provides the architectural foundation to ensure the answer is “Yes.” By deploying authentication infrastructure on European soil, organizations maintain operational control even while consuming cloud services globally. The authority to authenticate, and thus to grant or deny access, remains under the organization’s direct control.
True resilience is the ability to maintain operational autonomy when the continuity of your mission is at stake.

