Agreement-based Logical Access
Conditional Access
Agreement Based Logical Access
In the IT, legal, healthcare, financial, and various other sectors, trust and security are paramount in the digital realm. The act of signing terms and conditions (like NDAs before entering a dataroom, complying with regulations like GDPR) as a prerequisite for gaining access, creates a secure digital environment for sensitive data and information.
What is Agreement Based
Logical Access?
When logging in meets legality
OpenOTP Security Suite offers conditional access based on time-stamped eIDAS e-signatures of agreements, merging authentication and signing into one efficient process.
These steps are usually separate, time-consuming and can be quite costly. OpenOTP Security Suite streamlines them.
Sign Digital Contracts during MFA login process! Users log in and/or authenticate and sign agreements, such as Non-Disclosure Agreements (NDAs) or contracts in one go, and any changes in the agreement trigger a new signature request, enhancing security and ensuring the latest terms.
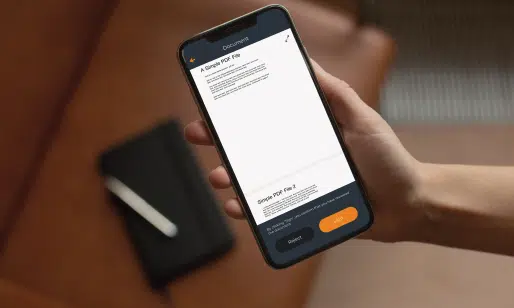

This integration not only simplifies user journeys but also saves time and resources while promoting a paperless environment.
If Multi-Factor Authentication (MFA) is added during the login process, you are always assured that the right person is granted the right access.
It is a transformative solution for businesses, aligning perfectly with the digital age’s demands for efficiency, security, and sustainability.
OpenOTP generates complete, signed, and stamped legal documents, making it a game-changer in access control & e-signature integration.
Agreement Based Access Process
Compliance Related Problems

Companies across various sectors, including financial services, education, healthcare, and more, are grappling with a growing array of compliance challenges in today’s regulatory landscape.
These challenges stem from an increasingly complex web of laws, regulations, and industry standards aimed at protecting consumer rights, data privacy, financial stability, and public health.
The global nature of business operations has intensified these compliance concerns, as companies often need to navigate a patchwork of international regulations and cross-border legal frameworks.
Navigating this intricate compliance landscape has become not just a legal obligation but a strategic imperative for businesses, as failure to do so can lead to regulatory penalties, reputational damage, and financial losses.
In this dynamic environment, staying proactive and agile in addressing compliance challenges has become a crucial aspect of corporate governance and risk management.
Main sectors facing compliance challenges
Financial Services
All the above require substantial investments in resources and technology to ensure compliance and financial integrity.
Healthcare
These challenges demand meticulous adherence to regulations to protect patient confidentiality, ensure accurate billing practices, maintain the highest standards of care, and navigate a complex web of international and regional compliance standards to avoid legal repercussions and financial penalties.
Technology & Data Privacy
Organizations must also implement robust policies for data retention (e.g., GDPR's right to be forgotten) and data breach notification (e.g., GDPR's 72-hour notification rule). This compliance framework is crucial for safeguarding PII (Personally Identifiable Information) and sensitive data, reducing the risk of regulatory fines.
These regulations require robust data encryption, secure storage, and comprehensive privacy policies to mitigate the risk of data breaches and legal consequences.
Insurance Services
In Europe, the General Data Protection Regulation (GDPR) enforces strict data protection rules for insurers, while the Insurance Distribution Directive (IDD) harmonizes insurance distribution across the EU. Solvency II is a comprehensive framework focusing on financial stability, and European regulations emphasize consumer protection in areas like pre-contractual information and claims handling, ensuring policyholder interests are safeguarded.
E-Signatures
In the United States, electronic signatures are regulated primarily under the Electronic Signatures in Global and National Commerce Act (ESIGN) and the Uniform Electronic Transactions Act (UETA). Both ESIGN and UETA establish a legal framework for electronic signatures, making them legally binding and enforceable, provided certain conditions are met.
