Next-Gen IAM Management for Mixed Cloud & Enterprise AD: The RCDevs Approach
Next-Gen IAM Management for Mixed Cloud & Enterprise AD: The RCDevs Approach
In today’s hybrid infrastructure landscape, identity and access management (IAM) is a complex and ever-moving target. Enterprises rely on a mix of on-prem Active Directory (AD), cloud IAMs like Azure Entra ID, Okta, Ping, OneLogin, and DUO, and increasingly, customer-facing identity stores running over SQL or SCIM-based services. Consolidating and managing all these moving parts is a painful, costly, and often error-prone process. This frequently leads to gaps in security and compliance. RCDevs WebADM unifies decentralized IAMs into one federated hub — no merging, no migration, just smart, centralized control, a game-changing approach that goes beyond simple authentication and into IAM federation without compromise.
More Than Just MFA and SSO
RCDevs WebADM is already known in security circles as a comprehensive platform providing:
- Multi-Factor Authentication (MFA)
- SSO and Web Identity Federation
- Privileged Access Management (PAM)
- PKI and certificate-based access
- Network Access Control (NAC)
- Context-aware access rules
But here is the thing: most people do not know that RCDevs WebADM can act as a central IAM hub, capable of integrating multiple decentralized IAM services into a single, federated meta-directory. It does not just “connect” them — it understands them. It manages them. It consolidates control without merging or migrating.
A Meta-IAM for a Decentralized World
At the heart of this new-gen architecture is the WebADM meta-directory — a centralized abstraction layer that brings together identity information from multiple IAM services:
- Microsoft Active Directory (on-prem)
- Azure Entra ID
- Okta
- Ping Identity
- OneLogin
- DUO
- SCIM-compliant directories
- SQL-based user databases
Once connected via lightweight connectors, WebADM builds a meta-IAM: a logical entity composed of multiple IAMs. From there, administrators can define meta-groups — user groups that span IAM boundaries — and design fine-grained access policies for apps, VPNs, PKI, Windows logins, PAM systems, and more.
No sync storms. No migration headaches. No duplicated identities.
Just one logical view over many systems — updated in real time, with full support for cross-IAM authorization.
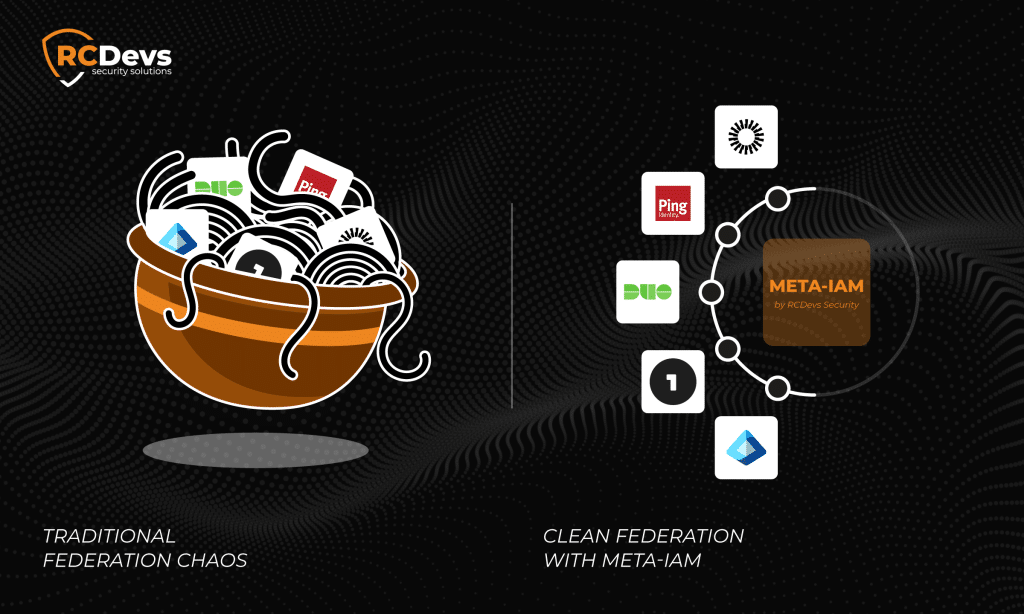
Federation Without the Cascading IdPs
Traditional IAM federation relies on chaining or cascading identity providers (IdPs) using SAML, OIDC, or LDAP referrals. That model quickly becomes a spaghetti mess when you have multiple IdPs across subsidiaries, partners, and business units.
