OpenOTP Federation Services: MFA for Single Sign-On and ADFS
Combine SSO (OpenID or SAML) and ADFS with a 2FA Solution
OpenOTP OpenID & SAML IdP
Combining SSO & MFA improves the security of your user logins.
Combine SSO (OpenID or SAML) and ADFS with a 2FA Solution
OpenOTP’s Single Sign-On (SSO) solution is easy to implement, convenient & time saving.
OpenOTP Security Suite includes an Identity Provider (IdP) allowing
federated identity management, commonly referred to as SSO.
OpenOTP OpenID & SAML IdP supports OpenID, OAuth, Kerberos and SAML2 standards.
Our IdP can be configured with both on premise and cloud applications and offers passwordless authentication.
SSO with RCDevs Security
OpenOTP OpenID & SAML IdP
OpenOTP OpenID & SAML Identity Provider works with OpenOTP’s authentication back-end.
RCDevs’ SSO solution also supports PKI-based authentication as well (with user certificates).
When users access a website with SSO, they establish a security association between the website, themselves, and the identity provider. The identity provider redirects them for a trusted authentication process.
Compared to other OpenID and SAML implementations, RCDevs’ SSO solution is very easy to implement, provided that you already have a working WebADM server with an OpenOTP license. The setup consists of adding the OpenID/SAML WebApp in WebADM and configuring authentication and access policies.
For more details on how to implement our IdP, please read our
Online Documentation or contact RCDevs for a more personalized explanation.
Main Key Features
Supports SAML2, OpenID-Connect & OAuth2
Supports IdP or SP initiated requests for Cloud SSO
Return group memberships & configurable user attributes
Uses all OpenOTP authentication methods (see list below)
Supports full PKI authentication with user certificates
Easy corporate SAML/OpenID-Connect configuration with metadata URL
Application-Federated Access based on authentication & access policies
Passwordless
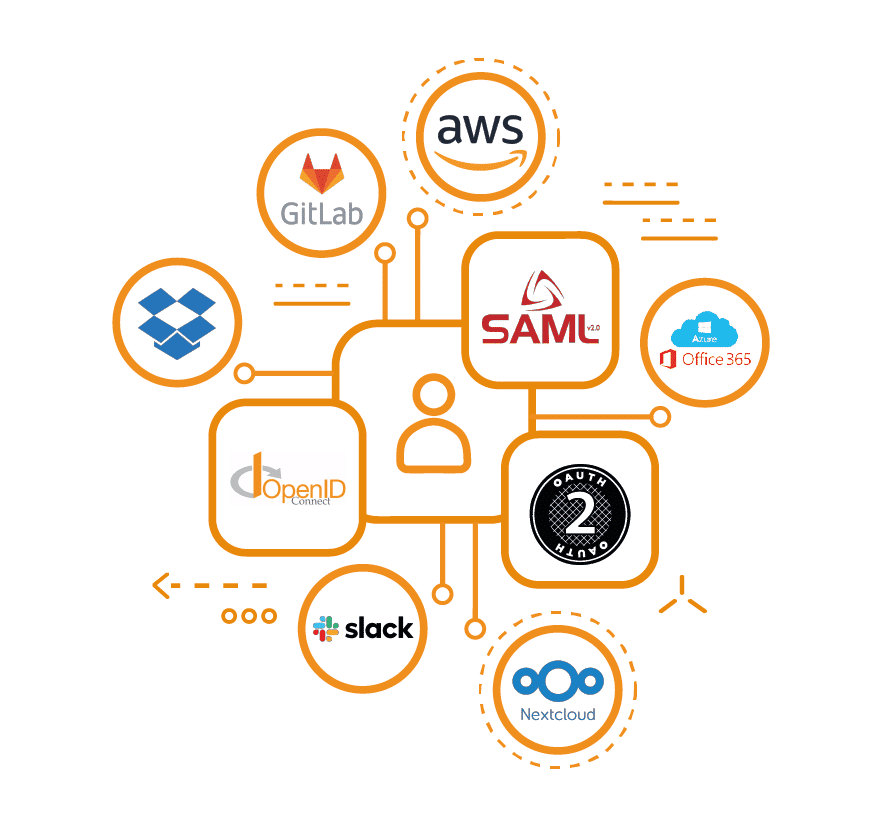
Supported SSO Standards
- OpenID Connect - OAuth2 - Kerberos Please note OpenID v1.1 & v2.0 are deprecated and have been removed
SSO Integration Examples
For some SSO integration examples, please check RCDevs' Online Documentation.
