WebADM: Complete IAM Solution for LDAP Organizations
IAM Solution
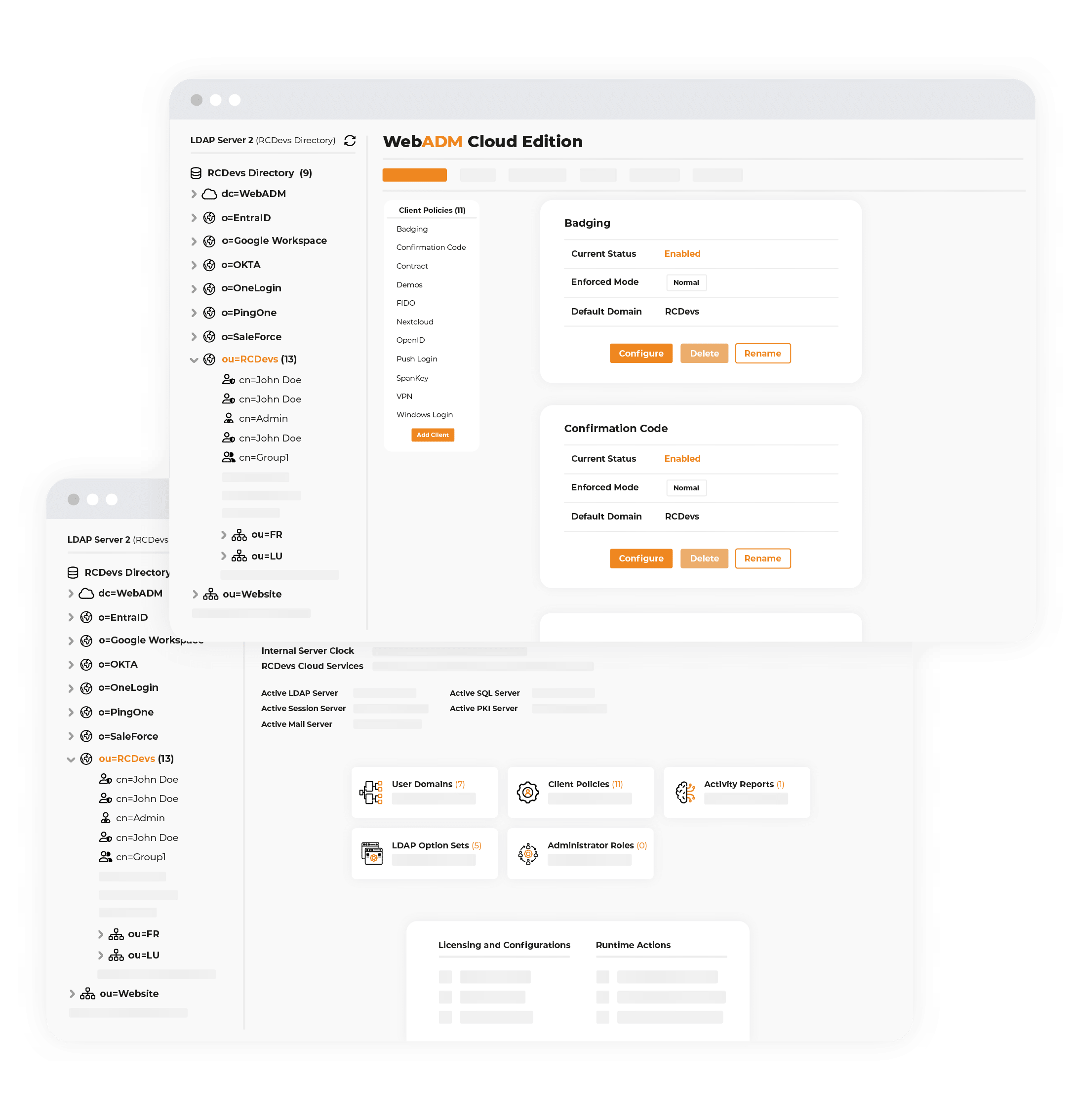
WebADM Control Center
WebADM is RCDevs’ core framework. It is a clustered application server that connects to on-premise and cloud identity sources, hosts OpenOTP, SpanKey, RCDevs IdP and self-services, provides web-based directory administration, and federates cloud IAMs/IdPs.
