
Mobile Authentication for Enterprise Security
Mobile Authentication for Enterprise Security
What is Mobile Authentication for Enterprise?
Mobile Authentication for Enterprise provides secure access for Websites, VPNs, Citrix, Cloud Apps, Windows, Linux, SAML, OpenID, Wifi, and much more.
An authenticator app is installed on your smartphone and produces a string of 6-8 digit code every time the user tries to log in with an MFA-enabled application. They have to put the code generated to access the data or application.
Authenticator Apps are used to protect oneself and the enterprises from password theft and other types of cyberattacks like data breaches. Also, it helps to comply with regulatory requirements like GDPR to protect sensitive data.
How do Authentication Apps work?
Generally, the authenticator apps work on a shared secret key known by the server and the authenticator app.
Once the user downloads the application:
1)A QRCode is generated by the server containing the Token information (Token type i.e. TOTP, HOTP, OCRA, the key algorithm, Secret key and the Key format, token expiration date, etc.). Based on this information, the authenticator app generates valid One-Time Passwords.
2)The user will then be able to register its token by scanning the QRCode through the authenticator application.
The same information is registered on the OTP server side for that user, that way, the server will be able to validate the OTP generated by the Token and provided by the user during the login purposes.
How does Push Authentication work?
After registering the token, the app follows the same mechanism as above.
The main difference in Push Authentication is during the enrollment purpose, the mobile will respond to the server with extra information like the mobile Push ID which is unique per device and which allow the authenticator provider to send “Push Notifications” on the destination device.
When a login process is started for a user:
1)A notification is sent to its device.
2) The user clicks on the notification, the authenticator application opens and then the user is prompted to approve or deny the authentication request pending on a 3rd party system/application.
3)By clicking on the ‘Approve’ button, the current OTP code is automatically picked up and sent to the OTP server.
4)The server validates the OTP provided through the mobile response (approve) and then the user is authenticated.
If the user declines the authentication request, the OTP is not forwarded to the authentication backend, the server can not validate the OTP code and then the authentication attempt on the 3rd party system/application is refused.
Note: authenticator apps are not tied in any way to your SIM card or phone number, and that’s a good thing.
RCDevs- Free Mobile Authentication App
RCDevs’ OpenOTP Authentication Server provides the most advanced user authentication system supporting simple registration with QR Code scan, Software Token based on OATH standards, and Approve/ Deny login with push notifications.

For complete documentation on how to install and configure, check this.
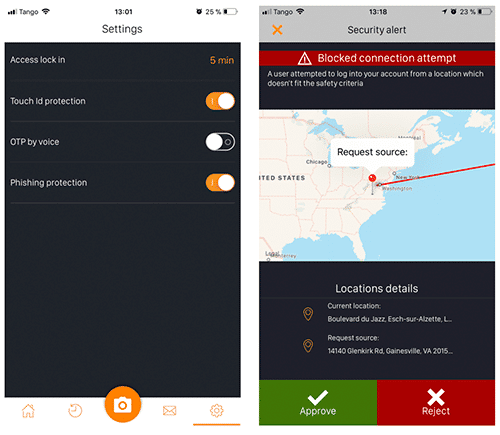
When you are in the OpenOTP Token application, some settings can be defined in the configuration menu:
- Access lock-in: This is the time after which your password will be asked to unlock the application.
- Biometric protection: Instead of using a passcode to unlock the application you can use the biometric functionality available on your phone (Touch ID or Face ID).
- OTP by voice: The OTP code will be spelled.
- Phishing protection: Phishing protection will use your location to prevent phishing attacks. If a phishing attack is suspected, the OpenOTP Token application will prompt you with a screen like below.
With RCDevs’ Mobile Authentication App/ OpenOTP Token you can secure your enterprise with Strong Authentication and do digital signature, which is legally binding.

