OpenOTP Network Access Control with MFA
Secure switches & WiFi networks with MFA

Unified IAM Federation
Native IAM Integration
OpenOTP is compatible with local directories such as Active Directory (AD) and LDAP, providing extensive support for on-premise environments. Additionally, it is natively integrated with EntraID, Okta, Google, Ping Identity, One Identity, and many other identity providers, enabling simple integration across diverse IAM systems.
Protect your Ethernet Switches & WiFi
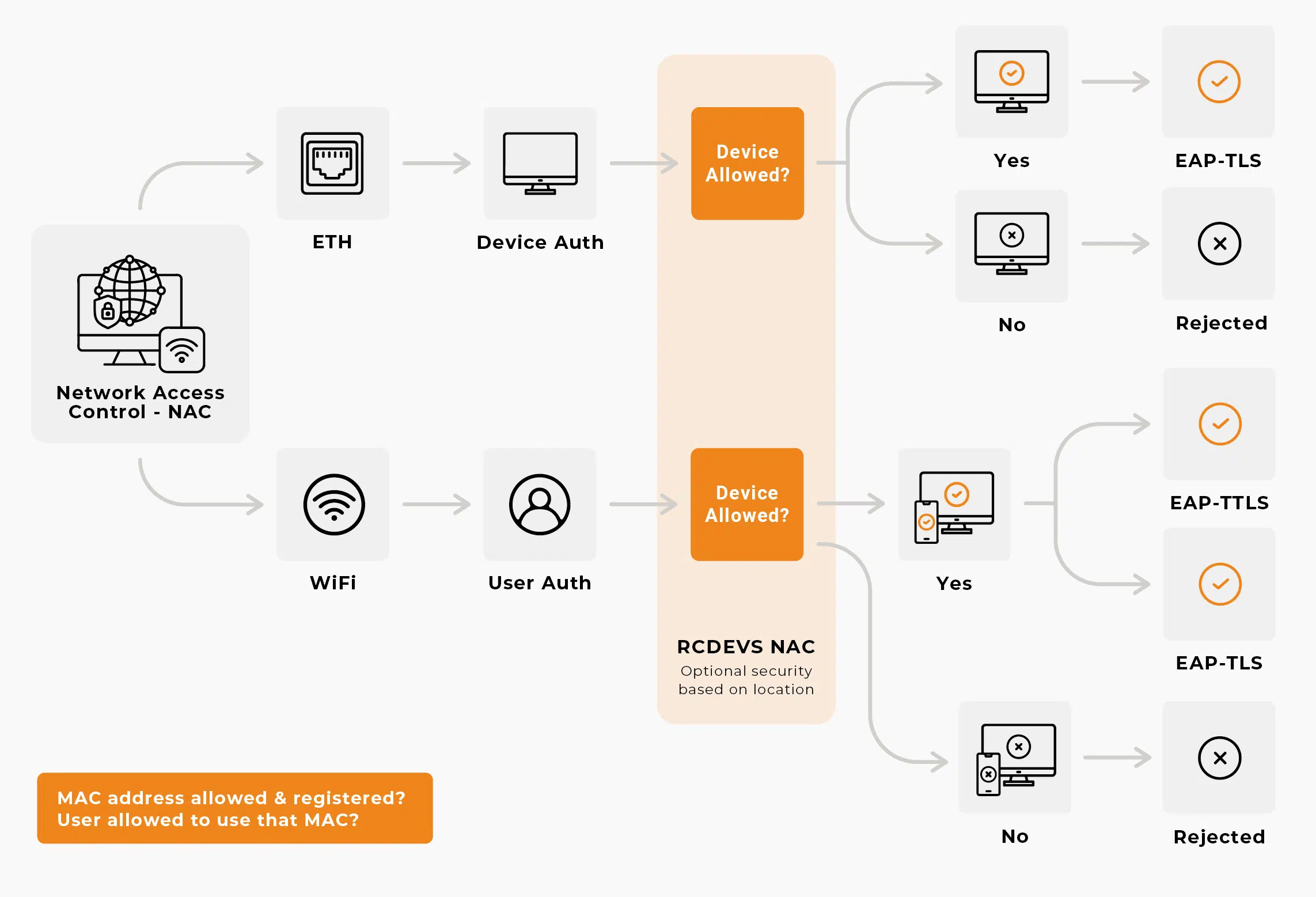
OpenOTP Network Access Control adds location-based security measures to your network access protocols. This feature ensures that only users in authorized locations can access network resources, significantly reducing the risk of unauthorized access. By combining location data with MAC address verification and device authorization, OpenOTP NAC provides a comprehensive and dynamic security solution tailored to the modern, mobile workforce.
By integrating advanced authentication methods and OpenOTP NAC, RCDevs offers a robust and secure network access control solution that keeps your enterprise network protected and efficient.
Main NAC Features
Supported on Enterprise WiFi/Ethernet with EAP-TLS (certificates)
Supports LDAP, OTP, Push and LDAP+OTP login modes
Per user/group/client Radius AVP for all providers
Authentication policies per client application or group of users
Customizable Dynamic Per user/group/client Policies
RCDevs 802.1X for WiFi is fully compatible with WebADM client policies
Define access control policies for each of your WiFi SSIDs
Client policies manage network access based on user groups, time, and LDAP metadata (i.e. VLAN access attributes which enable access to specific VLANs)