Educational
Legal
Maintaining legal compliance is essential for avoiding legal penalties, protecting an organization's reputation, and ensuring ethical business practices. It requires ongoing monitoring, policy implementation, and a commitment to operating within the boundaries of the law.
Telecommunications
OpenOTP Security Suite, the Solution
WebADM, Your IAM Solution
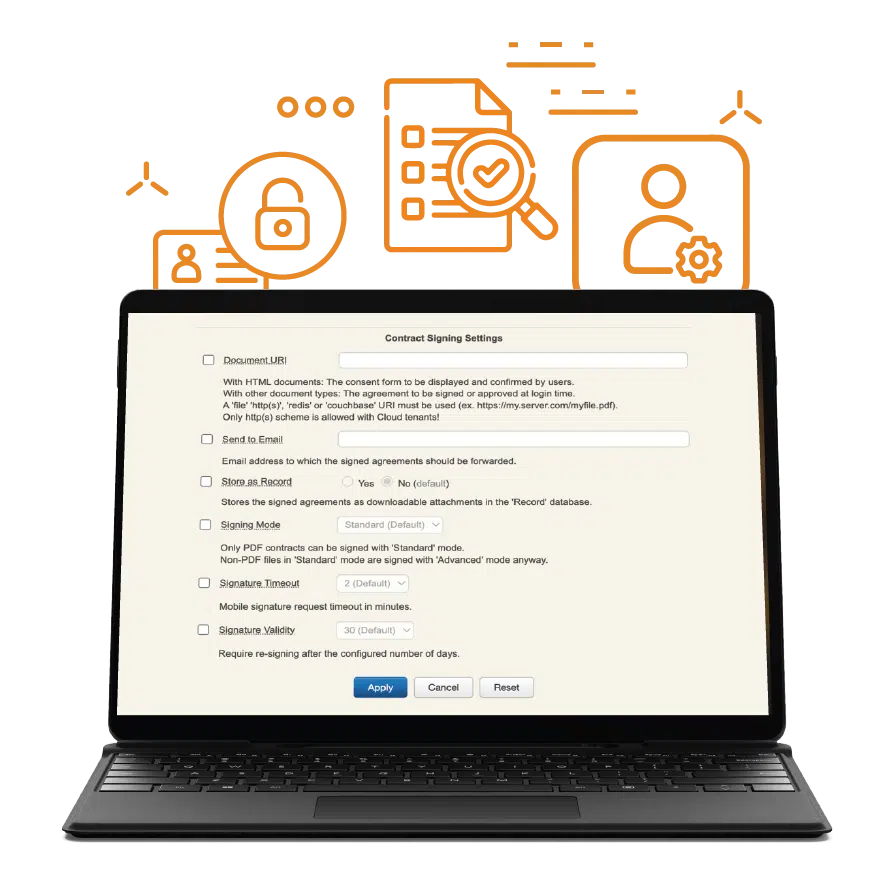
OpenOTP Security Suite is managed in the WebADM platform. It offers a robust solution to address compliance requirements effectively. This powerful Identity & Access Management (IAM) platform provides organizations with a comprehensive set of features and policies to ensure compliance with regulatory standards.
Companies can implement Multi-Factor Authentication, fine-grained access controls, and user provisioning policies that align with specific compliance mandates. This not only enhances security but also streamlines auditing and reporting processes, enabling organizations to demonstrate their commitment to compliance while safeguarding sensitive data and resources.
The paperless & timesaving capabilities of this integrated solution significantly reduce administrative overhead, making compliance efforts more efficient and cost-effective.
Unified IAM Federation
Native IAM Integration
OpenOTP is compatible with local directories such as Active Directory (AD) and LDAP, providing extensive support for on-premise environments. Additionally, it is natively integrated with EntraID, Okta, Google, Ping Identity, One Identity, and many other identity providers, enabling simple integration across diverse IAM systems.
