SpanKey SSH Key Server
SpanKey SSH Key Server
Centralized Linux Authentication
The IT infrastructure for most organizations relies on Linux
and Unix servers.
Linux server access is generally implemented with SSH for both administration and host-to-host scripting. The SSH protocol is secure and extremely convenient for server management.
Adding an extra security layer is recommended for SSH management with critical/production systems.
RCDevs Security provides these extra layers of security by combining SSH Public Keys and Multi-Factor Authentication (MFA).
RCDevs helps you
Centrally manage SSH Keys
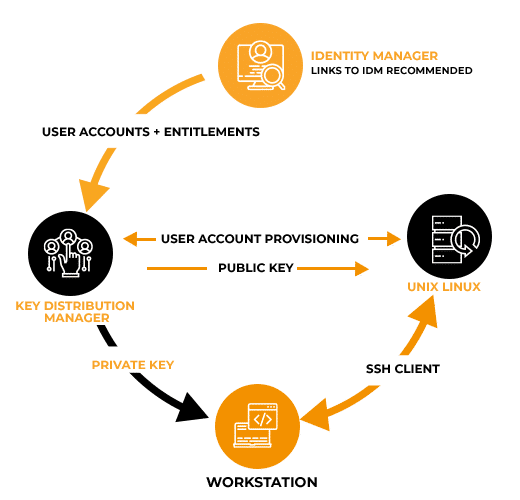
RCDevs’ SpanKey solution provides extended SSH key life-cycle management. This includes self-services for web-based SSH key self-enrollment with software and hardware private keys, automated key distribution, auditing of unwanted access and auto-renewal workflows for outdated public keys.
SpanKey is the centralized SSH key service component for OpenSSH where the public keys are stored in your central LDAP directory (ex. Active Directory). With SpanKey there is no need to distribute, manually expire or maintain the public keys on the servers.
Instead, the SpanKey agent is deployed on the target Linux servers and is responsible for providing the users’ public keys on-demand. SpanKey server provides per-host access control with “server tagging”, LDAP access groups, management from the RCDevs WebADM console, shared accounts, privileged users (master keys), recovery keys.
Our SpanKey solution is designed to support even the largest of IT estates.
Easy Keys Enrollment with Self-Services
The RCDevs’ Self-Service applications include an SSH key management feature that allows users to create their own SSH key-pair and get the associated public key automatically enrolled on the SpanKey server. The list of allowed SSH key types (RSA/ECC/DSA) and key length (number of bits) is configurable on the SpanKey server. The self-service generates a new key pair and securely provides the private key in several formats, including PuTTY and OpenSSH. A policy configuration can optionally enforce passphrase protection. The self-service access can be protected by an OTP login method with RCDevs’ OpenOTP.
Graphical Session Recording
With SpanKey, terminal sessions are monitored and recorded. Idle sessions get automatically locked after a configurable time and a user password prompt is used for unlocking. But more important, terminal user sessions are recorded live into the WebADM secure record database. Sessions are stored encrypted on either the SQL database or a NAS mount. For audit and investigation purposes, you can also re-play terminal sessions with the session player within WebADM. SpanKey is able to record a one-day SSH session in 3 MBytes only! So unlike with competitor solutions where recording gets quickly heavy in storage size, SpanKey lets you keep your audit information for years without requiring extra terabytes.
Automated Public Key Expiration
Expiring SSH keys after a fixed amount of time is required for ensuring a certain level of trust for the user keys and to comply with ISO or PCI regulations. When SpanKey is configured with key expiration, the users are automatically notified upon expiration of their public. An email is sent with a renewal link allowing them to self-renew their just-expired public key.
Conditional Access
Conditional access relies on two key methods:
Agreement-based logical access ensures users agree to specific terms or policies before gaining access, promoting compliance.
Presence-based logical access leverages real-time location or device data to grant access based on contextual criteria, like network location or device trustworthiness.
These methods enhance security by combining agreement confirmation with contextual factors, helping organizations enforce stringent access controls and protect critical assets.
Support for Shared Account
Shared accounts are very common practice with the Enterprise use of SSH. A shared account (like ‘root’ or a ‘webmaster’ user) is a system account that is used concurrently by several administrators. In SpanKey you can transform any generic LDAP user into a shared SSH account simply by linking this account to a ‘shared access LDAP group’. Then all the members of the group gain access to the shared account with their own SSH key.
Centralized Audit Rules and Logs
With SpanKey Server integrated with WebADM client policies, you gain the ability to centrally establish and manage Auditd rules, ensuring their enforcement during SSH authentications. Furthermore, this setup enables the collection of logs from all SpanKey clients, facilitating their transmission to the SpanKey Server, which can then seamlessly relay them to a SIEM system for comprehensive security analysis and monitoring.
Master Keys and Recovery Keys
In SpanKey you can define master groups where the members of the group are considered as super users and can use their SSH key to access any other SpanKey account. A master group can be configured differently for different sets of target servers via WebADM Client Policies.
By default, the SpanKey agents will erase the users’ authorized_keys file at runtime to prevent users from adding unhanded public keys. If recovery keys are configured, then these keys are automatically written to the user’s authorized_keys file for recovery purposes (in the event where the SpanKey agent cannot communicate with the SpanKey server).
