u2f
RCDevs & Yubico
OTP/U2F for Entreprises
2 leaders in the multi-factor market joined their forces
The solution relies on RCDevs’ OpenOTP technology combined with Yubico’s OTP/U2F user authenticators and HSM devices. It also aggregates the best of two worlds: RCDevs specialized in the OTP/U2F Enterprise integration with its flexible and full-featured security back-end supporting a wide variety of user authenticators. Yubico focussed on user experience, usability and stronger security concepts with its YubiKey product family and cost-effective HSM devices.
Customers worldwide recognize RCDevs and Yubico as pioneers in the security market, providing advanced technologies and high-quality products. The RCDevs/Yubico solution is well designed, suited for modern customer needs, extremely robust and scalable from SMEs to large corporations. It is already used by thousands of customers worldwide, including fortune 500 companies.
RCDevs & Yubico helps you to
Implement OTP/U2F for entreprises
Customers worldwide recognize RCDevs and Yubico as pioneers in the security market, providing advanced technologies and high-quality products. The RCDevs/Yubico solution is well designed, suited for modern customer needs, extremely robust and scalable from SMEs to large corporations. It is already used by thousands of customers worldwide, including fortune 500 companies.
A New Standard for Two-Factor Authentication
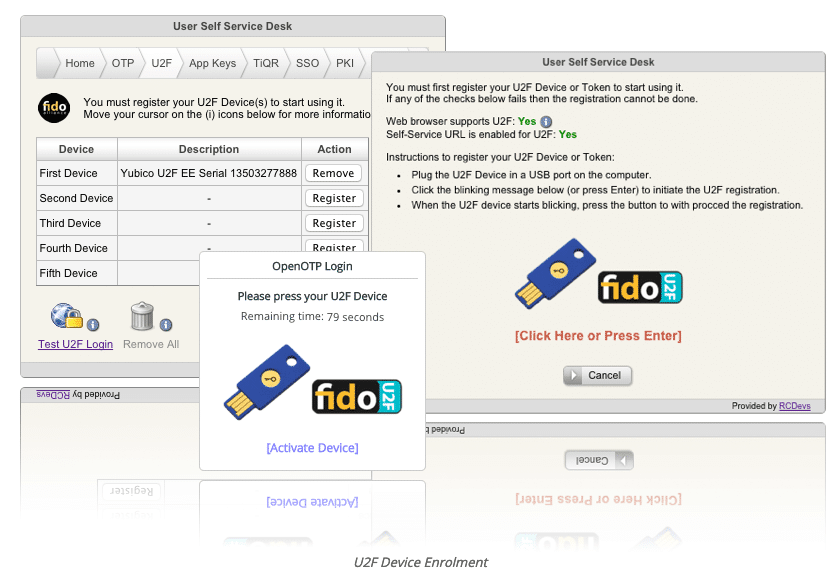
U2F Specifications
LDAP/AD domain passwords
YubiKeys from Yubico (Standard, Neo, Nano, Edge)
Security Key from Google and Yubico (U2F)
Hardware Tokens (event-based, time-based and challenge-based)
Mobile/Software Tokens (Google Authenticator and any OATH compliant client)
SMS Tokens (with Clickatel, Plivo, AQL, custom SMSCs and any SMMP provider)
Mail and Secure Mail Tokens (PIN mailer)
Pre-generated OTP Lists, Emergency OTP, etc…
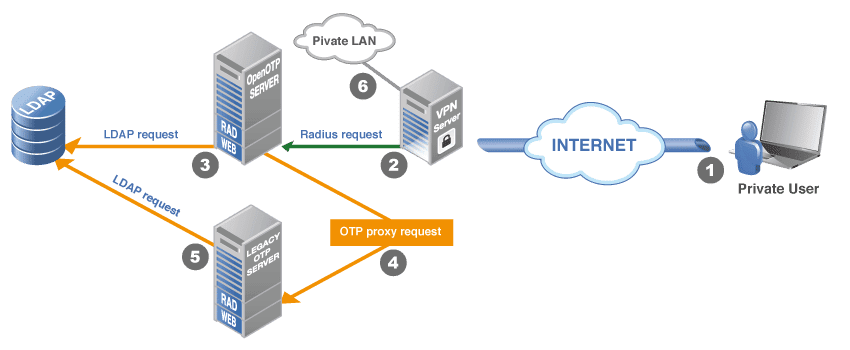
The OpenOTP architecture is modular and highly scalable, with proxy servers that can be exposed in the DMZ and a backend server which comes with failover and load balancing capabilities.
