FIDO2

Now you can log in to your Windows computer with FIDO2 ready USB key or device, as you used with the FIDO U2F Key.
Exciting New functionality
FIDO2 for Windows Credential Provider
There are 3 scenarios, you can log in to your RCDevs Windows credential provider via the FIDO2 key:
1)If you are on your active directory network, you can log in on your active directory with or without enabling Multi-Factor Authentication with your FIDO2 Key.
2)If you are outside your network and connected to the internet, you can still have authentication with your FIDO2 key that is verified on your RCDevs OpenOTP Server.
3)With no connection at all the offline mode still allows you to use your FIDO2 Key to authenticate yourself on your computer.
This mode is, of course, not mandatory and you can set the duration you want to enable it.
– LDAPU2F: Require both LDAP and FIDO responses.
– LDAPMFA: Require LDAP and either OTP or FIDO.
Main Benefits
Higher Security
Authentication to multiple systems with one device
Low Discrepancy
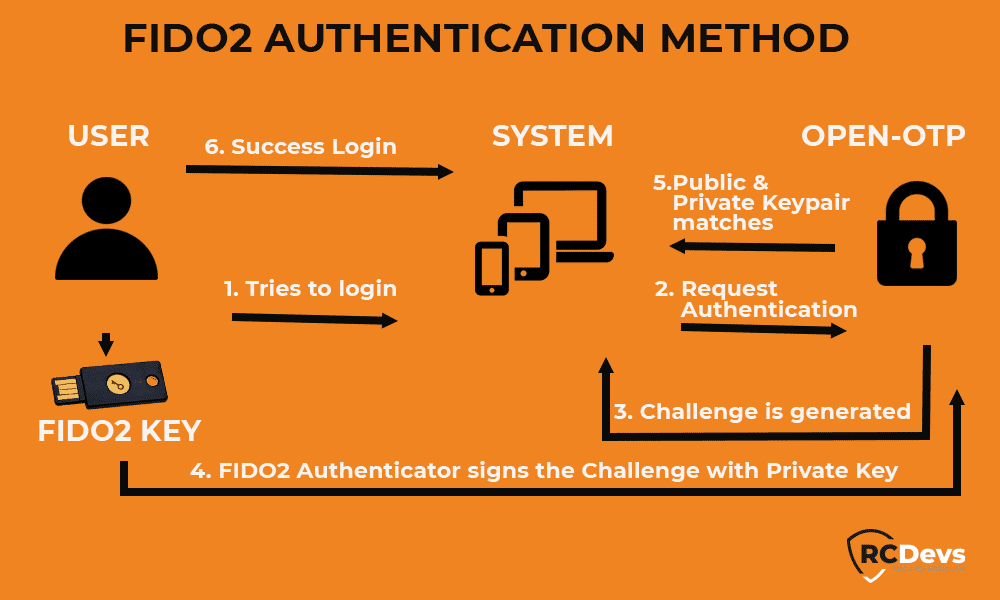
How FIDO2 works for the Windows Credential Provider client?
Here WebADM is the relying party. When you log in and configure in FIDO2, WebADM sends a challenge to the private key. The user’s private key is stored in FIDO2 authenticator, which is protected by a biometric factor or a pin (user’s presence is mandatory) and is used to sign transactions initiated by a relying party.
It brings to your windows login the same tree logging scenario that you already had with your RCDevs Mobile Push App.

