OpenOTP Authentication Server
OpenOTP Authentication Server
MFA Server with OTP & FIDO2
Secure Your Systems with OpenOTP IAM-MFA Solutions, an integral component of the OpenOTP Security Suite. Safeguard your user network access with Multi-Factor Authentication (MFA). Reach out for a FREE PoC or explore it firsthand.
MFA Integrations & Solutions
On-Premise or SaaS
OpenOTP is compatible with local directories such as Active Directory (AD) and LDAP, providing extensive support for on-premise environments. Additionally, it is natively integrated with EntraID, Okta, Google, Ping Identity, One Identity, and many other identity providers, enabling simple integration across diverse IAM systems.
Main Solutions & Integrations
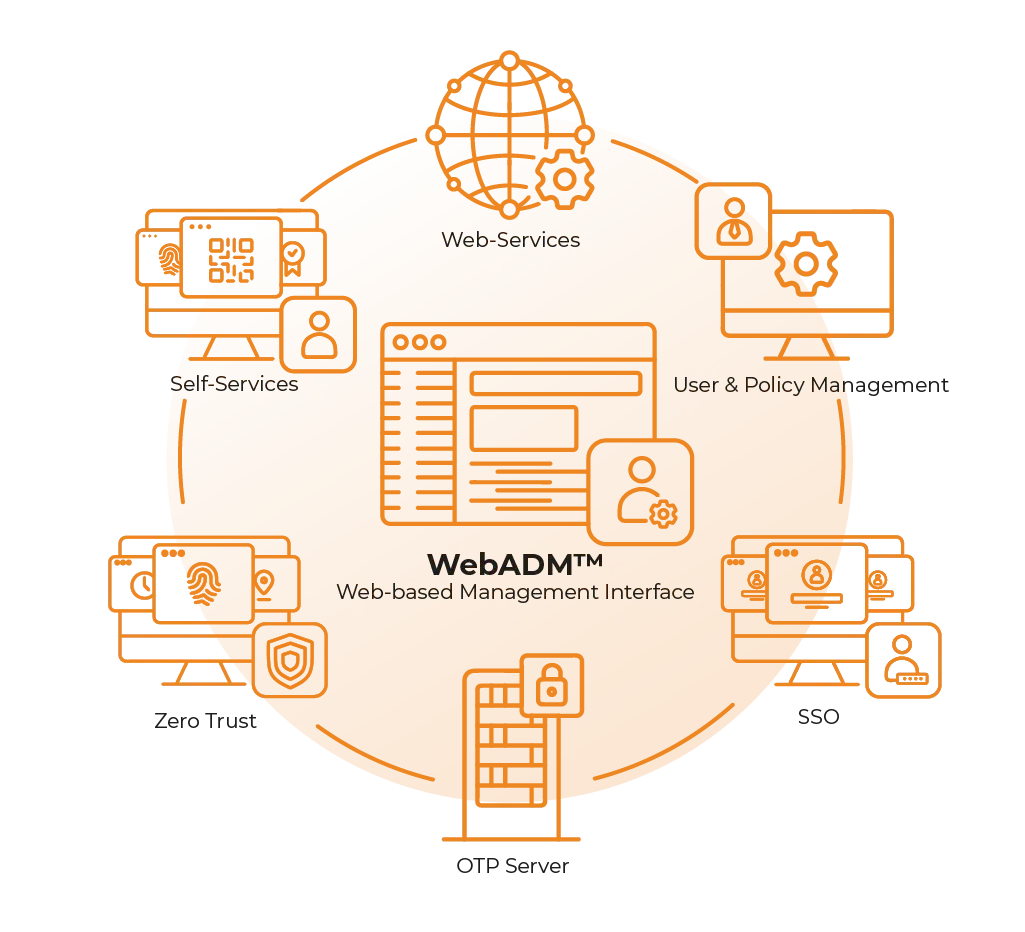
Identity & Access Management (IAM) and Policies
Geolocation-based access policies
DDOS and brute-force protection
Leaked / Pwned password detection
Federation (SSO)
Main License Features
On Premise and Cloud/SaaS Editions
Native AD / LDAP integration
High Availability (HA) for On-Premise Edition
SIEM integration
Multi-Domain
Strong Authentication Methods
Any OATH Hardware or Software Token
Multiple authentications with intelligent fallback
Mail, SMS, Printed OTP list

Unified IAM Federation
Native IAM Integration
OpenOTP is compatible with local directories such as Active Directory (AD) and LDAP, providing extensive support for on-premise environments. Additionally, it is natively integrated with EntraID, Okta, Google, Ping Identity, One Identity, and many other identity providers, enabling simple integration across diverse IAM systems.
Freeware & Trials
On-Prem or Cloud, OpenOTP is the solution
Looking for an On-Prem MFA solution?
Take the next step in securing your systems by downloading our OpenOTP Security Suite Virtual Appliance, with options available for VMWare and Hyper-V. Choose between our On Premise Freeware and Trial options below to experience robust security solutions firsthand.
1
Download
2
Install
3
License
4
Setup
5
Test/PoC
1
Register online
2
Select a Template
3
Test/PoC
Looking for a SaaS/Cloud MFA solution?
Easy and quick! Register using the online form.
In just a few clicks, your account (cloud tenant) will be created and automatically configured, including domain setup and more. Simply create a user and begin testing MFA in your infrastructure.
Select
They trust us around the world
More than
Clients
More than
Happy users
More than
Years of Expertise
Clients in more than
Countries
Choose the method that best suits you
Authentication Methods
RCDevs’ IAM-MFA Cybersecurity Solutions Compatible with Strong Authentication Login Technologies
Cost-Efficiency – Spend Less for More Security
OpenOTP Security Suite provides cutting-edge Multi-Factor Authentication (MFA), Identity and Access Management (IAM), and Federation and many more solutions, all in one.
RCDevs Security offers top-tier security without the hefty price tag, allowing you to save significantly compared to high-cost competitors. Secure Your Systems with OpenOTP IAM-MFA Solutions!
Less is more? We agree 100%!
SEEING
IS BELIEVING
Whether you are buying a car or a security solution, you always want to test drive it before signing on the dotted line. We know this and you know this.
Contact us for your Free PoC or check it out for yourself.









