metaIAM
UNIFIED IAM FEDERATION
One Master IAM to Rule Them All
Federate multiple individual IAM systems (Microsoft Entra ID, Okta, Cisco DUO, PingIdentity, OneLogin, Salesforce, etc…) by inter-connecting
them and abstracting your ‘meta-IAM’ in a single, top-level and structured aggregated directory, with optional 2 way sync.
On top of this meta-IAM, the RCDevs solution provides IdPs and supports any Cloud or on-premises integration like email systems, VPNs, OIDC, etc.
The Future of IAM is Federation
Modern identity management is about connecting systems, not collapsing them
A Meta-IAM for a Decentralized World
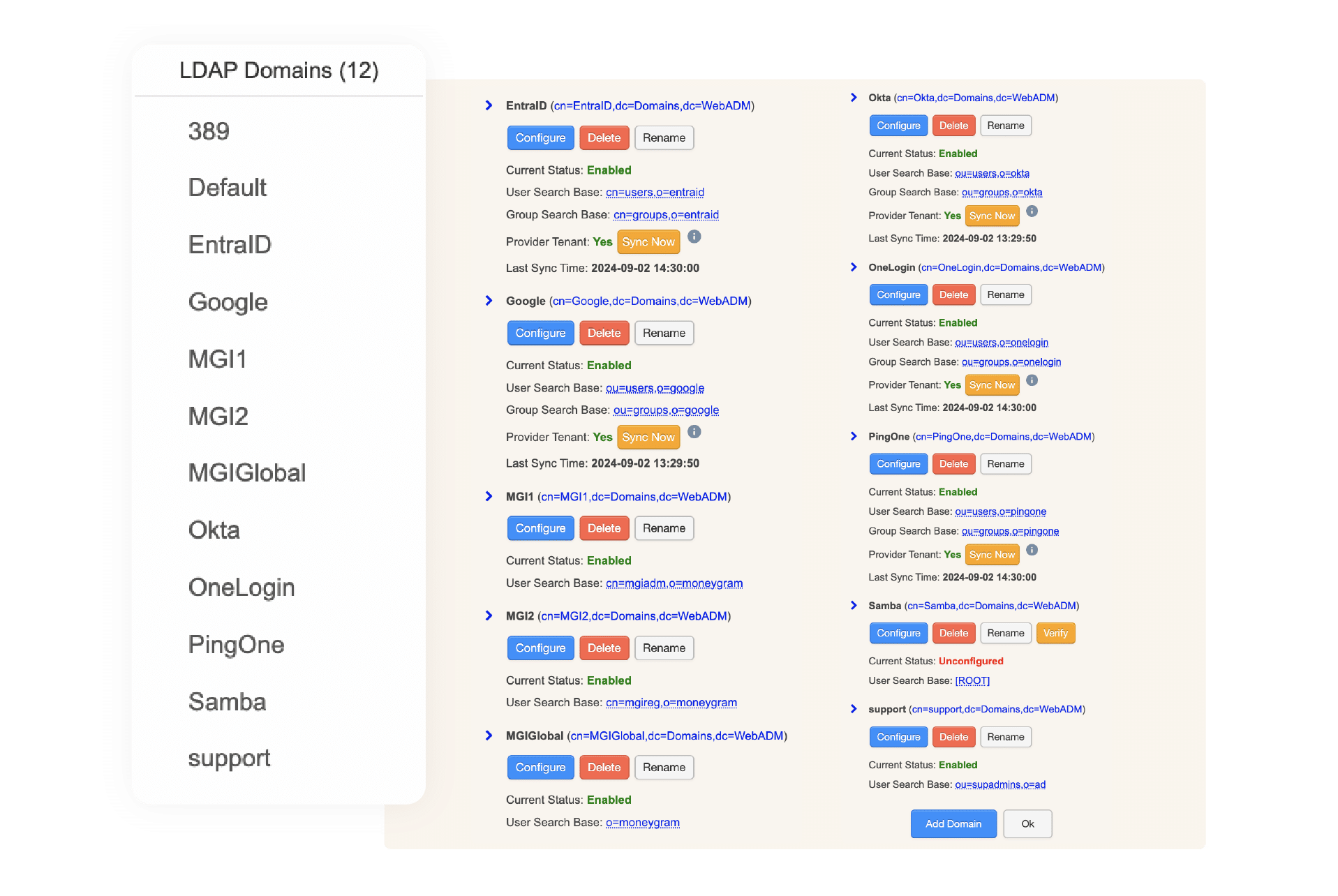
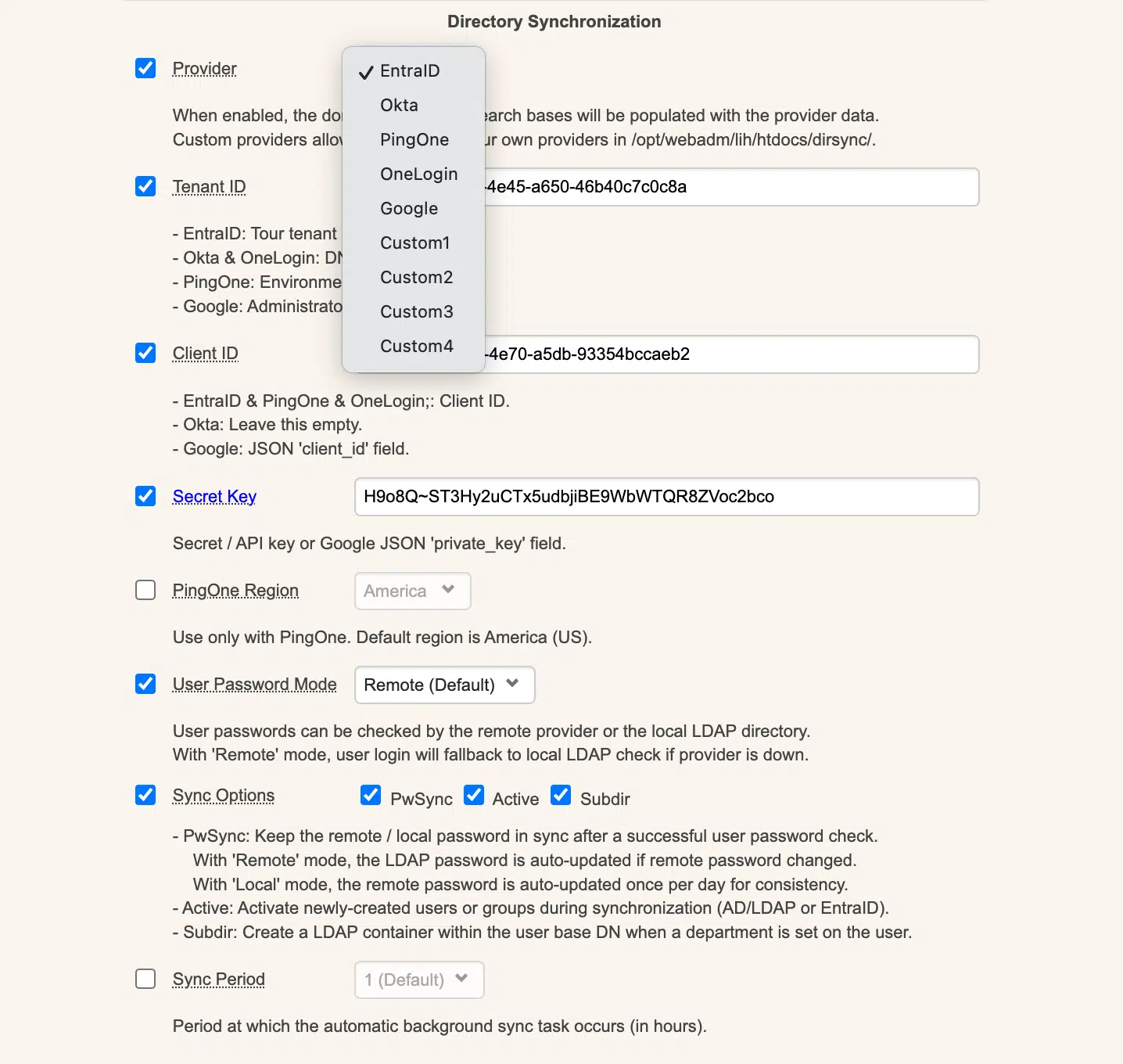
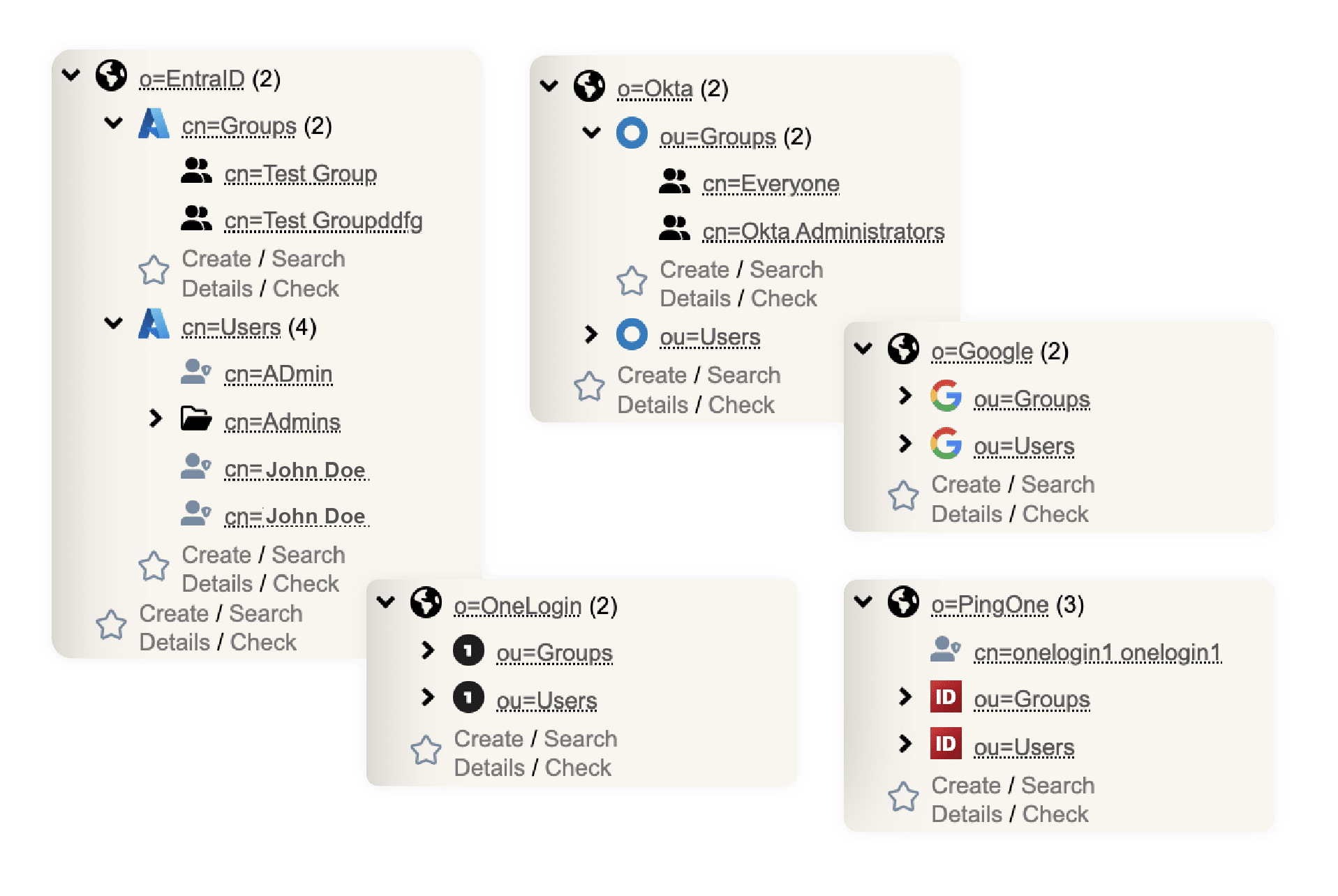
At the heart of this new-gen architecture is the WebADM meta-directory, a centralized abstraction layer that brings together identity information from multiple IAM services:
Once connected via lightweight connectors, WebADM builds a meta-IAM: a logical entity composed of multiple IAMs. From there, administrators can define meta-groups, user groups that span IAM boundaries, and design fine-grained access policies for apps, VPNs, PKI, Windows logins, PAM systems, and more.