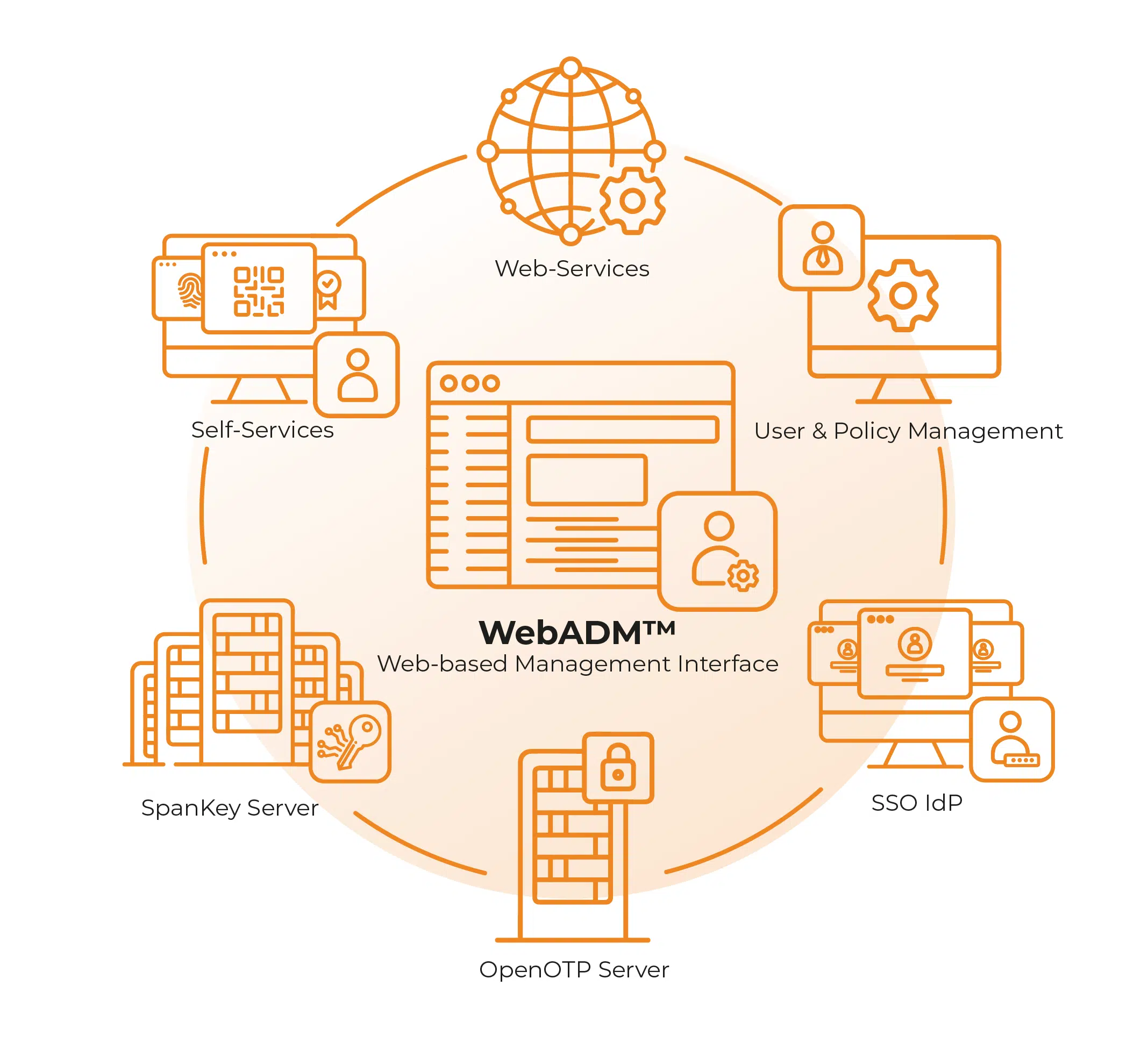
WebADM
WebADM is the beating heart of RCDevs’ solutions. Nothing runs without it, yet it stands strong on its own with a full PKI, powering services such as OpenOTP and SpanKey, and unifying all identity systems across on-premise and cloud environments.