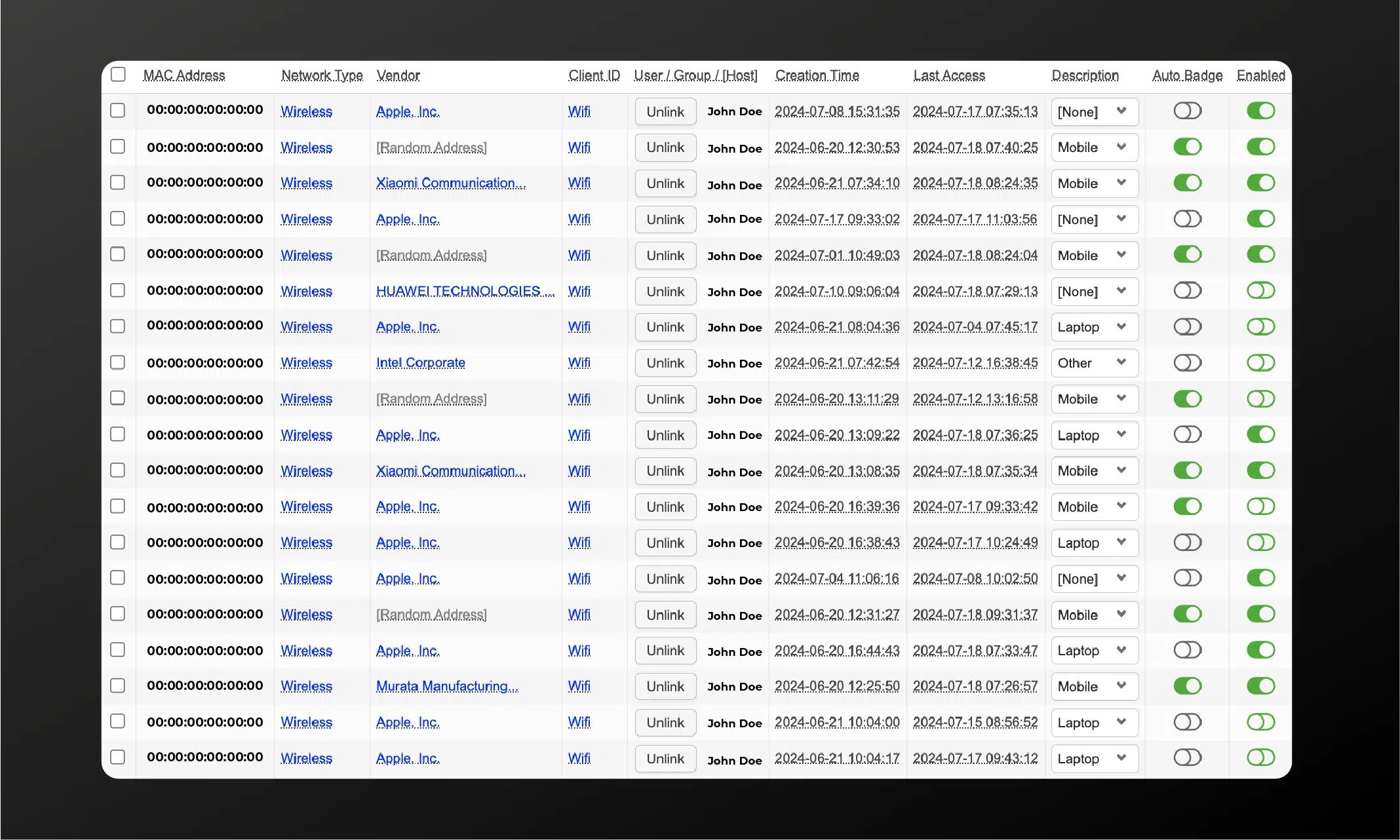
User / Device MAC Address Management
Manage and monitor MAC addresses on your network
Add MAC addresses automatically or upon admin approval
Automated alerts for Admins
Grant network access for devices only via client certificates
Only allow a user or group to use a specific MAC address
Temporarily deactivate MAC address or user network access or both
Presence-Based Logical Access Integration
Users are automatically badged in based on location and device MAC address
Network access is granted instantly upon successful badging
AD accounts are unlocked automatically when users are badged in
Access is controlled and regulated by predefined access policies
Enhances security by ensuring only authorized users and devices gain network access


Enhanced Security Measures
When users are not badged in or badge-out, their AD account is locked at the LDAP level
When users are not badged in or badge out, all network and system access are locked
Significantly reduces the attack surface when employees are not working or on vacation
OpenOTP NAC Operational Modes
OpenOTP NAC provides two operational modes, catering to different security needs and administrative preferences:
1. Auto-Creation Mode: This mode is ideal for environments with a large number of users or during the initial setup phase. When a new device connects to the network for the first time, OpenOTP NAC automatically registers the MAC address and links it to the user who is currently authenticated and present. This streamlined approach reduces administrative overhead and ensures seamless integration of new devices.
2. Strict Mode: For heightened security, strict mode requires administrative approval for each new device attempting to connect to the network. When a new device is detected, the system sends an alert to the administrator, who must then manually approve the device. This mode is perfect for environments where tight control over network access is critical.
3. Group-Based Access: administrators can define groups, restricting device usage to specific user groups. Only members of the designated group can use the device, making it easier to manage access and enhance security.
Ready to implement OpenOTP NAC?
Relevant Documentation
SEEING
IS BELIEVING
Whether you are buying a car or a security solution, you always want to test drive it before signing on the dotted line. We know this and you know this.
Contact us for your Free PoC or check it out for yourself.