
The Resurgence of DoS Attacks
The Resurgence of DoS Attacks
Protecting Your Enterprise against DoS with RCDevs’ New Brute-Force Protection
Despite advancements in cybersecurity, Denial-of-Service (DoS) attacks remain a significant threat to businesses, governments, and critical infrastructure. DoS attacks aim to overwhelm systems and disrupt services, making them a persistent challenge for organizations. While Distributed Denial-of-Service (DDoS) attacks, which involve multiple systems and are more dangerous, receive much attention, DoS attacks are equally disruptive and require robust mitigation strategies.
In response to the acknowledged increase in the volume and complexity of these attacks, we have developed a new feature called Brute-Force Protection, against Brute-Force and DoS attacks.
A Real Case Study: Illustrating a DoS Attack on One of Our Clients
Here at RCDevs, we understand the critical impact of DoS attacks firsthand. One of our clients, a large enterprise, frequently faced DoS attacks targeting their Active Directory (AD). These attacks involved a barrage of connection attempts searching for non-existent users. And with hundreds connection attempts per second sustained for an hour, the sheer volume of requests overwhelmed their AD, causing it to freeze and become unavailable for legitimate user authentication.
To address Denial-of-Service (DoS) attacks that exploit brute-force login attempts, RCDevs has developed a new “brute-force protection” feature within WebADM.
Protecting Active Directory from DoS Attacks with RCDevs
This situation highlights the need for a robust DoS mitigation strategy specifically designed to protect AD from such attacks. Traditional security measures like firewalls aren’t sufficient to address the unique challenges of brute-force attacks targeting AD.
The Challenge: WebADM Can Handle It, But AD Can’t
WebADM, our flagship security solution, is resilient and can handle thousands of requests per second. However, your AD infrastructure couldn’t withstand the relentless fraudulent user searches.
RCDevs’ Brute-Force Protection: Mitigating DoS Attacks with WebADM
Our new feature within the WebADM platform, Brute-Force Protection, is designed to detect and mitigate DoS attacks, ensuring the resilience and availability of critical enterprise services.

How It Works
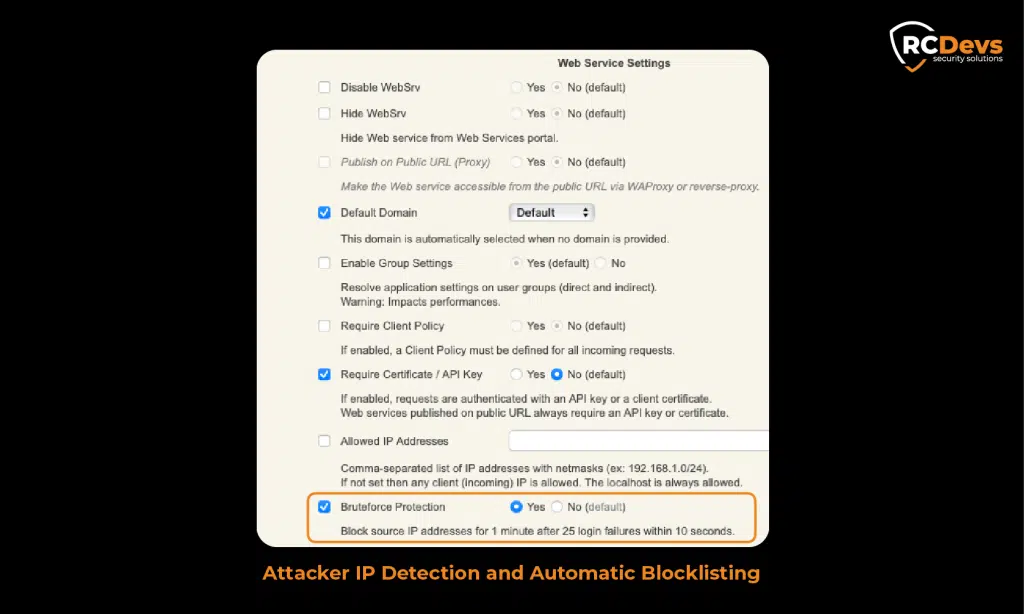
Attacker IP Detection and Automatic Blocklisting
The system identifies attacking IP addresses and automatically blocklists them, preventing further malicious attempts. It employs rotating counters of IPs per system to manage and update blocklists dynamically.
