RADIUS Bridge and VPN Security: MFA for third-party systems
OpenOTP Radius Bridge
Protect your Virtual Private Networks
OpenOTP RADIUS Bridge provides the RADIUS RFC-2865 (Remote Authentication Dial-in User Service) API for your OpenOTP server.
OpenOTP RADIUS is a very advanced system which is compatible with nearly all enterprise VPN appliances. It also provides EAP protocols for WiFi or NAC user authentication with WebADM PKI or OpenOTP MFA / FIDO.
Secure your VPN endpoint
RADIUS Bridge supports several password mechanisms to handle a two-factor authentication and by design, some One-Time Password methods like on-demand SMS-OTP work better with a challenge-response mechanism.
You can also choose whether the users should be challenged the OTP password after having entered their domain password or should enter the password and the OTP in a concatenated form.
RADIUS Bridge supports single-factor authentication with password-only or OTP-only too. The OpenOTP authentication policies are very flexible and can be configured on a per-client basis in WebADM. Moreover, the client policies can be contextual to the network or geolocation of the users accessing your systems.
This flexibility also provides support for integrations where the first factor is handled by your AD servers and the second factor (the OTP) is handled by your OpenOTP server.
The RADIUS standard is supported by all major security products on the market. You can also implement OpenOTP authentication methods for:
VPN Servers (Checkpoint, Cisco ISE/ASA, F5, Fortigate, Palo Alto…)
Microsoft VPN, TMG, UAG
Citrix (Access Gateway, XenApp, Netscaler)
VMWare View
NAC Enterprise Wifi (EAP-TLS/GTC, TTLS)
Radius-enabled Linux services (OpenVPN, Apache…)
SWIFT Alliance Access
And many others…
RADIUS integrations support all OpenOTP features
100% compatible with RADIUS standard (RFC-2865)
Robust implementation built-in with FreeRadius
Many integrations including enterprise Wifi
OTP with challenge-response or password concatenation
Supports any RADIUS vendor dictionary
Supports MS Domain-style login names (i.e. Domain\Username)
Supports MS User Principal Names
Supports OpenOTP contextual authentication
Per user and group reply attributes for VPNs (ACL, roles)
Authentication policies per client application or group of users
Bridges all the OpenOTP functionalities (Tokens, Yubikey, SMSOTP, MailOTP…)
Standalone service with no additional OpenOTP configuration required
High performance with hundreds of requests per second
Cluster support with multiple bridges for HA
VPN Authentication with OpenOTP and Radius Bridge
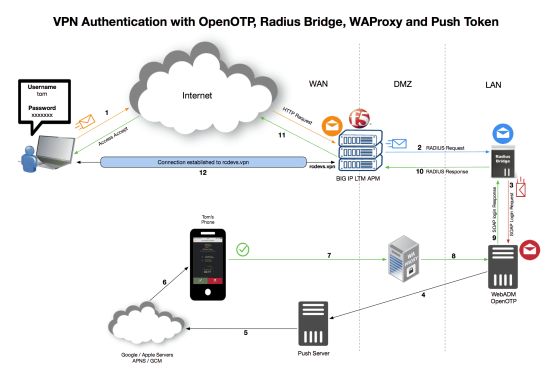
See below the OpenOTP RADIUS architecture diagrams. Scenario one shows a typical OpenOTP integration with an enterprise VPN server. Scenario two includes the WAProxy mobile-to-server communication component which is necessary to enable OpenOTP Push login with Approve/ Deny notifications.
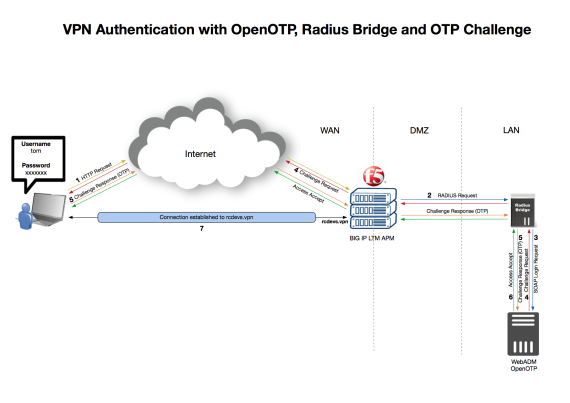
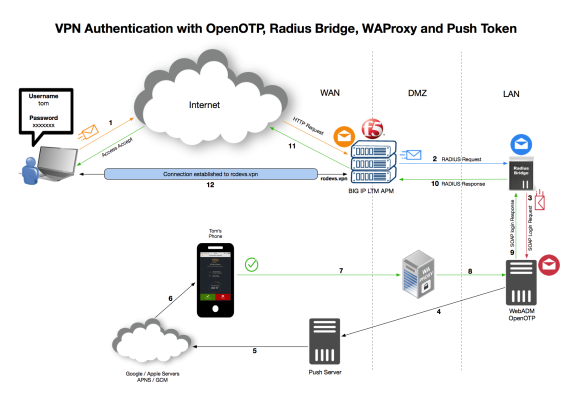
See how simple it is to use OpenOTP RADIUS Bridge:
Unified IAM Federation
Native IAM Integration
OpenOTP is compatible with local directories such as Active Directory (AD) and LDAP, providing extensive support for on-premise environments. Additionally, it is natively integrated with EntraID, Okta, Google, Ping Identity, One Identity, and many other identity providers, enabling simple integration across diverse IAM systems.
Choose the method that best suits you
Authentication Methods
RCDevs’ IAM-MFA Cybersecurity Solutions Compatible with Strong Authentication Login Technologies
SEEING
IS BELIEVING
Whether you are buying a car or a security solution, you always want to test drive it before signing on the dotted line. We know this and you know this.
Contact us for your Free PoC or check it out for yourself.

