OpenOTP Token: Free Mobile Authentication App for Push Notifications and OTPs
OpenOTP Token App
The app features Push Notifications, OTPs, Badging, E-Signing, Anti-Phishing & Biometric Protection. Designed for iOS & Android
Why our software token?
OpenOTP Token App Features
Token Enrollment
Simple, secure & convenient
OpenOTP Token app offers simple and secure ways to enroll your tokens. Using the camera feature in the app, you can easily scan QR codes. A scanned and registered QR Code is no longer “active” and cannot be used again. Additional security settings are available.
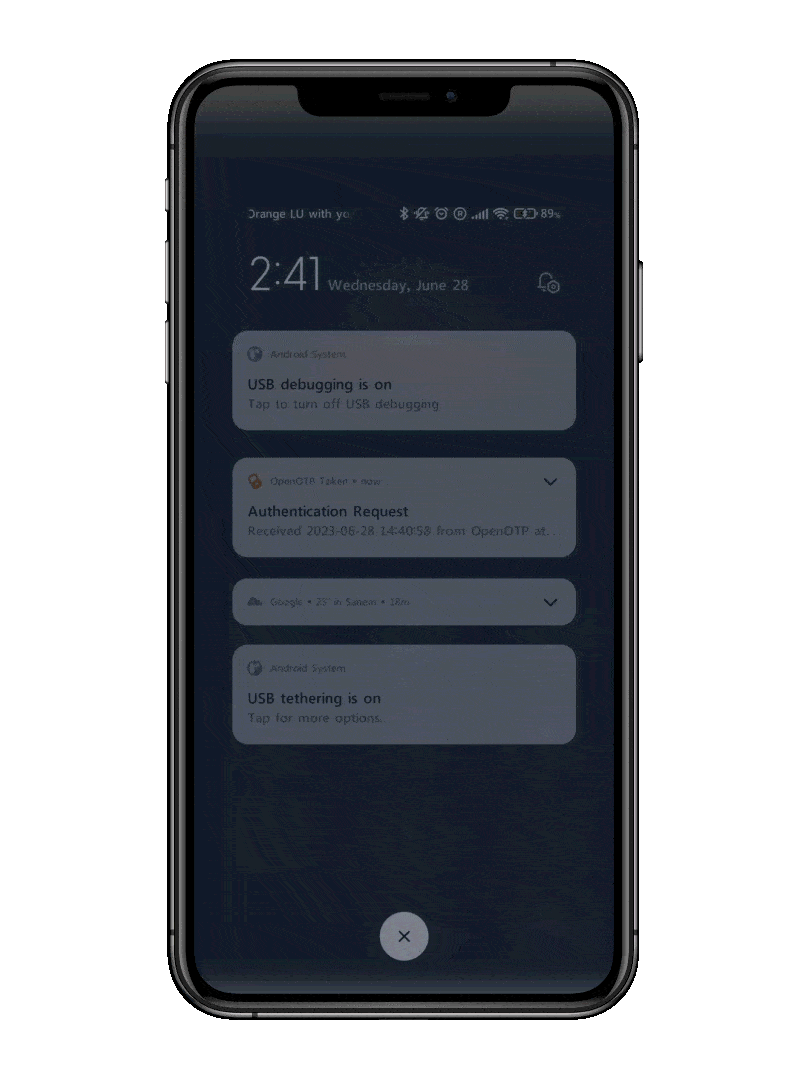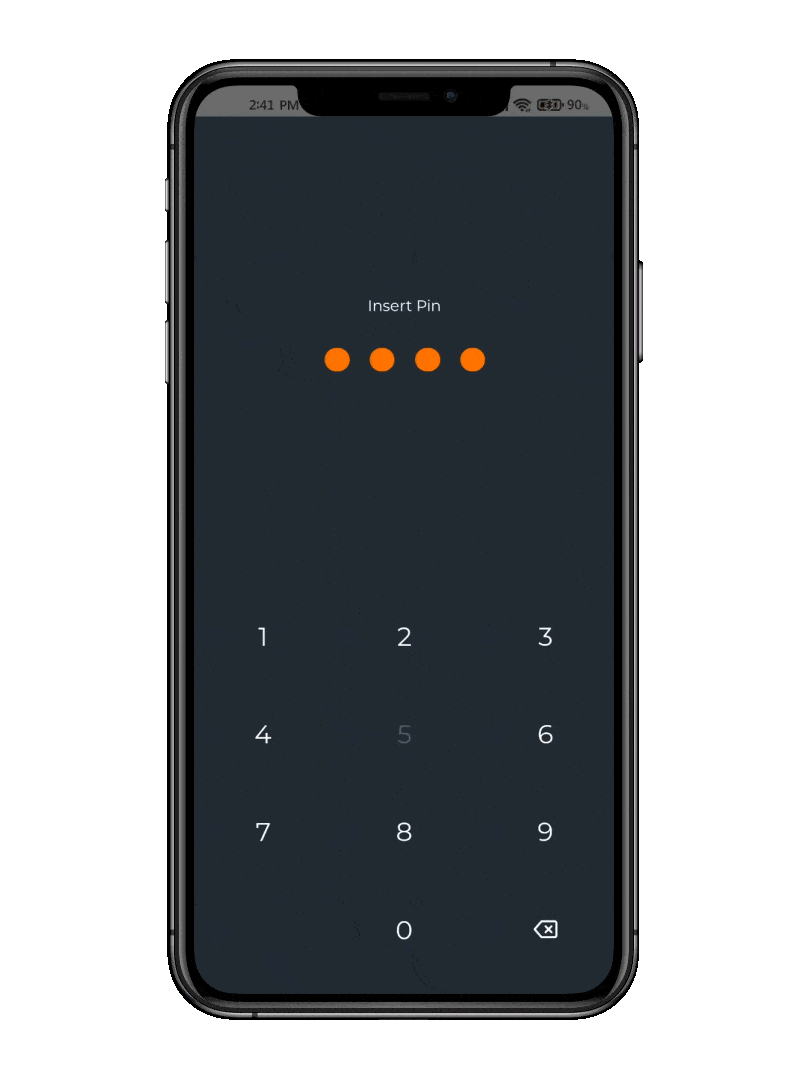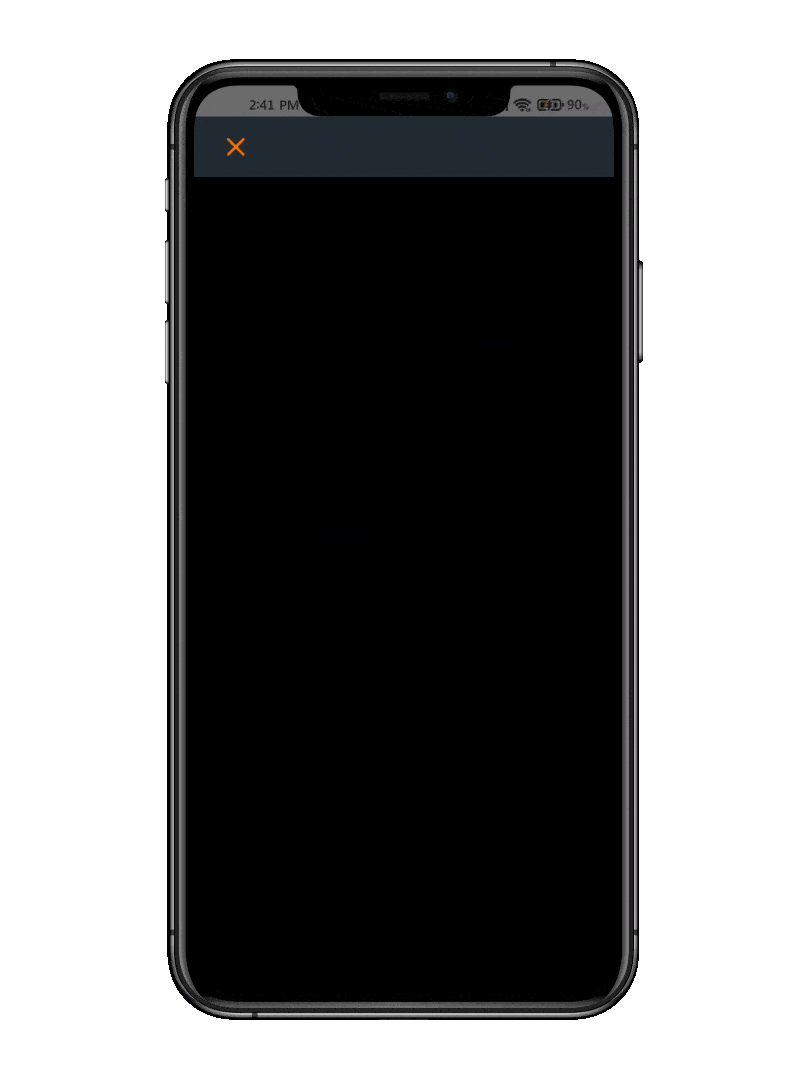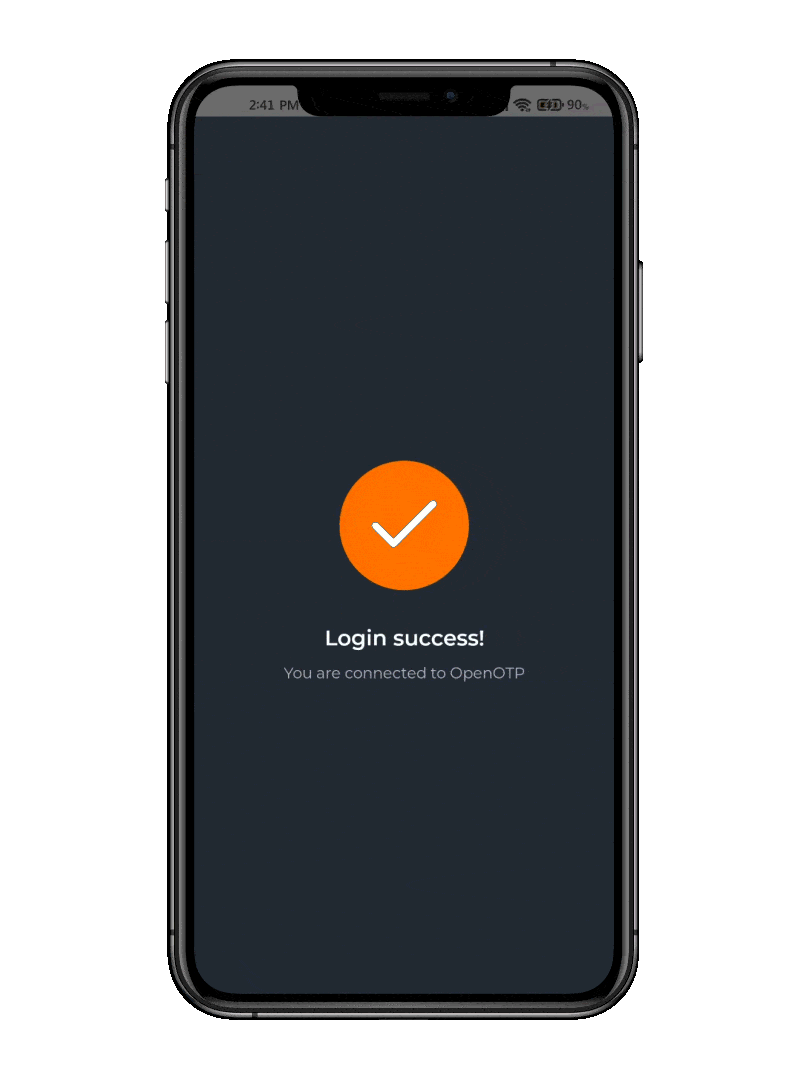
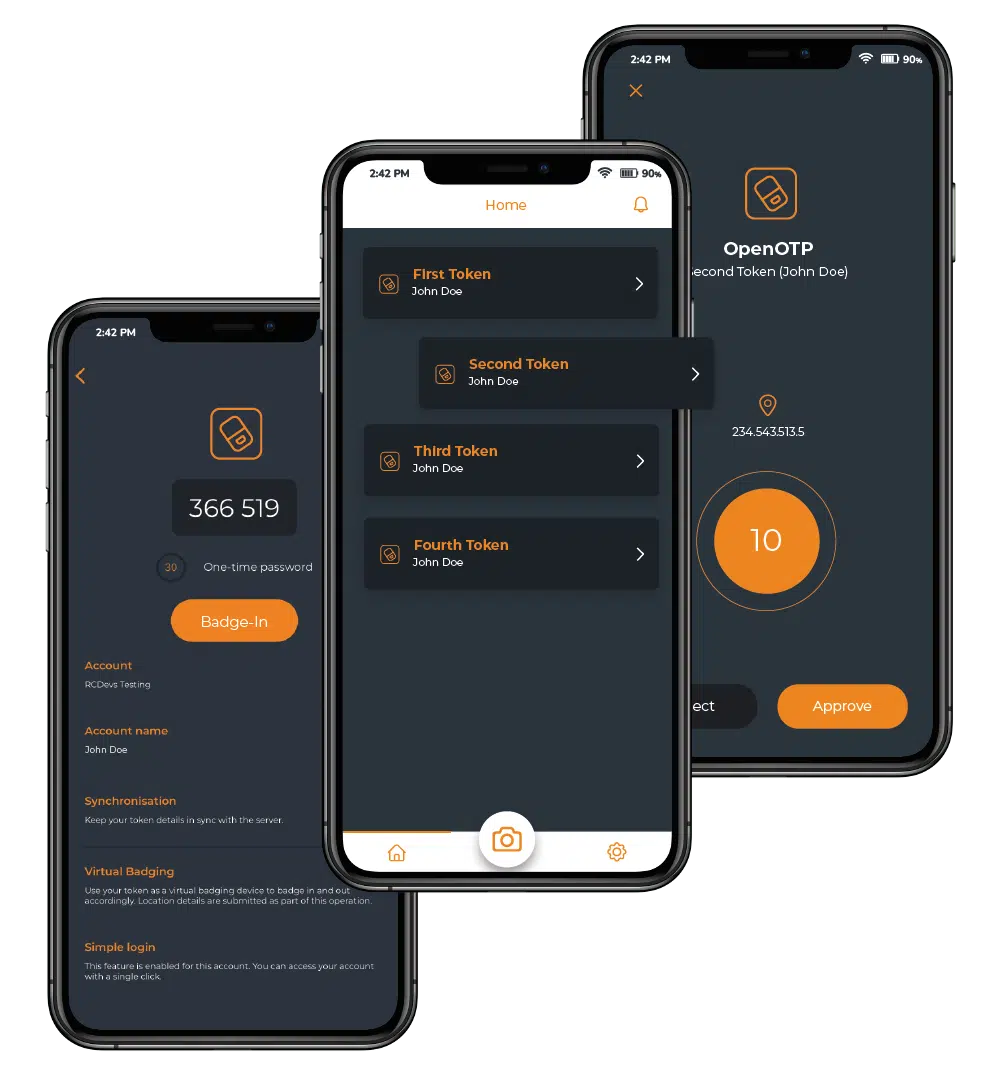
Push Notifications
User-friendly feature combined with additional security