No sync storms. No migration headaches. No duplicated identities.
Just one logical view over many systems, updated in real time, with full support for cross-IAM authorization.
Federation Without the Cascading IdPs
Traditional IAM federation relies on chaining or cascading identity providers (IdPs) using SAML, OIDC, or LDAP referrals. That model quickly becomes a spaghetti mess when you have multiple IdPs across subsidiaries, partners, and business units.
WebADM flips that on its head!
There is no need to cascade or nest identity providers. Instead, each IAM remains autonomous and untouched. RCDevs’ connectors pull necessary identity and group info into the meta-IAM layer, where global policies and access control rules are enforced.
That means each system, whether a cloud IAM, legacy AD, or SQL user store, continues to function independently. But to the applications and services consuming identity from WebADM, it is all one clean, logical model.
Build Meta-Domains & Cross-IAM Access Groups
With WebADM, you can create meta-domains — logical entities that group multiple IAMs under a single umbrella. Then you can define meta-groups that span those domains.
Example use case:
1. Combine users from Entra ID (corporate cloud), on-prem AD (legacy users), and a partner’s Okta instance.
2. Place selected users from each in a meta-group: SecureFinanceOps.
3. Apply a single access policy to that meta-group to control access to a VPN, internal dashboards, and PKI-based email signing.
This kind of cross-IAM group policy is normally the holy grail of IAM strategy — and RCDevs delivers it without data migration, synchronization pain, or IdP sprawl.
Zero-Footprint, Bi-Directional Sync
By default, WebADM operates in a zero-footprint mode, meaning it does not modify the connected IAMs. But if you want more control, it also supports one-way or two-way sync, enabling centralized user and group provisioning.
In two-way mode, WebADM becomes a master IAM manager across all systems.
You can:
• Move or copy users between IAMs
• Retain passwords, MFA/FIDO credentials, and group memberships
• Automatically propagate identity changes
Example: You can move a user from Okta to AD with a click and WebADM handles the rest, preserving credentials, MFA enrollment, and even password hashes thanks to its IAM metadata layer.
Temporary Access & Smart Federation
One of the most powerful features of RCDevs WebADM is its temporary federation capability.
Example:
You have a consultant from Company A who needs access to internal services at Company B for a short project.
With WebADM, you can:
• Temporarily copy the user to Company B’s IAM (or a federated group)
• Include password + MFA details
• Set an auto-expiry date
• Apply scoped access policies
The user has simple access for the duration of the project, and everything is cleaned up automatically after.
RCDevs IAM Consolidation
Key Features
Scalable Identity Convergence
Streamline and scale identity management by unifying siloed IAM and IdP systems into a single, centralized view built for millions of identities.
Bi-Directional Sync
WebADM supports real-time or scheduled two-way sync, allowing changes like group memberships, user metadata, and token assignments to be written back to connected identity systems. Users and groups can be copied or moved across IAMs with passwords and MFA methods intact.
Cloud Outage Resilience
Ensure system resilience with automatic local password synchronization, allowing for continued operation even during a cloud/SaaS service outage.
Unified Authentication Across Systems
Enable a single application to authenticate users easily across any connected IAM, providing a unified and smooth authentication process.
Native Integration
Integrate directly with IAM systems, eliminating the need for additional LDAP connectors. This simplifies the setup process and reduces complexity.
Cross-IAM Policy Design
Create and enforce security policies that span across multiple IAM systems, maintaining consistency and security throughout the organization.
Remote User Management
Manage remote IAM users effectively without the need for password resets, ensuring a seamless user experience.
Group Membership Synchronization
Sync group memberships across different IAM systems and implement Unix-level group functionalities for enhanced access control and management.
Multi-Tenant Implementation
Implement all these features on a per-tenant basis in our MSSP multi-tenant edition, offering customized IAM solutions for each tenant.
SEEING
IS BELIEVING
Whether you are buying a car or a security solution, you always want to test drive it before signing on the dotted line. We know this and you know this.
Contact us for your Free PoC or check it out for yourself.