HSMs & Hardware SSH Devices
When HSMs (ie. YubiHSM) are used in WebADM, the SSH private key generation will use the HSM’s true random generation to gather the required entropy (random bytes) used in the SSH key-pair creation process. SpanKeys uses HSMs for both RSA and ECC (Elliptic Curve) key generation.
SpanKey supports Hardware Devices like Smartcards and the Yubikeys v4 with PIV Applet. With Hardware SSH devices, there is no SSH private key file; the users just need to plug the device in the USB port for connecting remote servers with SSH.
Architecture diagram of
SpanKey Server & SpanKey OpenSSH Agent
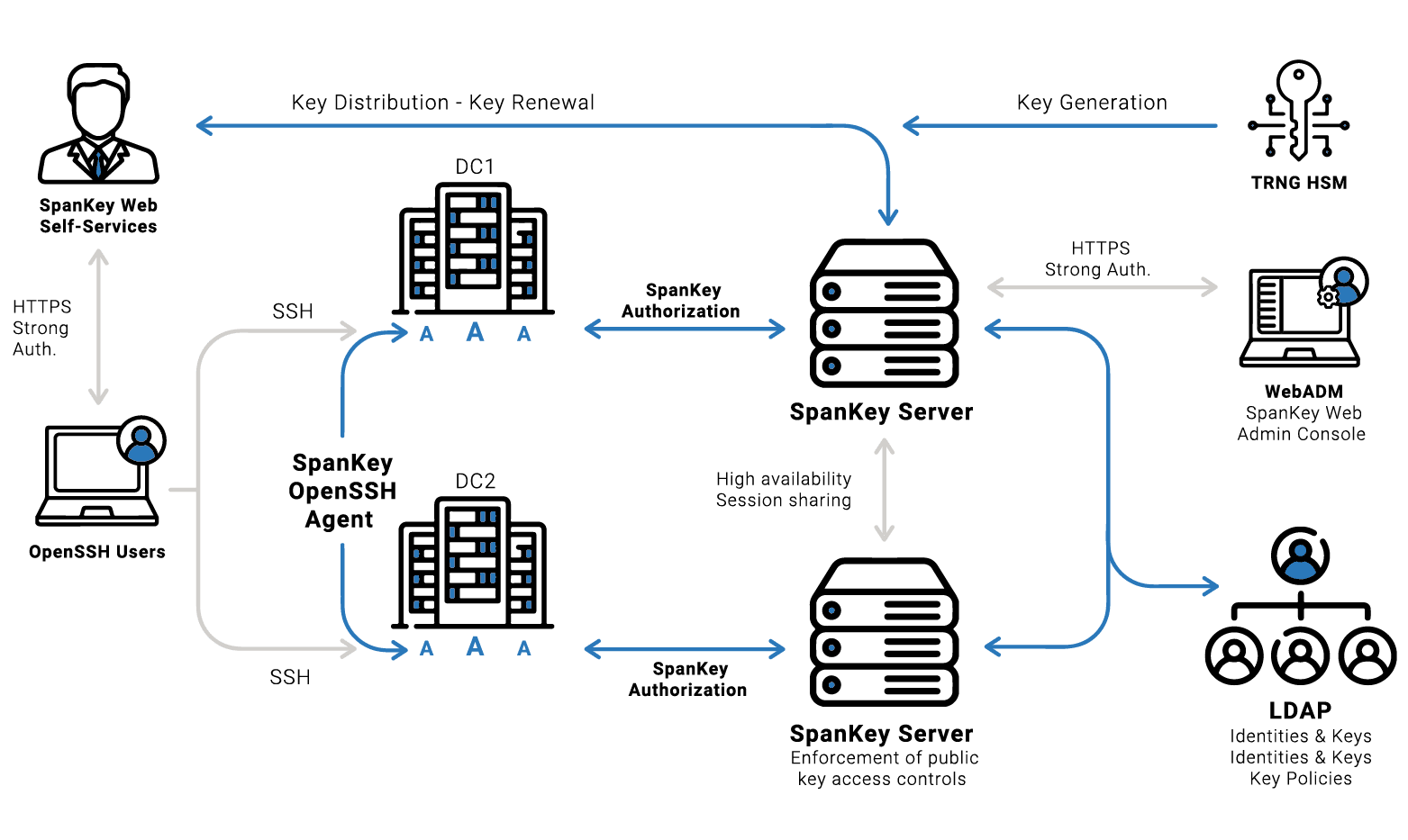
Where to use SpanKey?
The SpanKey server runs on your WebADM Cluster and is connected to your Active Directory or any other LDAP directory.
The SpanKey agent for Linux is provided as RPM and DEB packages.
It can be used on:
• Oracle / RedHat / Centos Servers
• Debian / Ubuntu
• Suse Linux
• Raspberry Pi/ ARM
Public Key Algorithms
SpanKey supports the industry standards for public key-based authentication with OpenSSH:
• RSA With 1024, 2048 and 4096 bits
• ECC (Elliptic Curve) With 256, 384 and 521 bits
• DSA With 1024 bits only