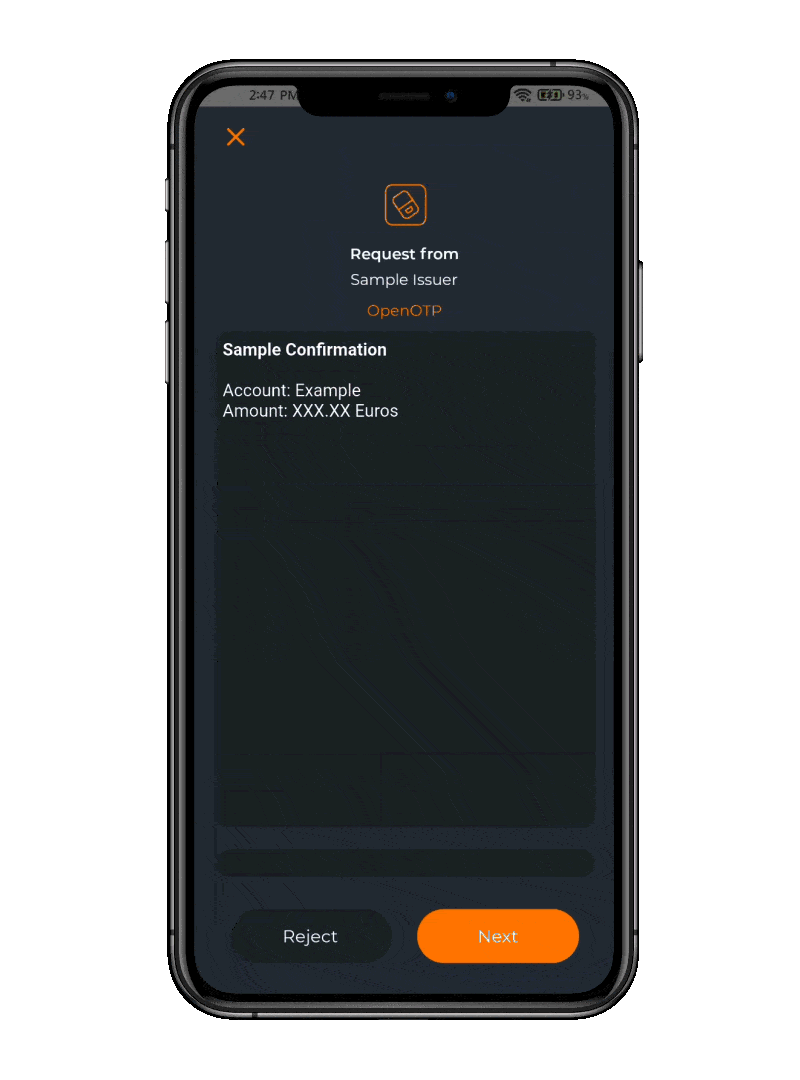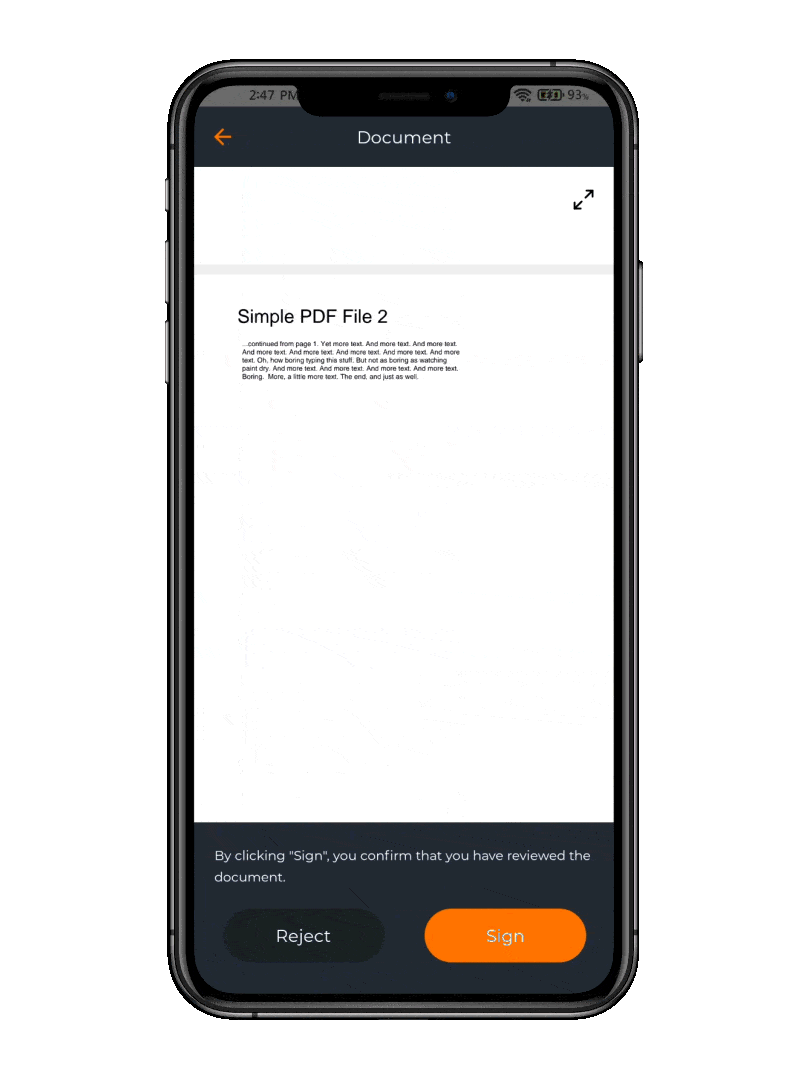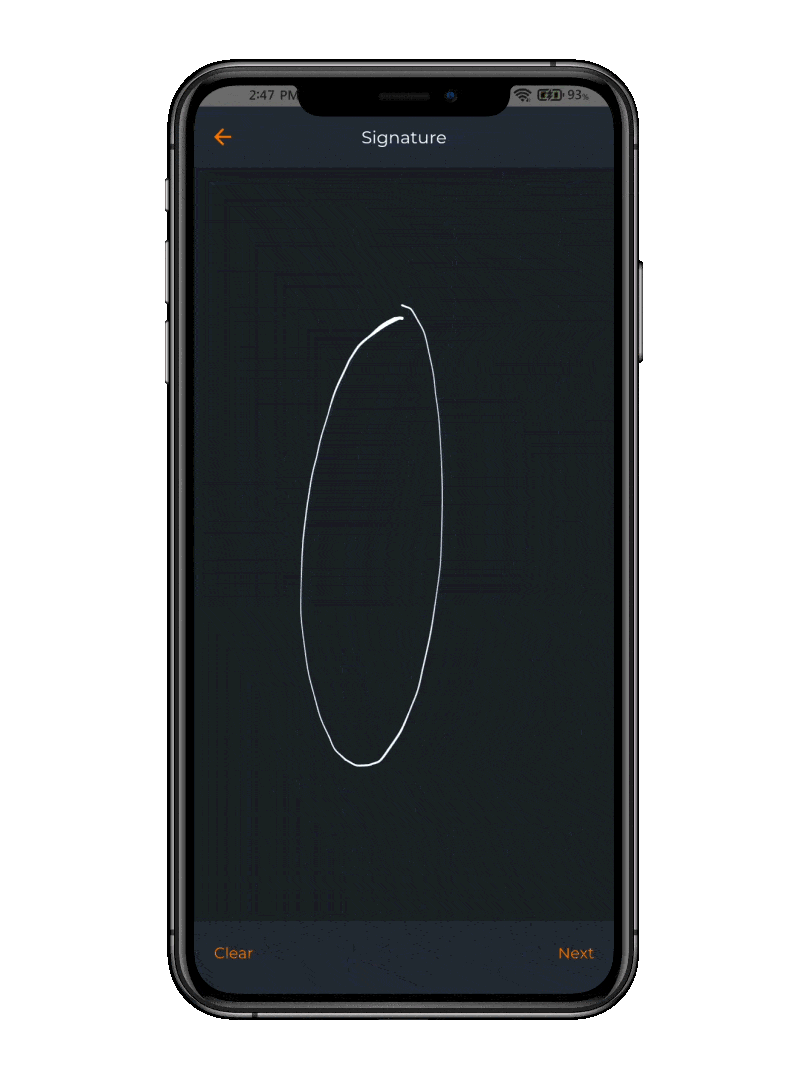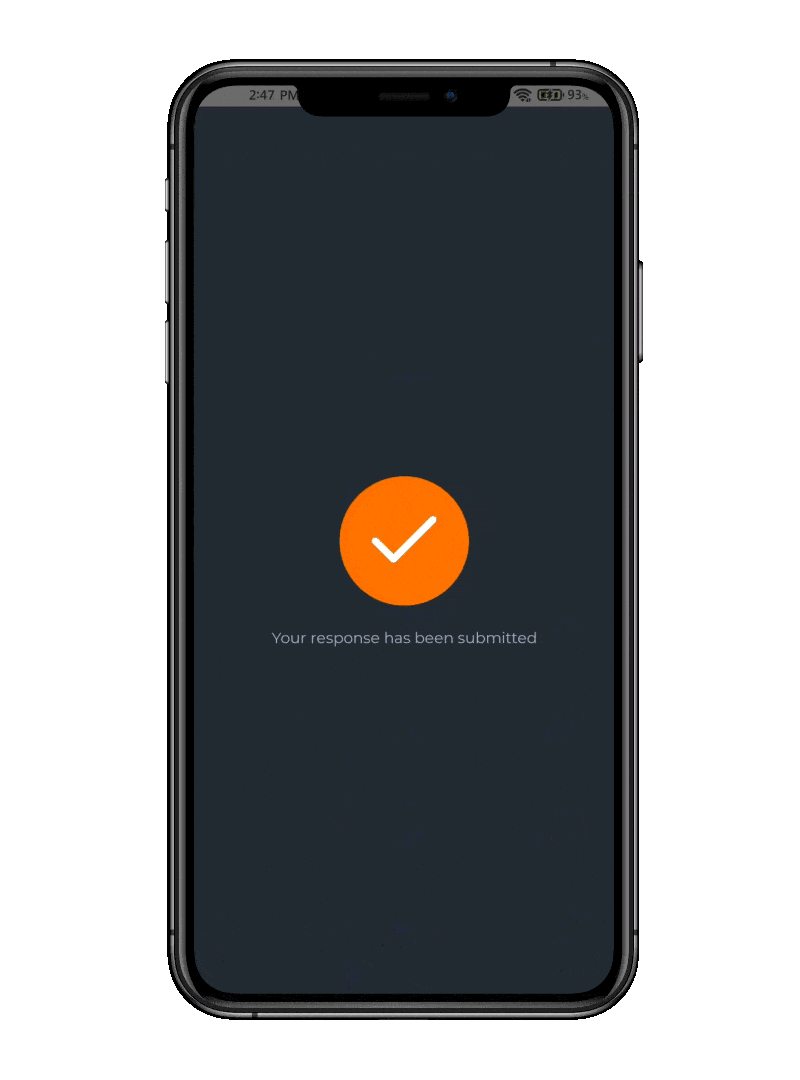
Push notifications have two distinct advantages. The first one is users will love the fact that they do not have to type a 6 or 8 digit code in less than 30 seconds. The second one is that a physical push action on a phone cannot be stolen and replicated by someone else.
Additionally, optional features like display codes, badging for location-based