IDENTITY & ACCESS MANAGEMENT
Core Functions of WebADM
Identity Management
WebADM connects to multiple identity sources, whether on-premise or in the cloud, to provide unified control over users and groups across the organization.
It supports integrations with:
✔️ On-premise directories such as Active Directory, OpenLDAP, Novell eDirectory, etc…
✔️ Cloud identity services including Azure Active Directory (Entra ID), Google Workspace Directory, Okta, Duo, Ping Identity, OneLogin, etc…
By consolidating these sources into a single management interface, WebADM simplifies identity administration and ensures consistency across all systems.
Access Management
Policies define who can access what, when, from which networks, and under what conditions. They govern how users authenticate and which resources they can reach. Whatever your access strategy, role-based, contextual, or aligned with a Zero Trust model, WebADM can implement and enforce it to keep security consistent while adapting authentication workflows per application and context.
Policy layers (by weight, higher overrides lower)
✔️ w1 - Default application configuration
✔️ w3 - Per-user
✔️ w2 - Per-group
✔️ w4-w6 - Per-application
Precedence rule
✔️ Settings with the highest effective weight take priority
Evaluation criteria (examples)
✔️ User attributes, group membership, directory source, authentication
method, client type, network/location, time
OpenOTP example (LoginMode)
✔️ Default (w1): LDAP
✔️ Per-user (w3): LDAP+OTP → requires password and one-time password
✔️ Per-application (e.g., w5): LDAP+U2F → for that specific app, requires password and FIDO/U2F, overriding lower-weight settings
Service & Application Server
WebADM hosts OpenOTP, SpanKey, the OpenID Connect/SAML IdP, and self-service tools, with a helpdesk for delegated first-line support. It provides the runtime, directory connectivity, policy enforcement, and integrations needed for unified authentication and federation.