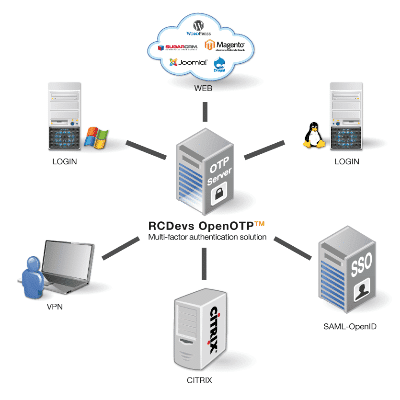
OpenOTP and most RCDevs integration plugins support two-factor authentication with both OTP and U2F through a set of comprehensive APIs, fine-grained Identity and access management (IAM), powerful audit capabilities, Web SSO with integrated OpenID / SAML services, advanced RADIUS support.
Integrations
OpenOTP and most RCDevs integration plugins support two-factor authentication with both OTP and U2F through a set of comprehensive APIs, fine-grained Identity and access management (IAM), powerful audit capabilities, Web SSO with integrated OpenID / SAML services, advanced RADIUS support.
ACME has set up the YubiKey NEO for its employees, and is using OpenOTP to provide authentication for their internal systems.
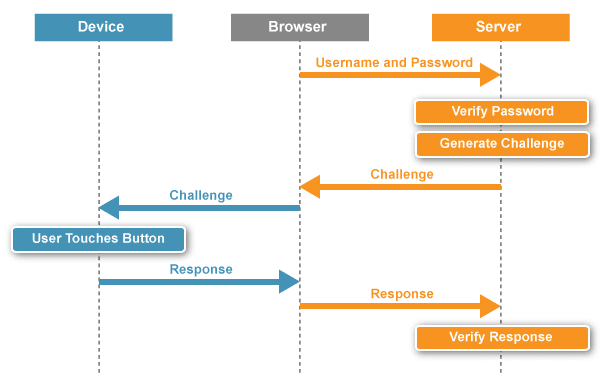
The ACME user inserts his YubiKey NEO, which has dual capabilities U2F/OTP, into a USB port on his PC. The PC is protected by Windows user login and password and a one-touch U2F challenge. The user enters his domain username and password, and touches his YubiKey NEO to confirm the U2F authentication. His credentials are validated, and he is logged in to his Windows environment.
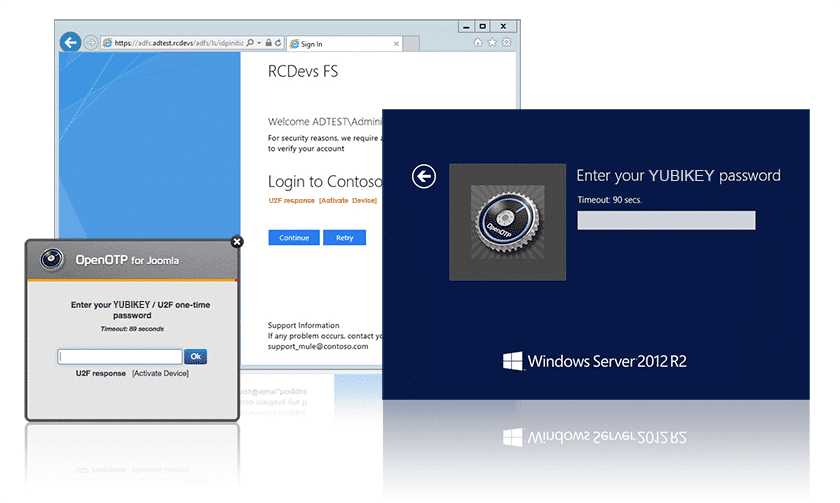
Control access to Microsoft Web resources
From the OpenOTP application, this ACME user can launch all of his SAML-enabled cloud applications, including Salesforce or Jive, after a single U2F authentication. For VPN access, this ACME user will use the same YubiKey, using a single touch to generate a One Time Password.
ACME Administrators will also use their own YubiKey NEO to authenticate to their privileged UNIX accounts over SSH utilizing the OTP mode.
For accessing cloud applications on their Android devices, both administrators and users leverage the NFC capability of the YubiKey NEO and, once again, they enjoy a one-touch experience As a fallback method, OpenOTP will offer a simple OTP via SMSField Communications.
