
Strengthening IT Security Through Good Infrastructure Hygiene
Strengthening IT Security Through Good Infrastructure Hygiene
Maintaining clean, organized, and up-to-date infrastructure is a key aspect of a secure and resilient IT environment. Infrastructure and system hygiene refers to the ongoing practice of managing systems, networks, and data effectively to minimize security vulnerabilities and prevent operational issues. As highlighted in NIST SP 1800-31, neglecting proper system maintenance can lead to cybersecurity risks, data breaches, and costly downtime—issues that can be devastating for an organization’s reputation and bottom line. Let us explore the cybersecurity risks associated neglected system upkeep and some strategies for improving it, especially through centralized management.
Why Infrastructure Hygiene is Critical for Security
Maintaining well-structured infrastructure is closely tied to cybersecurity, as well-maintained systems are less susceptible to security incidents. Systems that are regularly updated, standardized, and monitored are better equipped to handle threats, making it difficult for unauthorized access or malware to exploit known weaknesses. Patching systems promptly, as recommended in NIST guidance, is one of the most effective measures to close security gaps. Here’s how maintaining infrastructure standards strengthens cybersecurity:
- Prevents Vulnerabilities: Systems that are routinely patched and updated are far less likely to have exploitable vulnerabilities. Maintenance practices such as consistent versioning, up-to-date security patches, and standardized configurations help ensure systems aren’t an easy target.
- Reduces Unauthorized Access: When cyber hygiene practices include robust identity management and well-defined access policies, organizations can better manage who has access to which systems, minimizing the risk of unauthorized access.
- Increases Incident Response Efficiency: With organized and well-documented systems, identifying the root cause of incidents or security breaches is much quicker, allowing security teams to act decisively to contain and resolve threats.
- Mitigates Risks in Complex Environments: For organizations with multiple systems or recent acquisitions, Strong maintenance practices streamline integrations, standardize configurations, and reduce misconfigurations that could otherwise lead to security gaps.

Common Causes of Subpar System Hygiene
Ensuring consistent system upkeep is essential but often challenging. Many organizations struggle due to a range of issues that hinder consistency and increase security vulnerabilities. The following challenges, as detailed in NIST SP 1800-31, are common obstacles to robust system maintenance:
- Legacy Systems and Technical Debt
Older systems can be difficult to update or integrate with modern technology, accumulating technical debt and security vulnerabilities over time. - Rapid Growth or Expansion
Fast expansion, especially through acquisitions, can lead to fragmented systems with inconsistent standards, making management and security difficult. - Lack of Documentation and Training
Insufficient documentation leaves IT teams without crucial knowledge, leading to confusion, slow troubleshooting, and greater potential for errors. - Inconsistent Standards Across Departments
Different departments using unique configurations or policies create security gaps, complicating consistent policy enforcement and system management. - Lack of Centralized Management Tools
Without centralized tools, managing updates, access, and configurations is time-consuming and error-prone, increasing the risk of security lapses. - Limited IT Resources and Budget Constraints
Overburdened teams and restricted budgets often mean delayed maintenance and updates, allowing unpatched vulnerabilities and inconsistent access controls to persist.
Key Practices for Improving Infrastructure Hygiene
Adopting structured maintenance practices becomes increasingly important. As NIST recommends, organizations should prioritize the following strategies to improve system hygiene:
- Adopt a Centralized Management System: Start by consolidating all systems, applications, and user management protocols under one centralized management platform. This consolidation will allow for consistent access control, easier tracking of system health, and uniform application of security policies.
- Standardize Naming Conventions and Configurations: Establish and enforce clear standards for naming conventions, configuration settings, and versioning formats. This should extend to identifiers, dates, and numeric formats so that all systems use a common language, simplifying integration and minimizing misconfigurations.
- Implement Role-Based Access Control (RBAC): Limit user access to only the systems or data necessary for their role, and regularly audit these permissions to ensure that they are current. This practice reduces exposure to insider threats and minimizes the impact of compromised accounts.
- Automate Patching and Updates: Automation is critical for ensuring patches are applied promptly and systematically across all systems. NIST highlights that automated patching tools reduce human error and accelerate response times.
- Conduct Regular Security Audits and System Reviews: Regularly audit systems to verify adherence to maintenance standards and ensure that security protocols are effective. Audits should cover user permissions, system configurations, patch levels, and documentation accuracy.
- Enforce Multi-Factor Authentication (MFA) Across Systems: Multi-factor authentication is one of the simplest and most effective ways to improve security posture. Applying MFA across all systems, and using a centralized management system to enforce this policy, significantly reduces the risk of unauthorized access.
Addressing System Hygiene with Centralized Management: RCDevs’ OpenOTP
Centralized management solutions like OpenOTP from RCDevs may not address every challenge tied to suboptimal infrastructure practices, but they significantly help eliminate most of them. The platform supports Identity and Access Management (IAM), centralized authentication, and multi-factor authentication, enabling organizations to better manage access and enforce security policies consistently. These features align with NIST‘s emphasis on the importance of securing patch management tools and ensuring robust access controls.