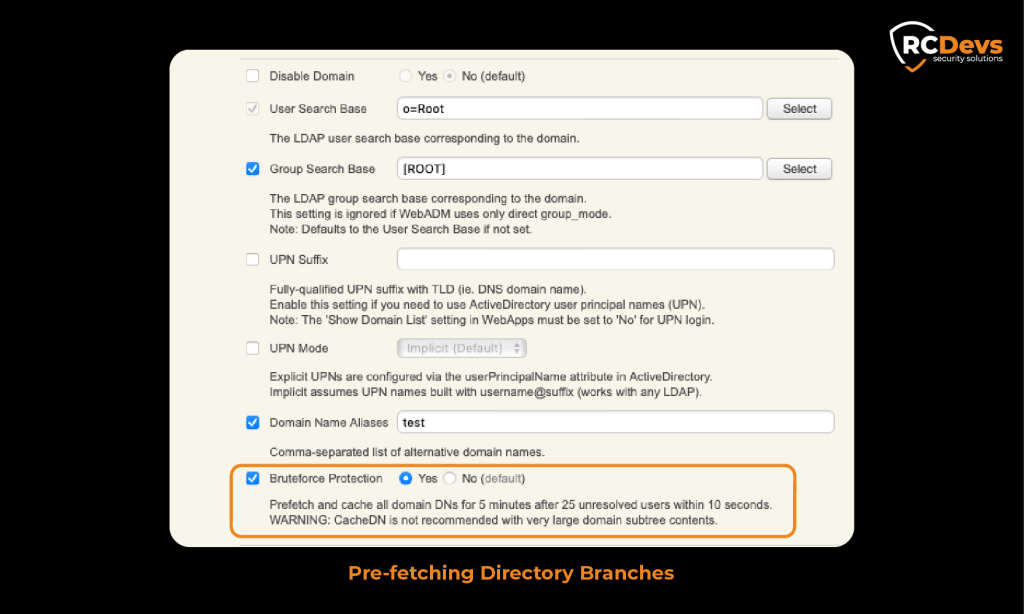
Pre-fetching Directory Branches
When multiple unsuccessful user searches are detected, the system initiates a pre-fetching mechanism. After 25 unsuccessful attempts within a 10-second window, WebADM pre-fetches the concerned AD branch for 5 minutes, loading the relevant directory portion into memory. This reduces the load on the AD system, preventing it from freezing and allowing legitimate users to access directory services without interruption.
Prefetching works with limited branches so as not to create too large AD requests with an instant impact on the Active Directory. Moreover, prefetching is done in a “mutex” mode which spools incoming request at cluster level during branch prefetch (not to overload AD with multiple prefecting at the same time).
Activation and Integration
Activating Brute-Force Protection in WebADM is straightforward. Administrators can enable the feature through the WebADM console. Integration with existing directory services is seamless, requiring minimal configuration changes.
Settings to activate Brute-Force Protection in WebADM under Admin:
Benefits of RCDevs’ Brute-Force Protection
By implementing Brute-Force Protection, organizations gain significant advantages:
- Enhanced AD Security: WebADM shields Active Directory from brute-force attacks, safeguarding user authentication.
- Reduced Downtime: Mitigating DoS attacks ensures continued availability of critical resources, minimizing downtime.
- Improved Efficiency: Intelligent caching of frequently accessed AD data reduces overall system load.
Facts and Trends about DoS
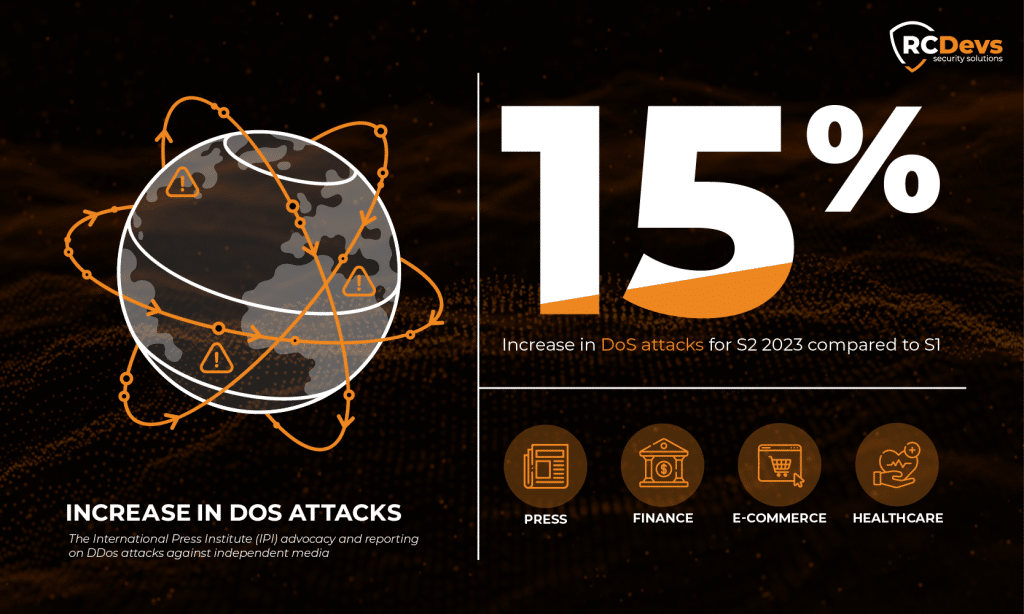
Increase in Attack Volume and Complexity
Recent reports for S2 2023 indicates a 15% increase in DoS attacks compared to S1, with significant impacts on industries like finance, healthcare, and e-commerce. These attacks are becoming more sophisticated, leveraging advanced techniques to bypass traditional security measures.
