Zero Trust Security Model
Implementing a Zero-Trust Security Model for Effective Data Protection
The zero-trust model is an information security framework that has become increasingly popular in recent years. It refers to the principle of not trusting anything inside or outside of the network perimeter by default. Instead, it requires verification of every user and device that tries to access the network. This approach helps to reduce the attack surface and improve overall security posture.
Origins of Zero Trust
The term zero trust was first coined in 2010 by Forrester Research, but the concept can be traced back to the BeyondCorp project developed by Google. The project aimed to address the challenges of traditional perimeter-based security models, where access to resources was restricted based on whether a user was within the corporate network or not. BeyondCorp sought to move away from this model and instead focus on identity-based access controls, allowing employees to access resources from any device, anywhere in the world, as long as they could prove their identity.
The concept gained further momentum with the 2020 NIST SP 800-207 publication, which provided the first comprehensive federal guidelines for Zero Trust Architecture. According to Gartner’s 2023 research, 61% of organizations are actively implementing Zero Trust strategies, with the market expected to reach $51.6 billion by 2026. The approach has evolved from Google’s initial identity-centric model to encompass broader frameworks including Secure Access Service Edge (SASE) and Zero Trust Network Access (ZTNA) architectures.
How to Implement Zero Trust Model?
Implementing a zero-trust model requires a systematic approach. Here are the key steps involved:
- Identify critical data and systems that need to be protected.
- Define the access policies for each user and device.
- Use multi-factor authentication (MFA) to verify user and device identity.
- Apply the principle of least privilege, which means granting users the minimum level of access necessary to perform their job functions.
- Monitor network activity in real-time to identify potential threats.
- Continuously review and refine access policies based on user and device behavior.
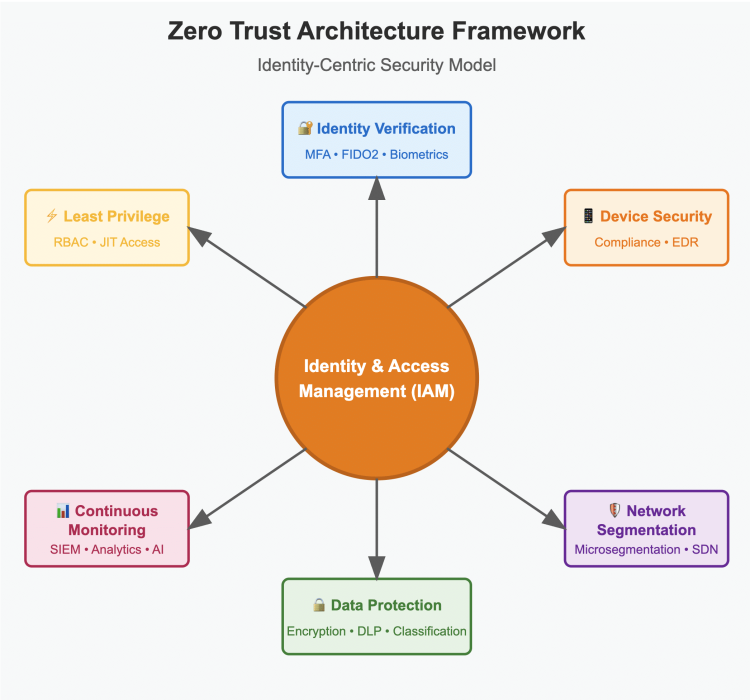
What are the Key Components of Zero Trust?
- Identity and Access Management (IAM): This involves verifying the identity of users and devices attempting to access resources, and providing access only to those with the appropriate level of authorization (detailed hereafter).
- Network Segmentation: This involves dividing the network into smaller segments, each with its own security controls and access policies. This reduces the risk of lateral movement by attackers in the event that one segment is breached.
- Endpoint Security: This involves securing all endpoints, including laptops, desktops, servers, and mobile devices, with appropriate security controls such as firewalls, antivirus software, and intrusion detection and prevention systems.
- Least Privilege: This means providing users with the minimum level of access required to perform their jobs, and restricting access to sensitive resources to only those who need it.
- Continuous Monitoring: Monitoring network activity in real-time to detect and respond to security threats as they arise.
Technical Architecture Considerations
Successful Zero Trust implementations require careful consideration of several technical factors:
- Identity Verification Stack: Multi-layered authentication combining FIDO2/WebAuthn hardware tokens, risk-based authentication engines, and behavioral biometrics for continuous user verification
- Policy Decision Points (PDP): Centralized engines that evaluate access requests against dynamic policies, considering user context, device posture, application sensitivity, and threat intelligence
- Software-Defined Perimeters (SDP): Microsegmentation implemented through software-defined networking (SDN) and network function virtualization (NFV) technologies
- Data Loss Prevention (DLP) Integration: Real-time data classification and protection mechanisms that adapt permissions based on content sensitivity and user privileges
Implementation Challenges and Best Practices
Based on enterprise implementations across Fortune 500 companies, key challenges include:
- Legacy Application Integration: 73% of organizations struggle with applications lacking modern authentication APIs. Solutions include application proxy layers and privileged access management (PAM) bridges
- Performance Impact: Real-time policy evaluation can introduce 50-200ms latency. Optimization through edge computing and policy caching reduces this to sub-10ms
- Compliance Mapping: Aligning Zero Trust controls with frameworks like SOC 2 Type II, ISO 27001, and NIST Cybersecurity Framework requires detailed control mapping and automated evidence collection
Industry benchmarks indicate successful implementations achieve 85% reduction in lateral movement incidents and 67% faster threat containment compared to perimeter-based architectures.