Microsoft ADFS
Multi-Factor Authentication & Federation Service with Microsoft Web Applications
ActiveDirectory Federation Services (ADFS) is the new way for implementing Web-based authentication and Single-Sign-On (SSO) functionalities in Microsoft environments.
Current versions of Exchange and Sharepoint portals can use ADFS natively provided that an ADFS instance is running on the network.
Unlike Kerberos SSO, ADFS is for Web access and it supports federating your corporate services, Cloud applications and Office 365.
MICROSOFT ADFS with RCDevs Security
Enhance your ADFS infrastructure
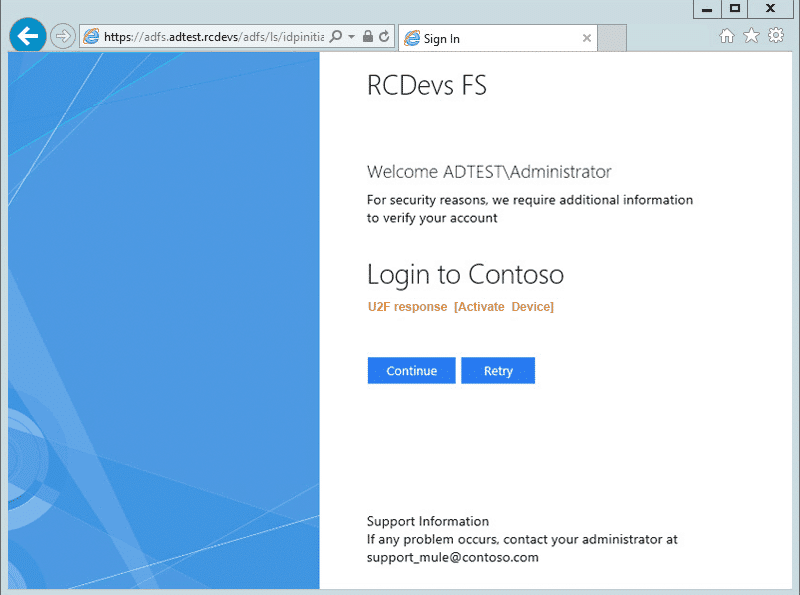
RCDevs supports all federation through MICROSOFT ADFS
RCDevs provides an OpenOTP Authentication Provider (AP) for ADFS. OpenOTP AP is a component that integrates OpenOTP One-Time Password (OTP) and FIDO2 authentication into all your ADFS-enabled applications, whether web-based or thick clients (as in Outlook or Teams for example). Our Authentication Provider works with all authentication methods supported by the OpenOTP Server.
Mixed OTP & FIDO2 Login
OpenOTP for ADFS supports both OTP (with all OpenOTP one-time-password methods) and FIDO2 signed authentication. Provided that your users are enabled with either OTP Tokens, YubiKey, SMS or FIDO2 devices, the ADFS authentication process proposes user logon with any of the supported authentication method. RCDevs is currently the only solution which provides mixed OTP and FIDO2 for ADFS.

Key Features
Integrates with any ADFS-enabled application
Supports ActiveDirectory User Principal Names (UPN)
Supports LDAP, OTP and LDAP+OTP login modes
Supports thick clients like Outlook or Teams through Modern Authentication
Supports any OpenOTP method (Tokens, Yubikey, SMSOTP, MailOTP)
Supports both challenged OTP and concatenated passwords
Supports FIDO2 signed authentication
Compatible with
All Federation through Microsoft ADFS Solution
Outlook Web Access and Sharepoint
IIS Web Applications
Office 365
Other SAML-Enabled Applications






Unified IAM Federation
Native IAM Integration
OpenOTP is compatible with local directories such as Active Directory (AD) and LDAP, providing extensive support for on-premise environments. Additionally, it is natively integrated with EntraID, Okta, Google, Ping Identity, One Identity, and many other identity providers, enabling simple integration across diverse IAM systems.
Choose the method that best suits you
Authentication Methods
RCDevs’ IAM-MFA Cybersecurity Solutions Compatible with Strong Authentication Login Technologies
SEEING
IS BELIEVING
Whether you are buying a car or a security solution, you always want to test drive it before signing on the dotted line. We know this and you know this.
Contact us for your Free PoC or check it out for yourself.