Kerberos Authentication
🔑 Key Takeaways
- Kerberos is a mature, ticket-based authentication protocol enabling secure SSO across enterprise networks and is the default in Active Directory.
- Core components include the Client (Principal), the Key Distribution Center (Authentication Server & Ticket Granting Server), and the Service Server.
- Security model uses strong encryption, mutual authentication, and tightly time-synchronized tickets—no passwords transmitted over the network.
- Ticket workflow: obtain a Ticket-Granting Ticket (TGT), request a Service Ticket from TGS, then present it to the target service for access.
- RCDevs OpenOTP integration adds multi-factor authentication (TOTP, push, FIDO2, hardware tokens) at the Ticket Granting Service stage via RADIUS or LDAP, enabling MFA in Active Directory Kerberos environments without modifying existing infrastructure.
Kerberos Authentication Protocol: A Complete Guide for Enterprise Security
Kerberos, a battle-tested network authentication protocol, has been securing enterprise networks for over three decades and remains a cornerstone of modern authentication systems. Whether you’re managing an Active Directory environment, implementing Single Sign-On (SSO), or architecting a hybrid cloud infrastructure, understanding Kerberos is essential for IT professionals and security architects.
This comprehensive guide explores how Kerberos works, its role in enterprise security, and how modern organizations are adapting this proven protocol to meet contemporary security challenges.
What is Kerberos?
Kerberos stands as one of the most trusted network authentication protocols in enterprise environments. Named after the three-headed guard dog of Greek mythology, this protocol employs a sophisticated ticket-based system to verify the identity of users and services across unsecured networks.
Core Components
The Kerberos architecture consists of three essential components:
- Client (Principal): The user or service requesting authentication
- Key Distribution Center (KDC): The trusted server that issues tickets, comprising:
– Authentication Server (AS): Handles initial authentication
– Ticket Granting Server (TGS): Issues service tickets - Service Server: The resource the client wishes to access
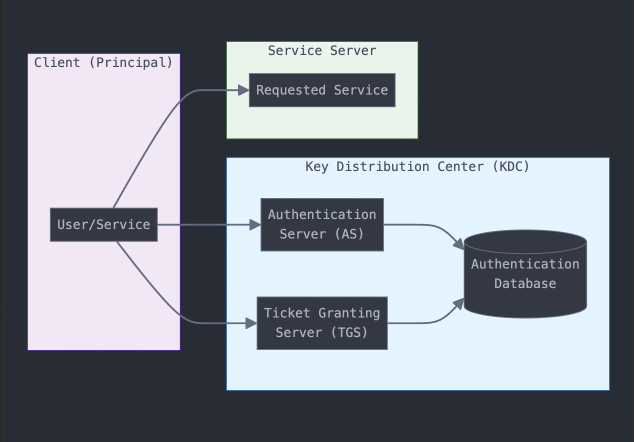
How Kerberos Works
The Kerberos architecture consists of three essential components:
1. Initial Authentication
The client requests a ticket-granting ticket (TGT) from the Authentication Server
The AS verifies the client’s credentials against the authentication database
Upon successful verification, the AS issues an encrypted TGT
2. Service Access
Using the TGT, the client requests a service ticket from the TGS
The TGS validates the TGT and issues a service ticket
The client presents this ticket to the desired service
3. Session Establishment
The service validates the ticket
Upon successful validation, the service grants access to the client
Key Security Features
Strong Encryption
Kerberos employs robust encryption methods to protect all communications, including:
- Ticket encryption using service keys
- Session key generation for secure client-service communication
- Password-derived key encryption for initial authentication
Time Synchronization
The protocol relies heavily on timestamp verification to prevent replay attacks:
- Tickets include creation and expiration timestamps
- All participating systems must maintain synchronized clocks
- Typical ticket lifetime ranges from hours to days
Enterprise Implementation
Active Directory Integration
Microsoft’s adoption of Kerberos as the primary authentication protocol for Active Directory has made it ubiquitous in enterprise environments:
- Seamless integration with Windows domain services
- Support for cross-forest authentication/li>
- Enhanced security compared to NTLM authentication<
Modern Authentication Challenges
While Kerberos excels in traditional network environments, modern enterprises face new challenges:
- Cloud service integration
- Remote work authentication
- Multi-factor authentication requirements
Enhancing Kerberos with Modern MFA Solutions
Modern security requirements often necessitate additional authentication factors beyond what Kerberos provides natively. RCDevs OpenOTP seamlessly integrates with Kerberos environments to provide:
- Transparent multi-factor authentication
- Enhanced security without disrupting existing workflows
- Simple deployment in Active Directory environments
For detailed information about implementing Kerberos with modern MFA capabilities, visit our dedicated blog post about OpenOTP’s Kerberos support.
