Why Mobile Badging is the future of time-clocking? (and a great path towards 3FA)
The evolution of regulations and the generalization of remote work are posing new constraints for HR departments, particularly in the case of cross-border employees. Existing time clock systems partially respond to this new situation as well as companies’ obligation to provide legal proof. RCDevs Security …
RCDevs’ OpenOTP Token App vs Google Authenticator
RCDevs’ OpenOTP Token App and Google Authenticator both provide OTPs (One Time Passwords) for Multi-Factor Authentication (MFA), for your servers and accounts. A time-dependent multi-digit code is generated, which is entered when prompted, once you have submitted your username and password. Google Authenticator is a …
Evolving CyberThreats
In the past two years, the increase of ransomware with high values and the emergence of malicious software supply chain vulnerabilities have raised security to the forefront of the list for government officials. In contrast to 20 years ago, when even extensive IT systems were …
Exciting New functionality: FIDO2 for Windows Credential Provider
OpenOTP Security Suite is 100% FIDO2 compatible. This means you can log in to your Windows computer with FIDO2 ready USB keys or devices, as you previously did with FIDO U2F Keys. What is FIDO2? FIDO2 enables users to easily authenticate to the online services …
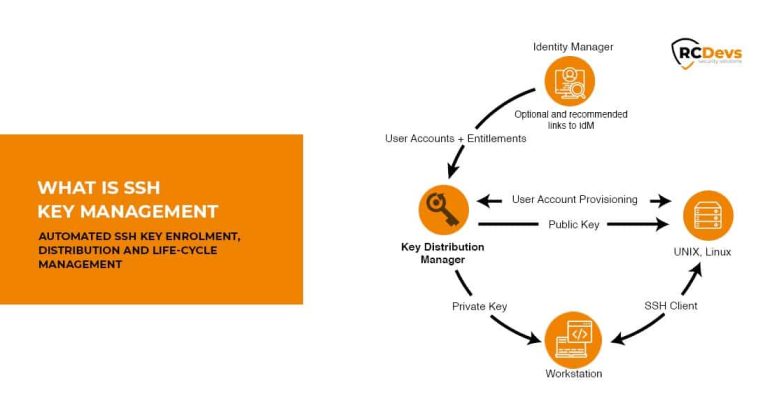
What is SSH Key Management- Latest Update
What is SSH Key Management SSH i.e. Secure Shell is a cryptographic network protocol that is a set of rules for transferring encoded data over the Network. Why do you need SSH? Easier to Use. Safer as Username and Password can be stolen by a …
Could Federated Identity Management become a standard?
Traditional approaches to identity management show their limitations. In this context, many organizations are turning to identity federation to facilitate user work across multiple systems, while reducing the administrative burden of managing access to these systems. …
We are proud to be in good company
We are proud to be in good company for Cybersecurity and authentication. Thanks to @The_LHoFT with support from @ALFIfunds, …
Federated Identity Management becomes a standard
Using the profit accumulator is one such way, and you should understand why it increases your chances of the profits. …