Yubico OTP / U2F Hardware

With the advanced OpenOTP APIs, both YubiKey OTP and U2F authentication can be used concurrently. Users will experience signed authentication with FIDO-U2F anytime the target resource is compatible and continues working in YubiKey OTP mode for their VPNs. Newer YubiKeys (like YubiKey Edge and YubiKey NEO) support both OTP and U2F working modes and the devices automatically choose the right authentication mechanism.
Yubico HSMs
In OpenOTP, YubiHSMs are used for:
Secure storage of YubiKey and OATH Tokens’ secret seeds.
Secure storage of passwords, PIN code and other critical user / system information.
Random OTP generation for SMS, Mail OTP and printed OTP lists.
Random U2F challenges.
Product Compatibility Matrix
| Product | Integration | YubiKey OTP | YubiKey U2F | OATH Token | Mobile Tokens | SMS/Mail OTP |
|---|---|---|---|---|---|---|
| VPN (Juniper, Cisco, F5, Checkpoint, Palo-Alto…) | RADIUS | Yes | No | Yes | Yes | Yes |
| "Citrix Netscaler, Gateway" | RADIUS | Yes | No | Yes | Yes | Yes |
| MS Windows Login, RDP, Terminal Services | OpenOTP Credential Provider | Yes | Yes | Yes | Yes | Yes |
| MS Windows Offline Login | OpenOTP Credential Provider | No | Yes | No | No | No |
| MS Reverse-Proxies (UAG, TMG) | RADIUS | Yes | No | Yes | Yes | Yes |
| MS Web Applications (Exchange, Sharepoint) | OpenOTP ADFS | Yes | Yes | Yes | Yes | Yes |
| MS Office 365 | OpenOTP ADFS | Yes | Yes | Yes | Yes | Yes |
| Google Apps | OpenOTP SAML/OpenID | Yes | Yes | Yes | Yes | Yes |
| Cloud Product & Services (SalesForce, Zimbra, SugarCRM, Jive…) | OpenOTP SAML | Yes | Yes | Yes | Yes | Yes |
| Web Products (Joomla, WordPress, Magento, Roundcube, Drupal, OwnCloud…) | OpenOTP Plugin | Yes | Yes | Yes | Yes | Yes |
| Linux / UNIX Services | OpenOTP PAM | Yes | No | Yes | Yes | Yes |
| Mac OSX Login and Services | OpenOTP PAM | Yes | No | Yes | Yes | No |
| Home-made Web Applications | OpenOTP APIs | Yes | Yes | Yes | Yes | Yes |
| C, C++, Java, .NET | OpenOTP APIs & SDK | Yes | Yes | Yes | Yes | Yes |
Migrating from a third-party OTP solution
There are many possible scenarios to implement a migration to RCDevs & Yubico. A common option consists in installing and configuring OpenOTP on top of your Active Directory Domain, side by side with an existing OTP solution. In this case the migration simply consists in implementing a standalone OpenOTP installation and switching to the new system when it is ready for production. In many cases, this approach is the easiest option but in some circumstances, you need to make OpenOTP server(s) work commonly with the existing OTP server(s), at least for a certain time. This second option is required when:
There are many users involved and you need to gradually re-enrol the users with other OTP devices or software (ex. you change from RSA Tokens to YubiKeys).
You need the existing OTP server(s) to remain for a certain time because some integrations have been customised for specific server APIs. You also need to update these custom integrations for OpenOTP. For example, your home-made Web applications’ login process must be adapted to use the OpenOTP Web APIs.
You want to keep existing hardware Tokens for users until they expire and sporadically enrol new hardware Tokens (ex. YubiKeys) one-by-one.
Migration Process
One OTP server from a third-party vendor which provides a RADIUS RFC-2865 interface.
A VPN server as client application consuming the RADIUS OTP validation service.
A pool of users registered in a MS Active Directory LDAP.
Migration Requirements
LDAP
RADUIS
Migration Steps
Step 1
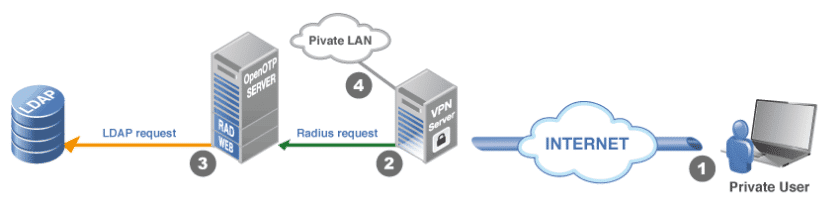
Step 2