authentication, and app selection help users verify they are logging into a legitimate service, and therefore counter push fatigue attacks.
These features reduce the risk of users approving fraudulent requests by ensuring they can clearly identify the service they are interacting with, making it harder for attackers to exploit confusion or repetitive actions.
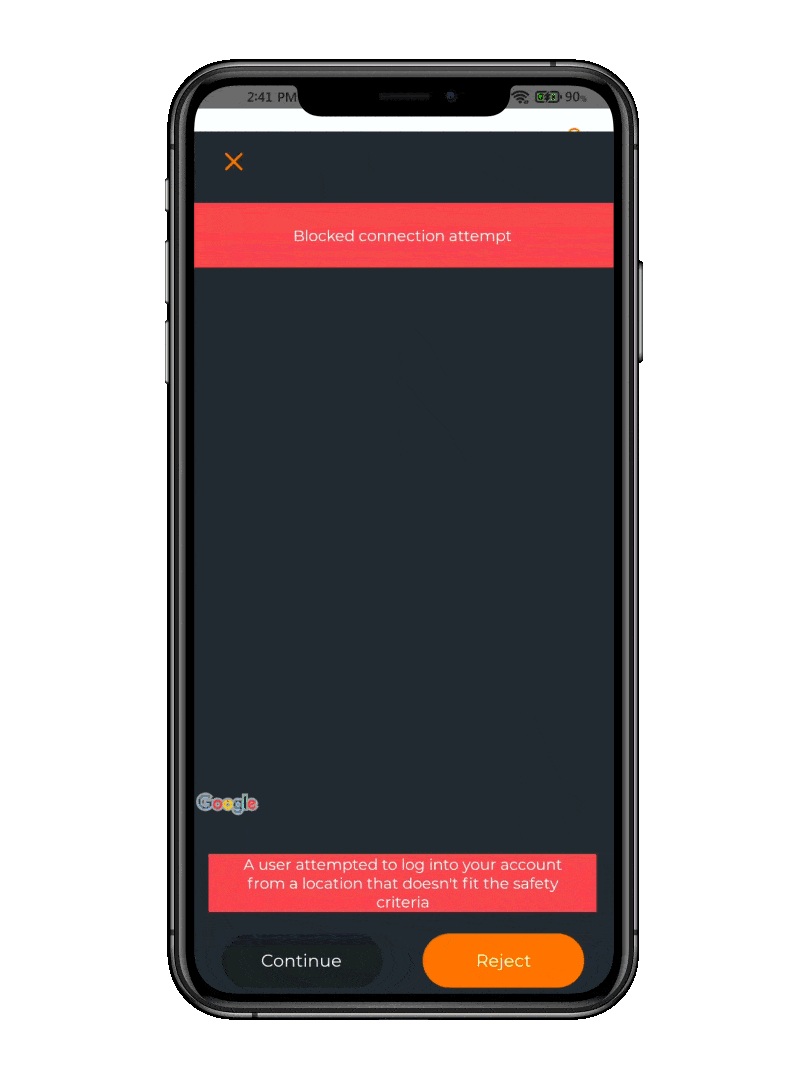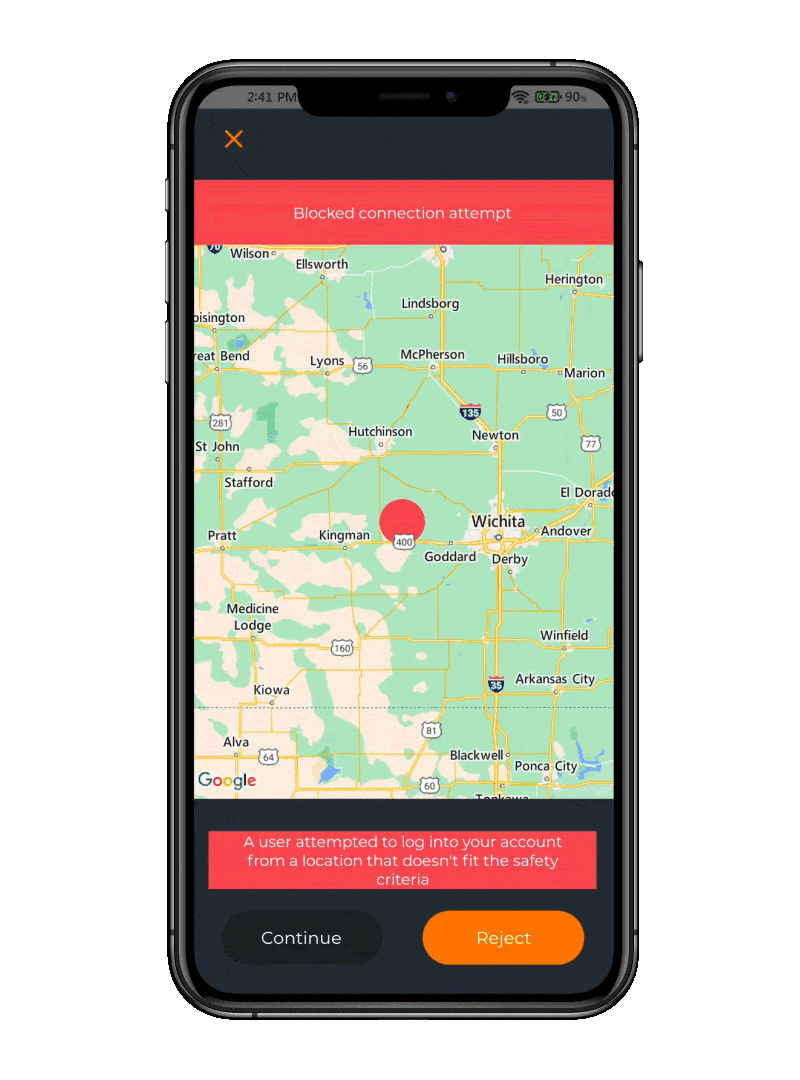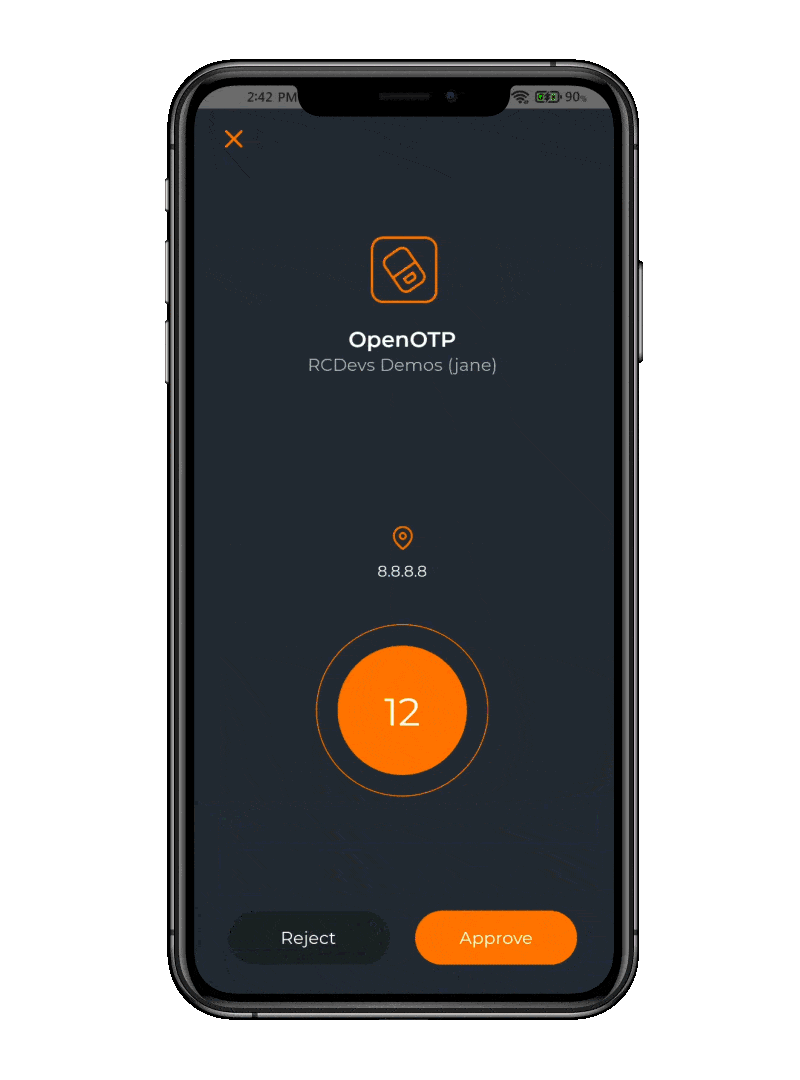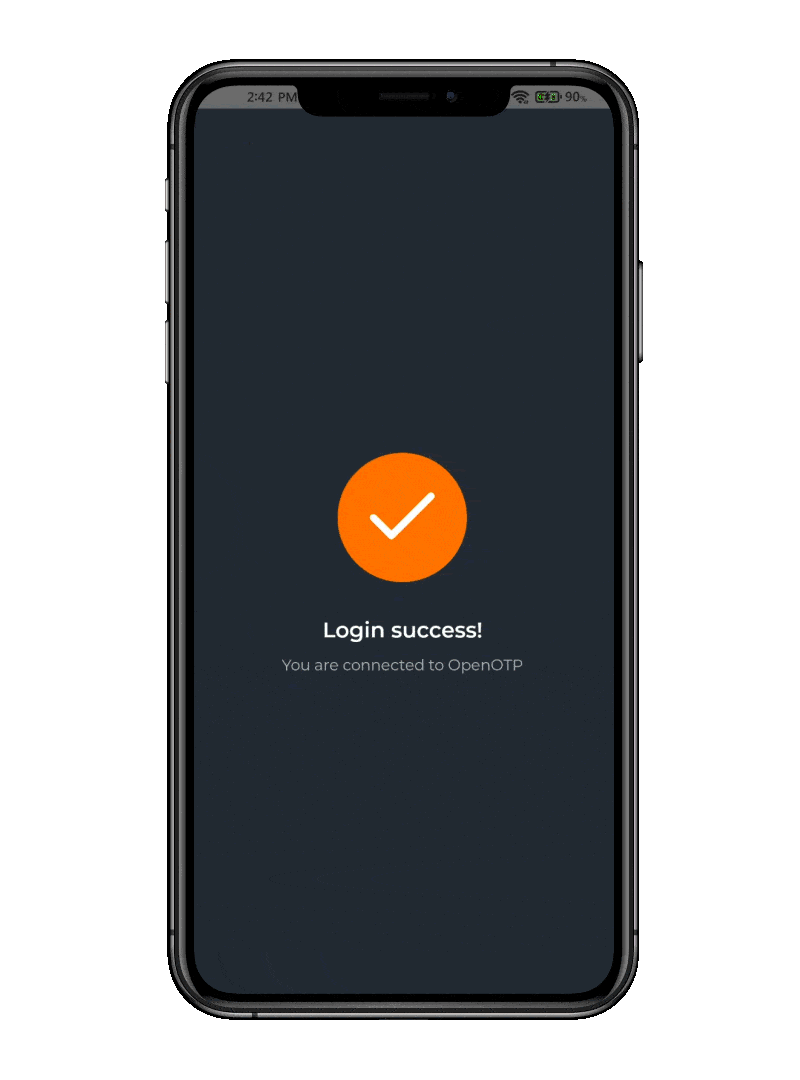
Anti-Phishing
Increase user cybersecurity awareness
Being warned that the IP address requesting access is not matching the location of the phone is a huge plus. It could be that your VPN is routing through a different location, in which case you can approve the Push and log in. If it is not you, you can reject the Push, denying access and warn your IT department about a possible phishing attack.