Geopolitical Tensions
Geopolitical tensions have driven the surge in DoS attacks, with state-sponsored groups and hacktivist collectives using these attacks for retaliation or to further political agendas. A notable example is the attack on the European Parliament’s website in November 2022, attributed to the Russia-linked group Killnet.
The media and independent journalism have also become prime targets for DDoS attacks, posing a severe threat to press freedom and the free flow of information.
How Do DoS Attacks Work?
Attackers often use botnets, networks of compromised computers, to generate the massive traffic volumes required for DoS attacks. Tools such as LOIC (Low Orbit Ion Cannon) and HOIC (High Orbit Ion Cannon) are frequently used to launch these attacks. More sophisticated attackers might employ reflection and amplification techniques, where they use legitimate services to amplify their attack traffic, making it even harder to mitigate.
As for DDoS attacks, they are executed through several stages and involve various techniques:
- Botnet Creation: Attackers infect multiple devices with malware, turning them into bots that can be remotely controlled. These devices could be computers, IoT devices, or any Internet-connected device.
- Command and Control (C&C) Server: The attacker controls these bots via a C&C server, coordinating the attack and directing the bots to target a specific IP address or service.
- Traffic Overload: The bots generate an overwhelming amount of traffic to the target, which could be in the form of connection requests, malformed packets, or massive data payloads.
- Service Disruption: The target system becomes inundated with this traffic, exhausting its resources and causing it to become slow or completely unresponsive to legitimate requests.
Types of DoS Attacks
DoS attacks can be categorized based on the nature of the traffic they generate and the vulnerabilities they exploit:
Volume-Based Attacks: These attacks aim to saturate the bandwidth of the target site. Examples include UDP floods, ICMP floods, and other spoofed-packet floods. The magnitude of these attacks is measured in bits per second (bps).
Protocol Attacks: These attacks exploit weaknesses in the network protocol stack, causing service disruption by consuming server resources or intermediate communication equipment. Examples include SYN floods, fragmented packet attacks, Ping of Death, and Smurf attacks. These attacks are measured in packets per second (pps).
Application Layer Attacks: These attacks target the application layer, the topmost layer of the OSI model, aiming to disrupt specific features or functions of a website. Examples include HTTP floods, Slowloris, and DNS query floods. These attacks are measured in requests per second (rps).
The Impact on Enterprises
DoS attacks can severely disrupt enterprises, leading to financial losses, damage to brand reputation, operational disruption, and in some cases, data breaches. Protecting against these attacks is crucial to maintaining business continuity and customer trust.
- Financial Loss: Businesses can incur significant costs due to downtime, lost revenue, and the expenses associated with mitigating the attack.
- Reputation Damage: Prolonged or repeated service disruptions can erode customer trust and damage a company’s reputation.
- Operational Disruption: Critical services may be rendered unavailable, impacting business operations and service delivery.
- Data Breaches: In some cases, DDoS attacks serve as a smokescreen for other malicious activities, such as data theft or malware insertion.
Conclusion
The rise in DoS attacks poses a significant threat to enterprise security, necessitating advanced and adaptive defense mechanisms.
RCDevs’ Brute-Force Protection within WebADM offers a powerful solution, combining intelligent detection, automatic blacklisting, and innovative pre-fetching techniques to safeguard critical directory services.
By offloading attack traffic and protecting Active Directory, WebADM ensures enterprises can maintain service availability and operational continuity in the face of escalating cyber threats.