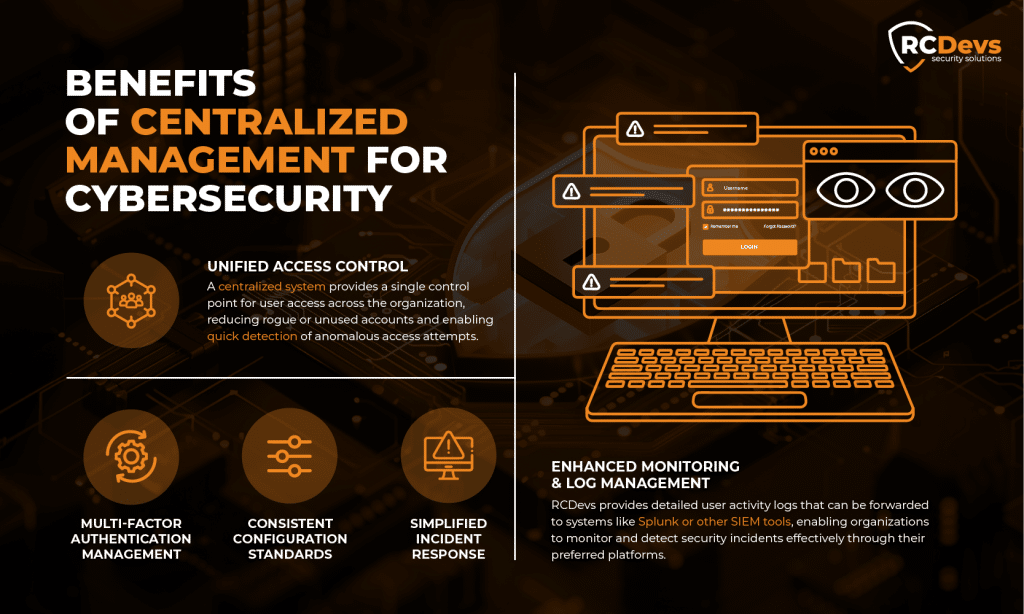
- Unified Access Control and Consistent User Management: RCDevs centralizes user authentication across systems, reducing risks from dormant accounts and ensuring consistent access policies. This includes establishing standardized user access management across departments and reducing vulnerabilities caused by poorly managed permissions.
- Federated Identity and Single Sign-On (SSO): Enable secure, seamless access to multiple systems with a single login, simplifying user management and enhancing security across the organization.
- Streamlined Multi-Factor Authentication (MFA): Enforce MFA policies across all systems to add a critical security layer, allowing even legacy systems to benefit from enhanced protection without requiring major overhauls.
- Centralized Management and Simplified Configurations: With tools like One-IAM, RCDevs provides centralized identity and access management, enabling organizations to manage all configurations through a single platform while ensuring uniform security standards across departments.
- Legacy Systems and Technical Debt: RCDevs integrates MFA into legacy systems to secure critical assets that would otherwise remain vulnerable, addressing system hygiene without removing existing technical debt.
- Scalability and Growth: RCDevs supports organizations in scaling their security infrastructure to meet the demands of rapid growth or expansion through solutions like One-IAM.
- Affordable and Hosted Solutions: RCDevs offers cost-effective security enhancements with affordable pricing and hosted options, helping organizations secure their infrastructure without exceeding budget constraints.
- Enhanced Monitoring and Log Management: RCDevs provides detailed user activity logs that can be forwarded to systems like Splunk or other Security Information and Event Management (SIEM) tools, enabling organizations to monitor and detect security incidents effectively through their preferred platforms.
RCDevs’ OpenOTP provides a comprehensive solution to support organizations in maintaining good system hygiene and cybersecurity, particularly for those operating in complex or multi-system environments. By centralizing the management of user access, authentication, and monitoring, these tools help organizations resolve key maintenance challenges and reduce their exposure to cyber threats.
Strengthening Resilience Through Centralized Management
Maintaining robust system upkeep and operational standards is critical for a secure and resilient IT environment. Disorganized system upkeep—such as inconsistent configurations, outdated patches, or insufficient access control—not only complicates operations but also increases the risk of security vulnerabilities. By adopting a centralized management approach, organizations can more effectively enforce hygiene practices, simplify management, and strengthen their cybersecurity defenses.
Tools like OpenOTP Security Suite from RCDevs Security provide robust support for centralized system management, addressing key areas such as Identity and Access Management (IAM), Identity Provider (IdP) services, and multi-factor authentication (MFA). Organizations can federate identities across systems, ensuring that access policies are applied consistently across diverse environments. These tools also streamline the management of user permissions and authentication processes, helping organizations enforce robust security practices across multiple systems and user groups. With features like single sign-on, centralized federation, and MFA, OpenOTP provides a comprehensive solution for organizations seeking to maintain strong infrastructure hygiene and secure access to critical systems.
To see how RCDevs’ OpenOTP can transform your IT infrastructure and security practices, contact us today or request a demo.