Agreement-based Logical Access
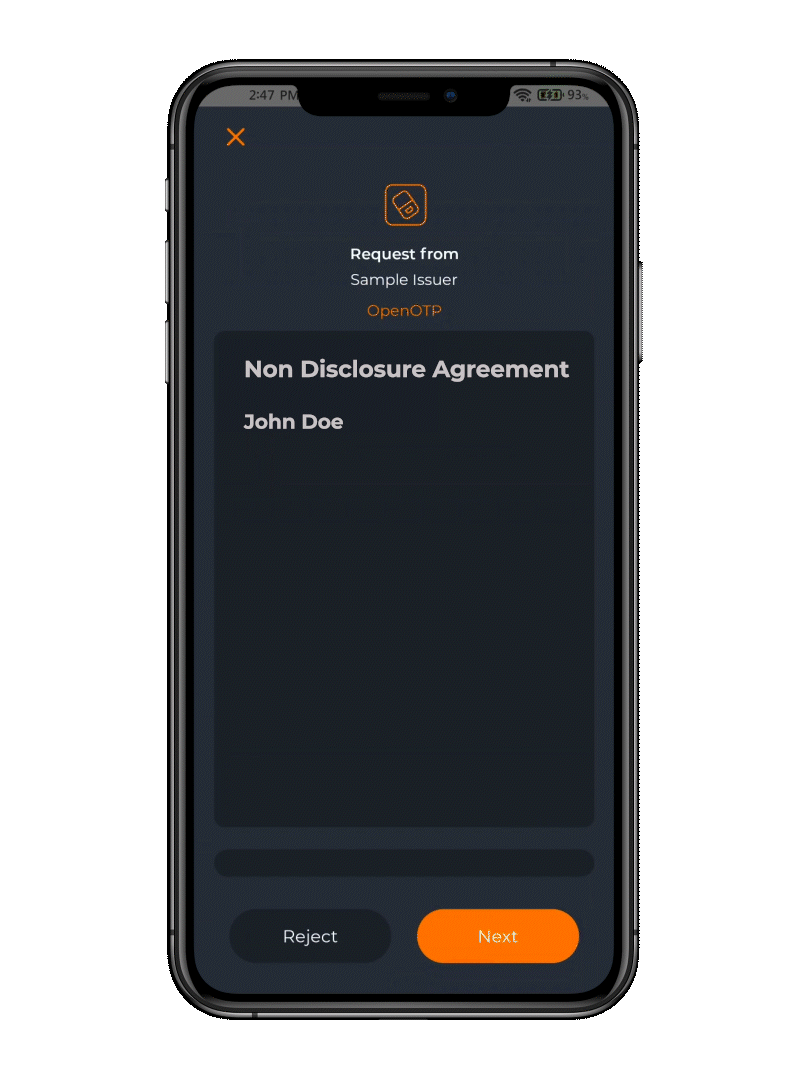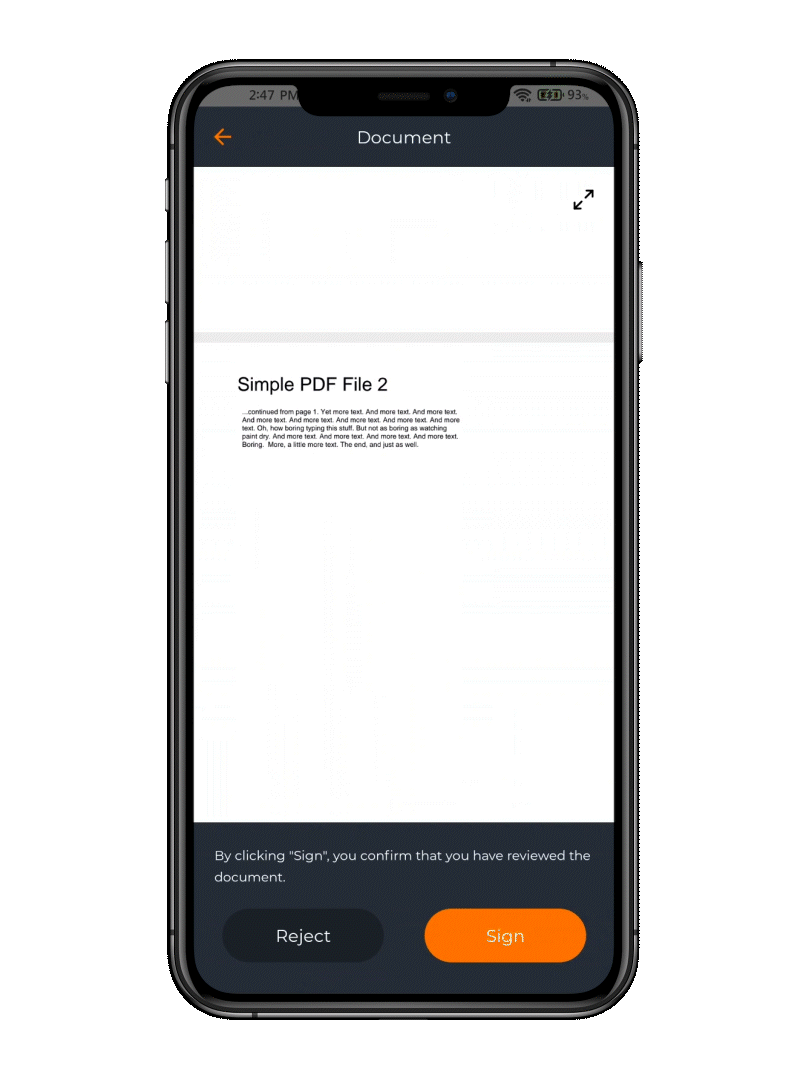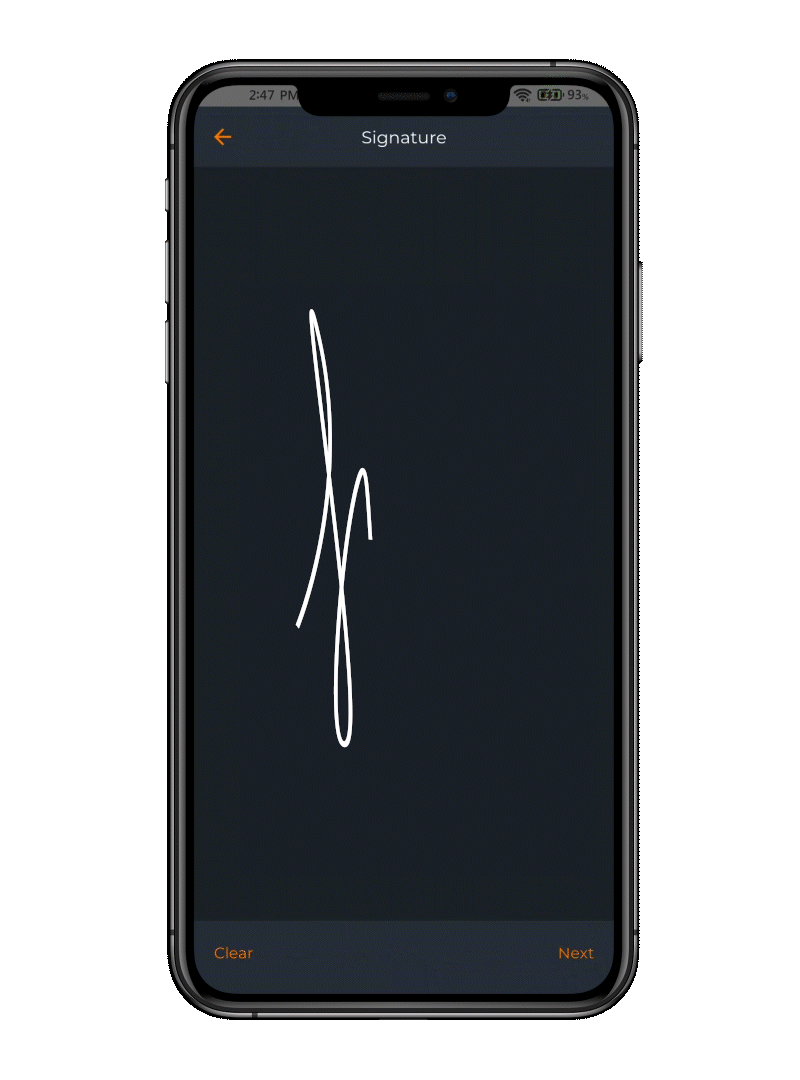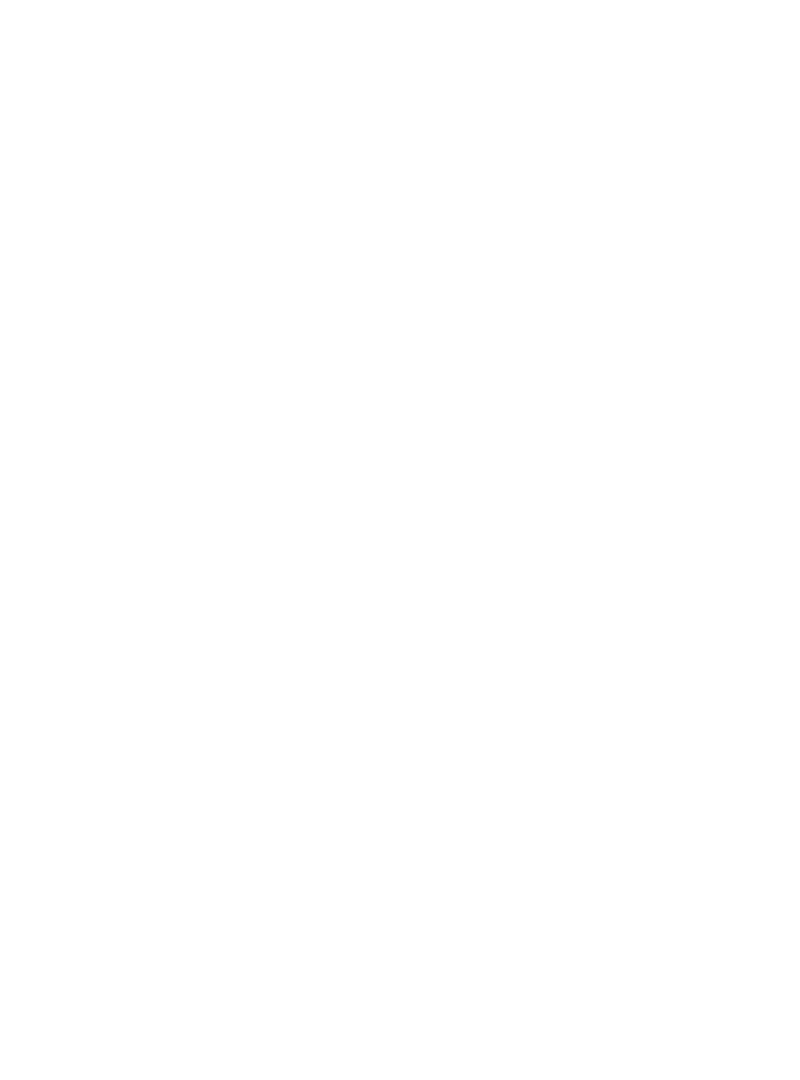
Add agreement-signing into your conditional access policies
Enhance access control by seamlessly integrating conditional access with time-stamped eIDAS e-signatures for agreements. Traditionally, authentication and signing processes are disparate, time-consuming, and costly endeavors. The OpenOTP Token App simplifies and accelerates these steps, merging them into an efficient and cost-effective process that enhances overall security and user experience.
Presence-based Logical Access
Reduces the attack surface to the minimum necessary
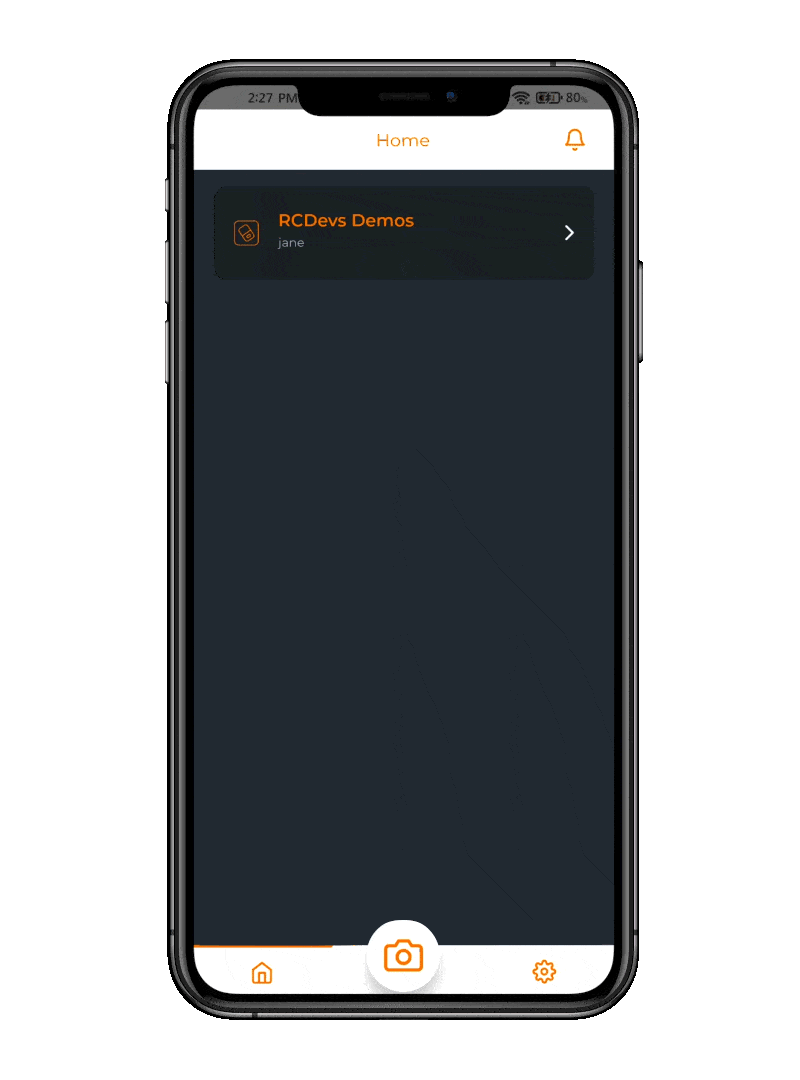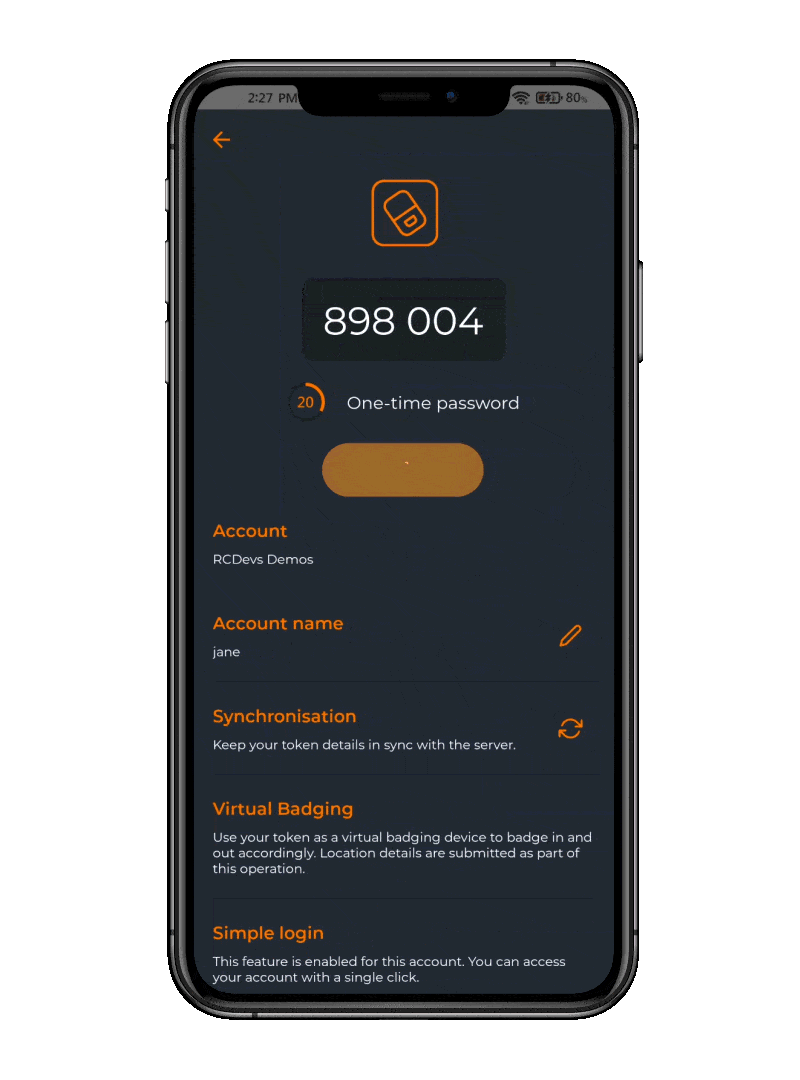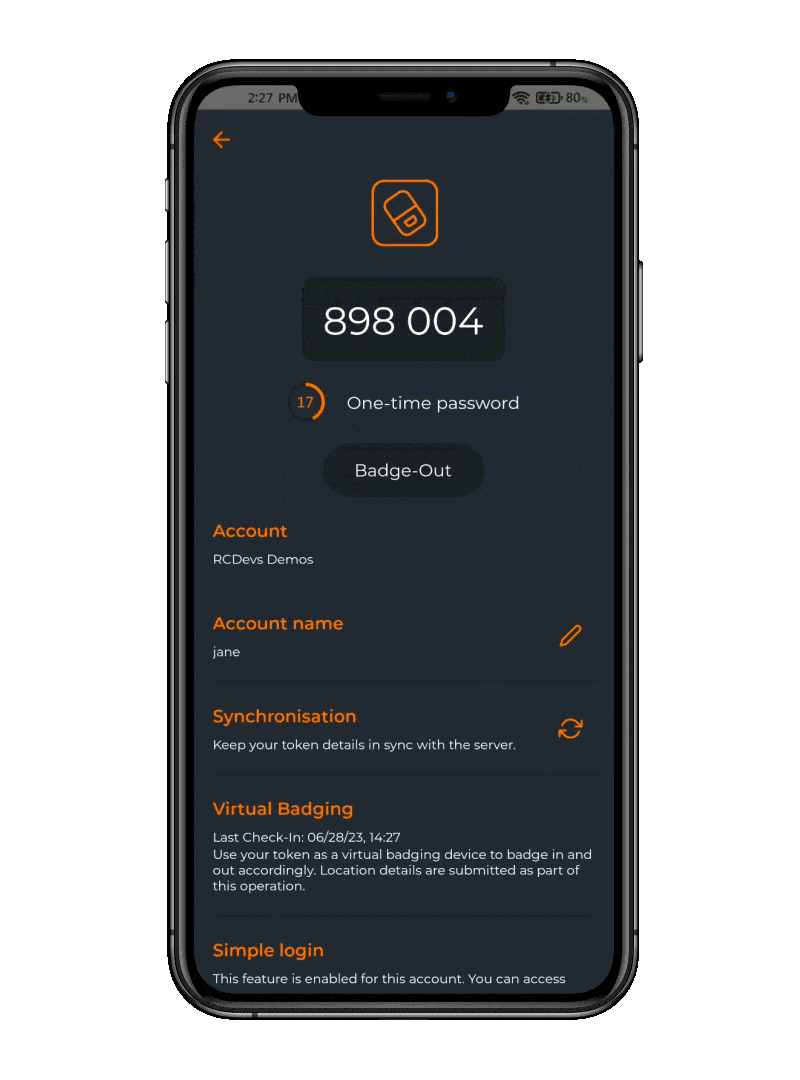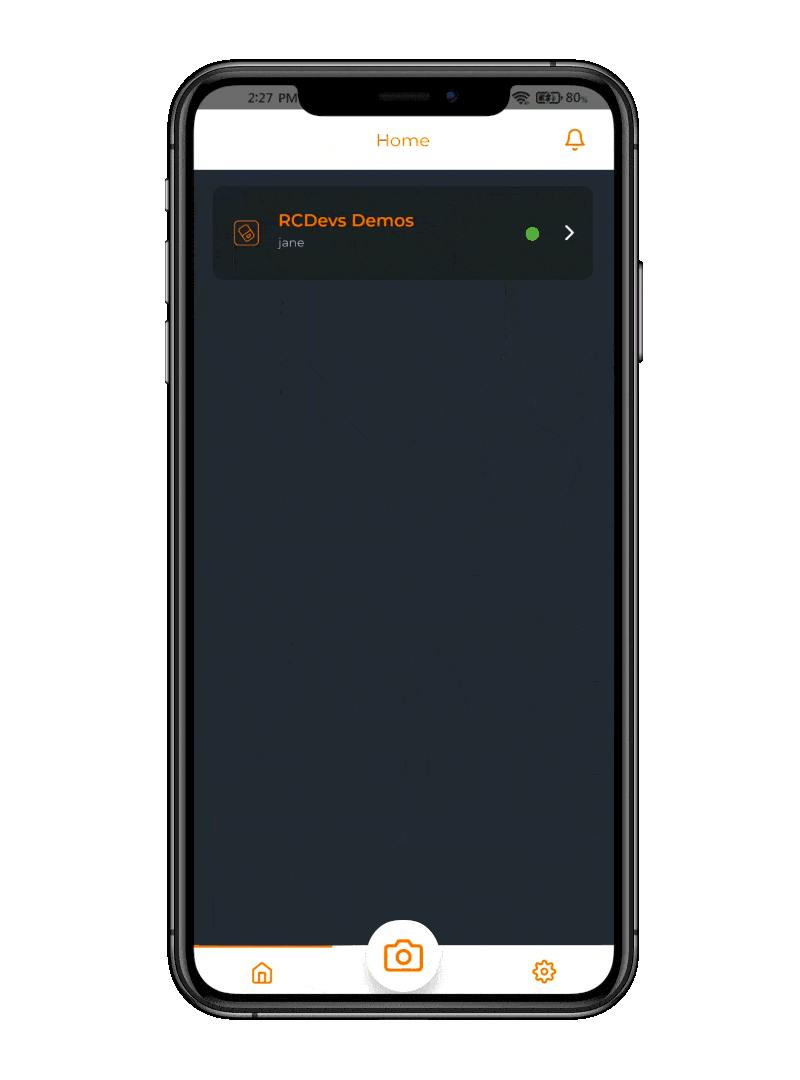
Presence-based Logical Access is a new approach to network security. The idea is to keep network access locked at all times unless an authorized employee has badged in. Thus, your networks are opened only to people effectively working and from an authorized location. OpenOTP Token App helps employees report to work in a simple and convenient way.
