WebADM Self-Service and Help Desk
OpenOTP Self-Service & Help-Desk
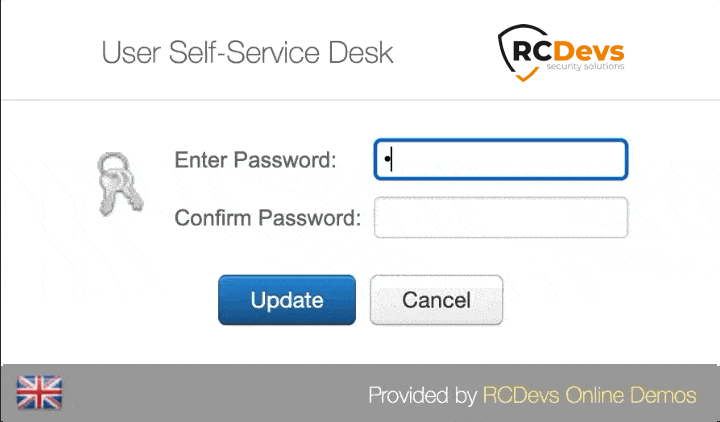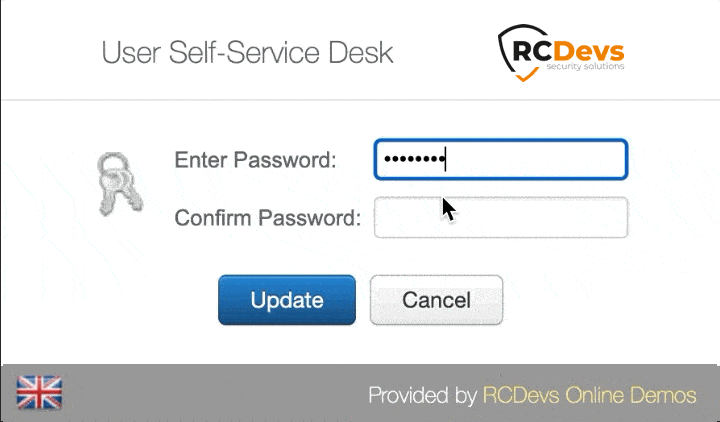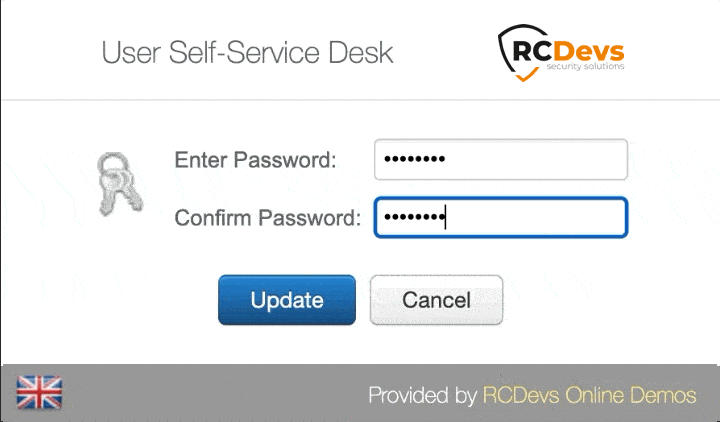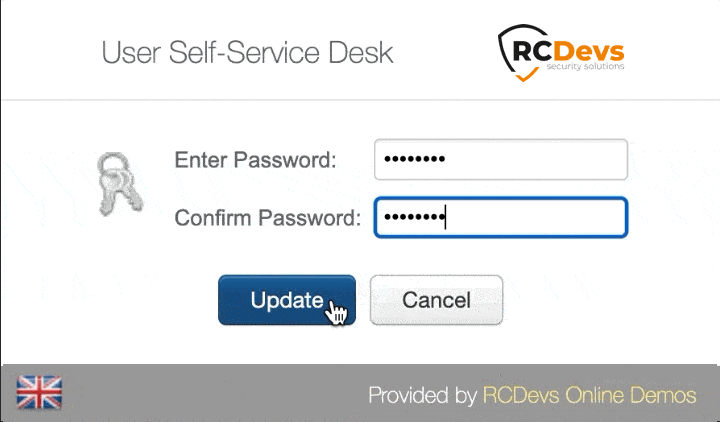
User Self-Service Desk
RCDevs Security solutions are provided with end-user helper applications (called WebApps) which are optional components in WebADM.
These applications are part of your security infrastructure. They simplify many of your help-desk processes by letting the users handle most of the self-management tasks (i.e. token enrollment or account/password management).
Web Apps are companion portals for your RCDevs’ Web Service applications. For example, in some use-cases, OpenOTP requires the end-users to enroll, test or resynchronize their tokens.
For public use, Web Apps can easily be embedded in your website or deployed on the Internet using RCDevs’ WebADM Publishing Proxy Server.
The Self-Service Desk is designed for internal (corporate) use and includes several self-management features as:
Manage account information such as email, mobile phone numbers, etc..
Reset LDAP password according to a configurable password policy
Enroll, re-synchronize and test Software / Hardware Tokens or Yubikeys
Manage user certificates
Receive an automatic link to renew a Token, Password, Certificate or SSH Key when they expire
Secure Password Reset
User Self-Registration
Administration Help Desk

Delegate the 1st line of support
Administration Help-Desk is another optional component in WebADM.
This web application provides an easy-to-use interface for the first level of IT Support function.
This web application must be installed on your WebADM server(s) and can be accessed through WAProxy or another reverse proxy configured with WebADM.