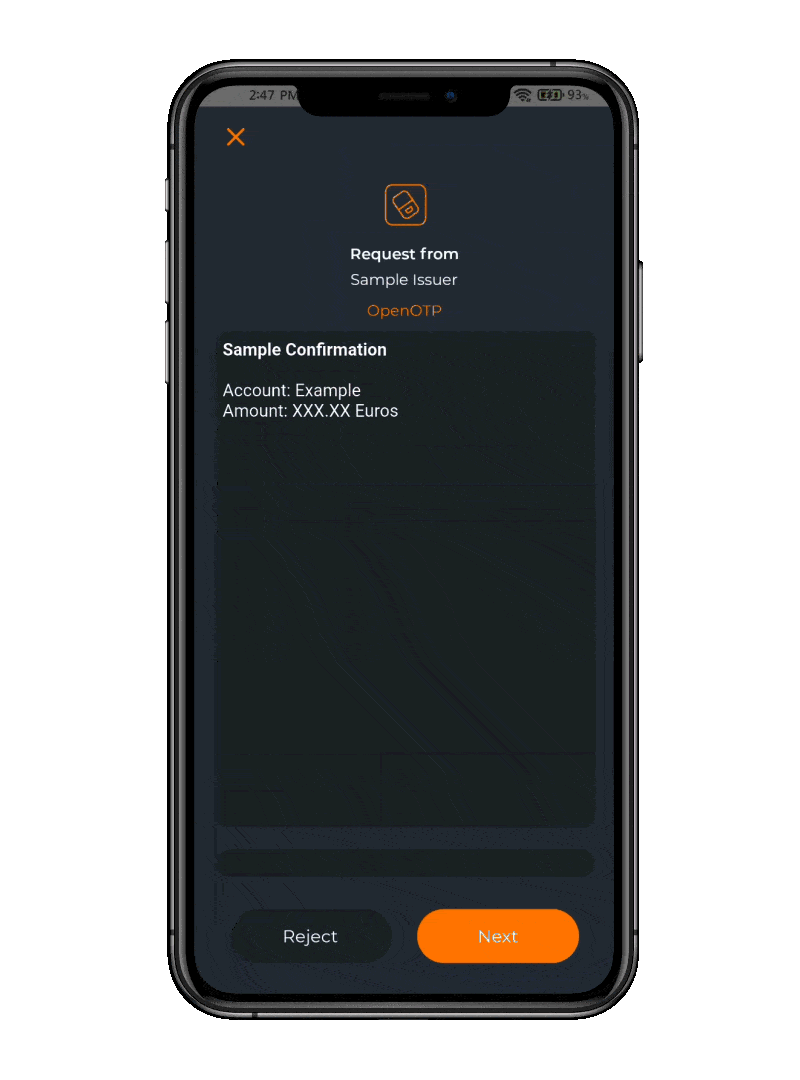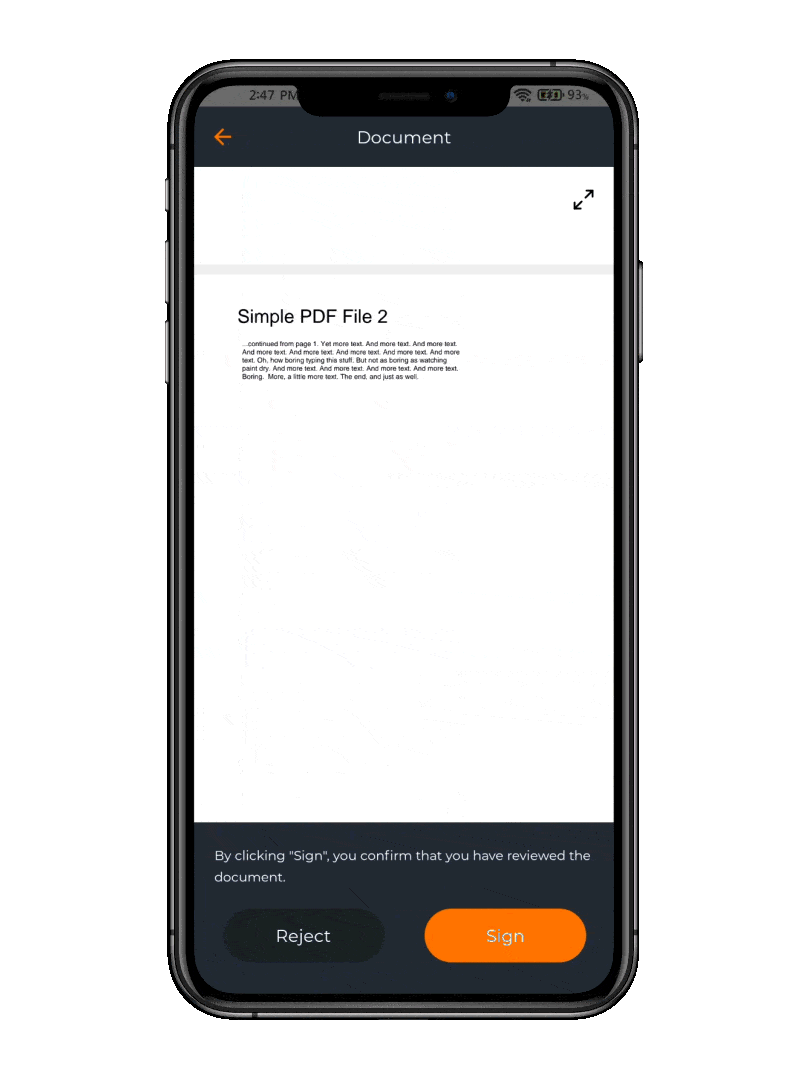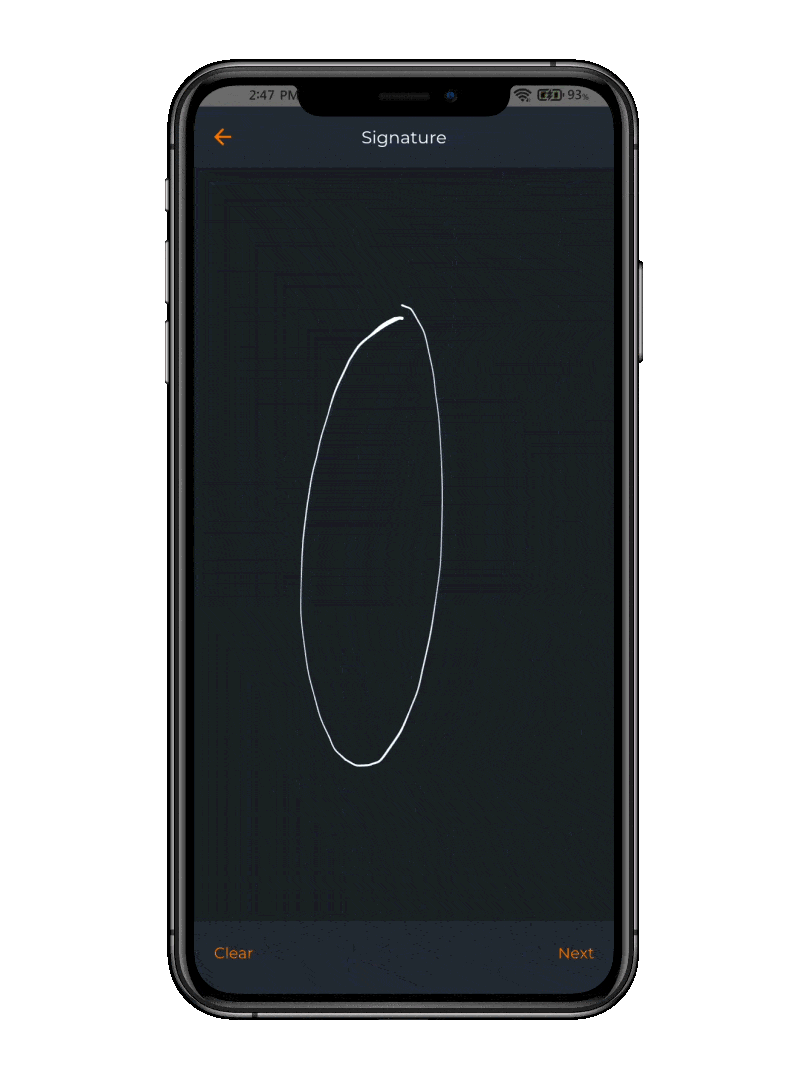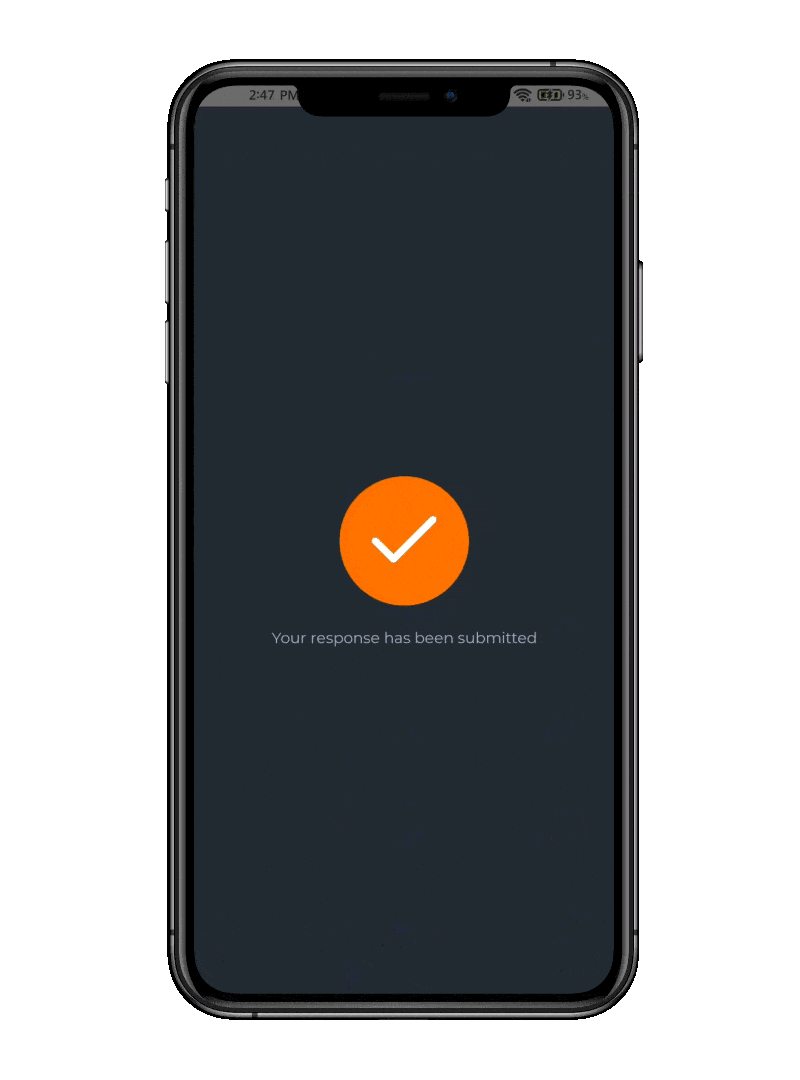
OpenOTP Token App
The free OpenOTP Token application offers a convenient solution for employees to receive Push Notifications as well as agreements to sign as part of the MFA process.
This app empowers users with the ability to securely authenticate and sign agreements via their mobile devices, eliminating the need for physical paperwork and cumbersome manual processes.
Its user-friendly interface and robust security features not only simplify document signing but also ensure the integrity and authenticity of these critical compliance records.
Since many organizations are already using it for Multi-Factor Authentication (MFA), this additional feature comes at no extra cost, providing an integrated and seamless solution for both security and compliance needs.
SEEING
IS BELIEVING
Whether you are buying a car or a security solution, you always want to test drive it before signing on the dotted line. We know this and you know this.
Contact us for your Free PoC or check it out for yourself.