The central role of Identity and Access Management (IAM) in Zero Trust Model
Identity and access management (IAM) plays a crucial role in the zero-trust model. IAM is the process of managing user identities and their access to resources. IAM ensures that only authorized users and devices can access critical systems and data. In a zero-trust model, IAM is used to verify user and device identity before granting access. This can be achieved through MFA, biometric authentication, or other forms of identity verification.
Conclusion and Next Steps
Zero Trust represents a fundamental shift from location-based to identity-based security models, with proven results across industries. Organizations implementing comprehensive Zero Trust architectures report average ROI of 150% within 24 months and 60% reduction in security incidents.
For organizations beginning their Zero Trust journey, we recommend starting with identity and access management as the foundational layer. RCDevs OpenOTP and WebADM provide enterprise-grade IAM capabilities supporting FIDO2, risk-based authentication, and comprehensive audit logging required for Zero Trust compliance.
FAQ
What is zero trust and how does it differ from traditional security models?
How does zero trust security fit in with other security models and frameworks?
Are RCDevs products compatible with "Zero Trust" approach?
- Identity and Access Management: OpenOTP and WebADM provide strong authentication and identity verification through a range of methods, including one-time passwords, push notifications, and biometric factors. This ensures that only authorized users can access resources, which is consistent with the zero trust approach.
- Least Privilege: OpenOTP and WebADM support role-based access controls, which allows administrators to assign access privileges based on the minimum level of access required to perform specific job functions. This reduces the risk of unauthorized access to sensitive resources.
- Continuous Monitoring: OpenOTP and WebADM provide real-time monitoring and logging of user activity, including failed authentication attempts, successful logins, and other security events. This enables administrators to detect and respond to security threats as they arise.
- Network Segmentation: OpenOTP and WebADM can be integrated with other security solutions to implement network segmentation, which helps to limit the lateral movement of attackers in the event of a breach.
- Compliance: OpenOTP and WebADM are compliant with a range of regulatory requirements, including GDPR, HIPAA, and PCI DSS. This ensures that only authorized users can access sensitive data, which is consistent with the zero trust approach.
What are the main challenges when implementing Zero Trust?
- Legacy system integration complexity - Older applications may lack modern authentication capabilities and require significant updates or replacement
- User experience considerations - Balancing security with productivity through seamless authentication flows without creating friction
- Organizational change management - Requiring cultural shifts from trust-based to verification-based thinking across all departments
- Cost and resource requirements - Comprehensive identity infrastructure, network segmentation, and continuous monitoring tools require significant investment
- Skill gaps in security teams - Need for expertise in identity management, micro-segmentation, and behavioral analytics
How do you measure Zero Trust maturity and success?
- Identity verification coverage - Percentage of users and devices with MFA and behavioral analytics implementation
- Network segmentation depth - Granularity of micro-perimeters and lateral movement prevention capabilities
- Data protection scope - Classification and encryption coverage of sensitive information across all systems
- Monitoring comprehensiveness - Real-time visibility and automated threat response capabilities
- Policy automation level - Reduction in manual access decisions and automated policy enforcement
Which industries benefit most from Zero Trust implementation?
- Financial Services - Enhanced protection of sensitive financial data and compliance with regulations like PCI DSS and SOX
- Healthcare - Protection of patient records (HIPAA compliance) while enabling secure remote access for medical professionals
- Government agencies - Securing classified information and critical infrastructure with defense-grade access controls
- Technology companies - Protection of intellectual property and customer data while supporting distributed development teams
- Manufacturing - Securing operational technology (OT) networks and industrial control systems from cyber threats
- Education - Protection of student data and research while providing flexible access for students and faculty across multiple locations
How does Zero Trust support remote work and cloud migration?
- Remote work enablement - Secure access from any location and device through identity-based verification rather than VPN connections
- Cloud migration benefits - Consistent security policies across on-premises and cloud resources, with access decisions based on user identity, device trust, and application sensitivity
- Hybrid and multi-cloud support - Unified access controls and continuous compliance monitoring regardless of where resources are hosted
- Location independence - Security policies follow users and data rather than being tied to specific network locations
What is the ROI and cost structure of Zero Trust implementation?
Cost reductions:
- Decreased breach costs - Average data breach cost is $4.45M according to IBM
- Reduced VPN infrastructure costs - Elimination of complex VPN management and hardware
- Streamlined access management - Automated policy enforcement reduces administrative overhead
- Faster secure onboarding - Automated identity provisioning and access controls
- Reduced help desk tickets - Fewer access-related issues and password resets
- Improved compliance audit efficiency - Automated reporting and continuous compliance monitoring
- Identity management platforms - Core authentication and authorization infrastructure
- Network segmentation tools - Micro-segmentation and policy enforcement points
- Endpoint security solutions - Device compliance and threat detection capabilities
- Staff training and expertise - Security team education and change management