WebADM flips that on its head.
There is no need to cascade or nest identity providers. Instead, each IAM remains autonomous and untouched. RCDevs’ connectors pull necessary identity and group info into the meta-IAM layer, where global policies and access control rules are enforced.
That means each system — whether a cloud IAM, legacy AD, or SQL user store — continues to function independently. But to the applications and services consuming identity from WebADM, it is all one clean, logical model.
Build Meta-Domains and Cross-IAM Access Groups
With WebADM, you can create meta-domains — logical entities that group multiple IAMs under a single umbrella. Then you can define meta-groups that span those domains.
Example use case:
- Combine users from Entra ID (corporate cloud), on-prem AD (legacy users), and a partner’s Okta instance.
- Place selected users from each in a meta-group: SecureFinanceOps.
- Apply a single access policy to that meta-group to control access to a VPN, internal dashboards, and PKI-based email signing.
This kind of cross-IAM group policy is normally the holy grail of IAM strategy — and RCDevs delivers it without data migration, synchronization pain, or IdP sprawl.

Zero-Footprint, Bi-Directional Sync
By default, WebADM operates in a zero-footprint mode — it does not modify the connected IAMs. But if you want more control, it also supports one-way or two-way sync, enabling centralized user and group provisioning.
In two-way mode, WebADM becomes a master IAM manager across all systems. You can:
- Move or copy users between IAMs
- Retain passwords, MFA/FIDO credentials, and group memberships
- Automatically propagate identity changes
Example: You can move a user from Okta to AD with a click — and WebADM handles the rest, preserving credentials, MFA enrollment, and even password hashes thanks to its IAM metadata layer.
Temporary Access and Smart Federation
One of the most powerful features of RCDevs WebADM is its temporary federation capability.
Let us say you have a consultant from Company A who needs access to internal services at Company B for a short project. With WebADM, you can:
- Temporarily copy the user to Company B’s IAM (or a federated group)
- Include password + MFA details
- Set an auto-expiry date
- Apply scoped access policies
That is it. The user has simple access for the duration of the project, and everything is cleaned up automatically after.
Beyond Enterprise: Hybrid IAM for Banks, Telcos, and Complex Orgs
Many modern orgs have IAM sprawl beyond just AD and cloud.
Think:
- Banks with AD + Entra ID + customer databases
- Telcos managing thousands of devices tied to SQL user stores
- Conglomerates onboarding new companies with incompatible IAMs
WebADM connects all of these into a coherent, secure, and policy-driven architecture.
You get:
- Role-based access over disparate identity systems
- Uniform policy enforcement regardless of source
- Real-time federation with zero duplication
It is IAM federation for the real world — one that accepts messiness and builds clarity on top of it.
The Future of IAM Is Not Migration. It is Federation.
The IAM industry has long been obsessed with consolidation via migration — merging directories, collapsing IdPs, syncing users into single stores. That is slow, expensive, and inherently fragile.
RCDevs WebADM offers something much smarter: consolidation by federation.
By enabling IAMs to work together, it removes the need for painful merges or duplications. You get the best of both worlds — autonomy for each business unit or department, and global visibility and control from the top.
For organizations with hybrid cloud/on-prem setups, multiple subsidiaries, or B2B integration needs, this is a massive leap forward.
Final Thoughts
RCDevs WebADM is not just an authentication tool. It is a next-gen IAM platform that redefines how large organizations think about identity — from rigid silos to dynamic, federated graphs of trust.
If you are dealing with a mix of cloud IAMs, legacy ADs, or SQL identity databases and you are looking for a clean, cost-effective way to unify control without disrupting autonomy, it is time to look beyond traditional SSO stacks.
IAM is no longer just about authentication. It is about orchestration. And RCDevs is leading the charge.

