What is SSH Key Management- Latest Update
What is SSH Key Management- Latest Update
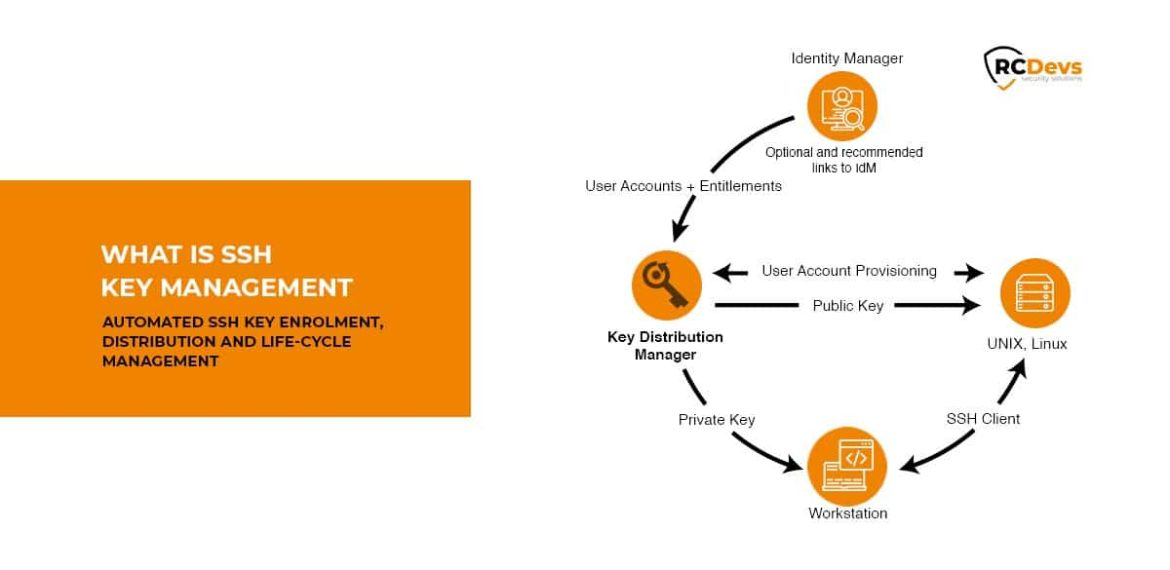
What is SSH Key Management
SSH i.e. Secure Shell is a cryptographic network protocol that is a set of rules for transferring encoded data over the Network.
Why do you need SSH?
- Easier to Use.
- Safer as Username and Password can be stolen by a man in the middle attack.
- Symmetrical encryption can’t be done on Remote Servers and SSH uses Asymmetric Cryptographic.
Who can Access it and Where?
Like with any method of authentication, SSH logins are governed by corporate IAM, which in the simplest form answers the question of who can access and where? Usually, the source of trust for this is the corporate LDAP, Active Directory (AD) in many cases, which hosts the relation between identities and their allowed locations of access.
With SSH keys this landscape is however very different: there is no single source, but instead, authorization information is distributed across the Unix/Linux server itself. If a company hosts 100 servers, then this equates to that there are 100 individual decision (or breach) points for access. As one access can lead to another, the real figure can be much larger.
Problems faced by Organisation using SSH Key
The problem many organizations face today is that their IAM solutions do not support SSH keys as a method of login. Technically speaking, the existing IAM solutions are unable to bridge the gap between numerous authorizations within a Unix/Linux server estate and the identities and authorizations found within the centrally managed AD/LDAP.
Many, or even all, Unix and Linux logins go ungoverned, without the ability to determine which key belongs to which identity and if the access is in breach with company IAM guidelines. In practice, this means that an unknown identity may log in with a key that is not even known to exist. To make things even worse, SSH logins are generally for privileged access, the most critical form of access.
Solution: Centrally Manage your SSH Key
RCDevs SpanKey is a centralized SSH key server for OpenSSH where the public keys are stored in your central LDAP directory (ex. Active Directory). With SpanKey there is no need to distribute, manually expire, or maintain the public keys on the servers. Instead, the SpanKey agent is deployed on the servers and is responsible for providing the users’ public keys on-demand. SpanKey server provides per-host access control with “server tagging”, LDAP access groups, centralized management from the RCDevs WebADM console, shared accounts, privileged users (master keys), recovery keys. It supports public key expiration with automated workflows for SSH key renewal (via Self-Services).
Easy Key Enrollment with Self-Services, Graphical session recording, Automatic public key expiration, Support for shared Account is to name a few features in SpanKey.
Click here to understand the Features and Architecture of SpanKey.