Common Kerberos Terms
- Principal: A unique identity in the Kerberos realm
- Realm: A logical network served by a single KDC
- Ticket: An encrypted data structure proving authentication
- Service Principal Name (SPN): Unique identifier for a service instance
Best Practices for Kerberos Implementation
- Maintain precise time synchronization across all systems
- Regular key rotation and password policy enforcement
- Proper planning of realm trust relationships
- Implementation of monitoring and logging
Future of Kerberos
While newer authentication protocols emerge, Kerberos continues to evolve:
- Integration with cloud authentication services
- Enhanced encryption methods
- Support for zero-trust architectures
Further Resources
FAQ
What is Kerberos and how does it work?
What is the purpose of a Kerberos ticket?
. Ticket-Granting Ticket (TGT): Acts like a digital passport that proves initial authentication
. Service Ticket: Grants access to specific services without requiring password re-entry These tickets are time-limited and encrypted, making them secure alternatives to repeatedly transmitting passwords.
Is Kerberos still relevant in modern environments?
. The primary authentication protocol for Active Directory environments
. A crucial component in hybrid cloud architectures
. Compatible with modern multi-factor authentication solutions
. Regularly updated with modern encryption standards
How secure is Kerberos?
. Never transmits passwords over the network
. Uses strong encryption for all tickets and communications
. Provides time-stamped authentication to prevent replay attacks
. Supports mutual authentication between clients and services
However, like any security protocol, its effectiveness depends on proper configuration and maintenance.
What are the differences between Kerberos and NTLM?
. Faster authentication process
. Mutual authentication support
. Better security through ticket-based system
. Support for delegation of authentication
NTLM is considered legacy technology and should only be used as a fallback when Kerberos is unavailable.
How does Kerberos compare to RADIUS?
. Kerberos: Designed for network service authentication within an enterprise domain
. RADIUS: Primarily used for network access authentication (VPNs, Wi-Fi, remote access)
Many organizations use both protocols: Kerberos for internal services and RADIUS for network access control.
What are the key differences between Kerberos and SAML?
. Kerberos: Traditional on-premises authentication protocol
. SAML: Modern protocol designed for web-based SSO and cloud services
Key distinctions:
- Kerberos operates at the network protocol level; SAML works at the web browser level
- Kerberos excels in Windows domain environments; SAML is preferred for cloud applications
- Kerberos uses tickets; SAML uses XML-based assertions
How can Kerberos be integrated with modern authentication systems?
- Implementing multi-factor authentication (MFA)
- Integrating with cloud identity providers
- Using solutions like RCDevs OpenOTP for additional security layers
- Maintaining hybrid environments that support both Kerberos and modern protocols
How does RCDevs OpenOTP enhance Kerberos authentication?
Seamless Integration:
- Transparent multi-factor authentication that doesn't disrupt the native Kerberos workflow
- Simple deployment through a single WebADM configuration file
- No modification required to existing Kerberos infrastructure
Enhanced Security Features:
- Addition of strong MFA to traditional Kerberos authentication
- Support for various authentication methods (biometrics, mobile push, hardware tokens)
- Real-time security policy enforcement
Enterprise Benefits:
- Maintains the familiar single sign-on experience for users
- Bridges legacy systems with modern security requirements
- Enables gradual transition to newer authentication protocols
- Supports hybrid IT environments combining on-premises and cloud services