✔️ Connects to directories: Active Directory, OpenLDAP, and cloud identity sources
✔️ Enforces access policies: method selection and conditions (network, time, client), with per-application overrides
✔️ Integration options: RADIUS, LDAP, SAML, OpenID Connect, REST APIs
✔️ Hosts core services: OpenOTP, SpanKey, OpenID Connect / SAML IdP
✔️ Provides self-service portals: password reset, OTP/FIDO enrollment, device management
✔️ Includes Helpdesk for delegated Level-1 support (unlock, reset, enroll), with scoped permissions and audit trail
✔️ Operational features: logging/auditing, monitoring hooks, clustering/high availability (when deployed accordingly)
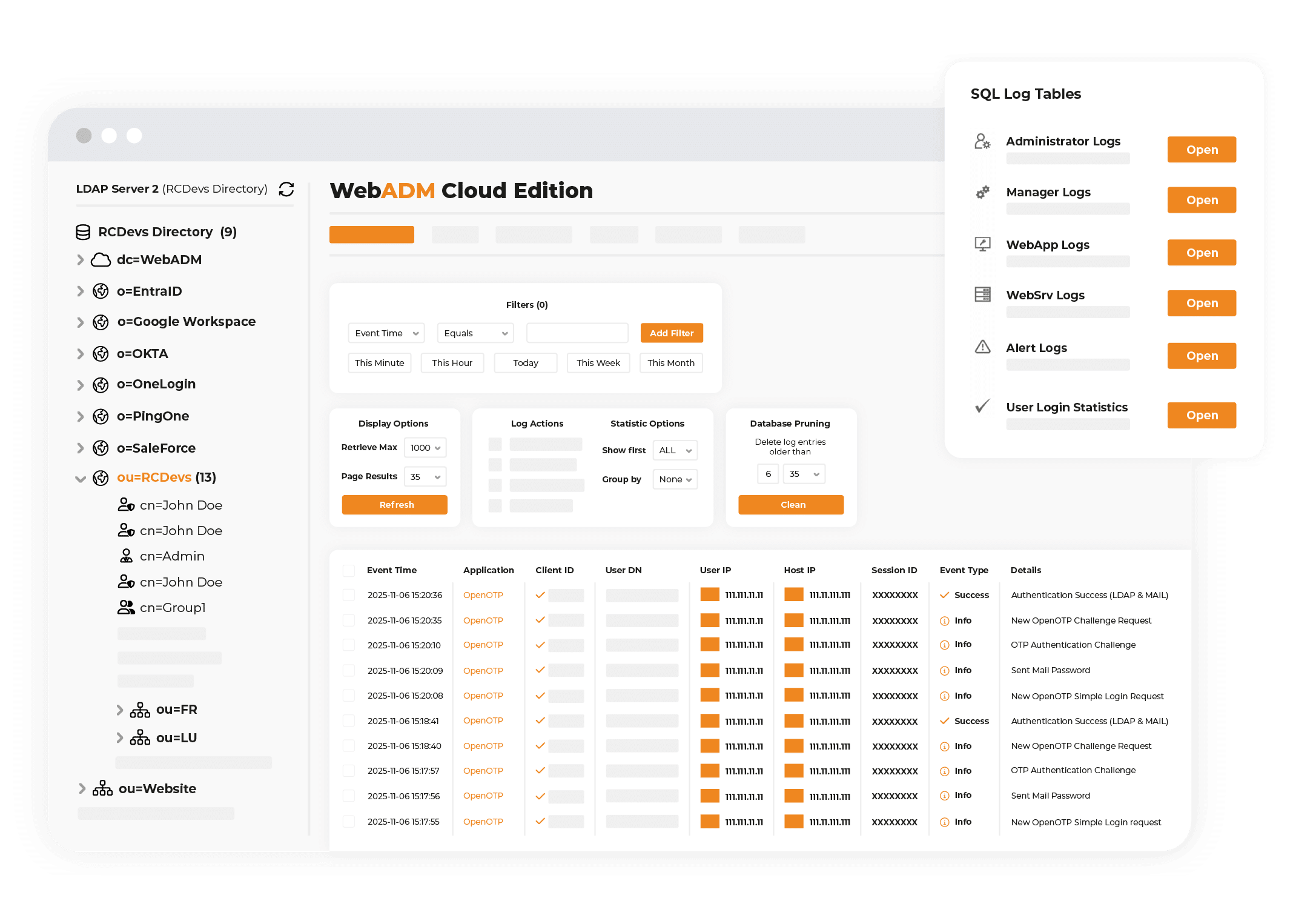
Audit & Logs
WebADM audit logs capture authentication events and administrative actions, and can be exported to external Security Information and Event Management (SIEM) platforms such as Splunk for centralized analysis and compliance reporting.
✔️ Events covered: authentications, configuration changes, admin and helpdesk actions
✔️ Context: timestamp, actor, source IP/agent, target application, outcome
✔️ Export: syslog/CEF output compatible with SIEMs (e.g., Splunk, QRadar, Elastic)
✔️ Retention & review: configurable retention, search and filtering, export for audits
✔️ Access control: role-based visibility and optional redaction of sensitive fields
Learn More About WebADM
Refer to our online documentation for additional WebADM resources
Unified IAM Federation
Native IAM Integration
OpenOTP is compatible with local directories such as Active Directory (AD) and LDAP, providing extensive support for on-premise environments. Additionally, it is natively integrated with Entra ID, Okta, DUO, Google, Ping Identity, One Identity, and many other identity providers, enabling simple integration across diverse IAM systems.