When integrated with OpenOTP Network Access Control (NAC), this system automates the badging process by granting network access and unlocking AD accounts based on user identity, location, and device MAC address. This integration ensures that only compliant devices and authorized users can access the network, adding a robust layer of security. For end-users, this process is friendly and elegant, providing seamless access without compromising on security. The automation simplifies their experience, allowing them to embrace security without worrying about network access complexities.
Electronic Signature
When your mobile becomes a signature device
The app offers the flexibility to e-sign documents using various integrations, allowing users to leverage their preferred platforms for digital signing. OpenOTP seamlessly integrates with your systems, empowering users to securely e-sign documents in their preferred workflows. (requires the purchase of e-signature credits)
More than
Clients
More than
Happy users
More than
Years of Expertise
Clients in more than
Countries
How we built our OpenOTP Token App
Additional Biometric security layer
With biometric protection, users can confidently rely on their unique physiological features, such as fingerprints or facial recognition, to safeguard their OpenOTP accounts from unauthorized access.
Secure Enrollment Procedure
RCDevs prioritizes the security of token enrollment by employing a secure process. The QR code (with optional PIN) is only used to initiate enrollment, rendering the QR code useless for potential attackers. This centralized and protected approach ensures a highly secure enrollment process.
Cryptographic Key
The cryptographic key used by the app is not only securely stored in the phone’s keychain but is also accessible exclusively by the app itself. Only the app has the necessary permissions and credentials to access and utilize the cryptographic key.
Fraudulent Connection Attempt
The app combats phishing attacks by analyzing the geographic location of the device during authentication. The app identifies and flags suspicious login requests originating from unfamiliar or unexpected locations.
SEEING
IS BELIEVING
Whether you are buying a car or a security solution, you always want to test drive it before signing on the dotted line. We know this and you know this.
Contact us for your Free PoC or check it out for yourself.