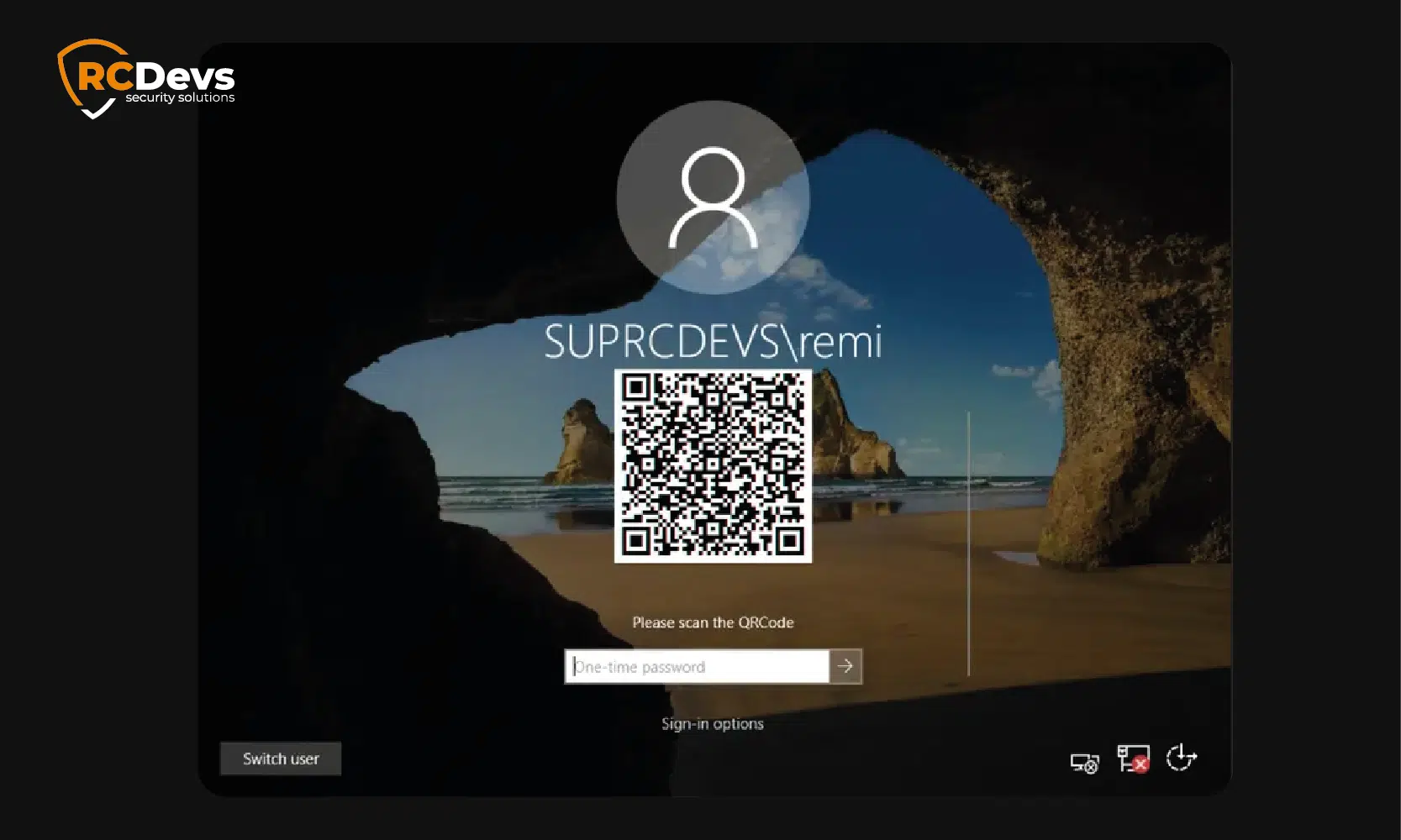
OpenOTP Windows Login & RDS – Supports Windows 7-11, Server 2012+, push/OTP/FIDO2.
Add MFA to Windows Login & RDS
with Inline User Enrollment
Add Multi-Factor Authentication with Inline Enrollment for Microsoft Servers, Remote Desktop & App logins. Enjoy enhanced security, even for offline logins (using our OpenOTP Token app or FIDO2).
As businesses increasingly rely on Microsoft Remote Desktop Services (RDS) and Windows Server to enable remote access to enterprise systems and shared applications, securing these environments is paramount.
OpenOTP MFA strengthens your RDS and Windows logins by adding a robust layer of protection—supporting push notifications, OTP, and FIDO2 authentication—against unauthorized access and compromised credentials. Compatible with Windows 7-11, Server 2012+, and even offline setups, it seamlessly integrates into domain or standalone systems via RADIUS or LDAP.
This enhanced security not only safeguards sensitive data and ensures compliance with industry standards but also delivers peace of mind for users accessing critical resources remotely. With OpenOTP, you can deploy enterprise-grade MFA in minutes, fortifying your organization’s defenses in today’s interconnected digital landscape.
Protect your Microsoft Operating System Access
RCDevs provides a Windows Credential Provider (CP) for Windows integrations. Our OpenOTP CP is your additional layer of protection for Windows login, remote access with Remote Desktop login & RDS.
Our OpenOTP CP supports both OTP and FIDO2 authentication mechanisms.
Any OpenOTP authentication method like Push Login, Yubikey, Hardware & software token, FIDO2 (except in RDS) is supported.
Our Credential Provider works in full AD environments but also in infrastructures without AD. Accounts can be separated from your AD (like in an OpenLDAP) and still be managed centrally.
Use cases include:
- Remote Desktop (RDS):
Secure on-premise RDP sessions with MFA. - Windows Server:
Add authentication to domain logins and portals. - Endpoints:
Safeguard desktops and VMware environments.
Version 4.0.0 of the OpenOTP Credential Provider introduces support for inline token enrollment directly from the Windows login screen. This feature enables new users to register their MFA tokens, whether software tokens like OpenOTP with Push notifications or hardware tokens, during the login process itself, without needing to switch devices or complete separate enrollment steps.
Our Windows Credential Provider:
Simplifies user onboarding by allowing token registration immediately at first login
Reduces the workload for IT and Helpdesk teams by minimizing manual provisioning and follow-up support
The Credential Provider supports multiple login scenarios:
- Online on company network:
Standard login with full connectivity to authentication servers. - Online off company network:
Login with internet access but outside the corporate network, enabling remote authentication. - Offline login:
Ability to authenticate without internet access by leveraging cached credentials and tokens, ensuring users can still securely log in even when disconnected (only possible with OpenOTP Token and FIDO2 authentication).
For Desktops & Laptops
For Remote Desktop Services
For AD Users
For Local Users and Computers Out of Domain
Key Features
Supports NT Domain-style login names like ‘Domain\Username’
Supports offline authentication with OpenOTP Token App & FIDO2 devices
Supports any OpenOTP method (Tokens, YubiKey, FIDO2, SMSOTP, eMailOTP)
Enterprise deployment with AD automated software deployment tools
Supports LDAP, challenged OTP & FIDO2 and Push login
Supports User Principal Names (UPN), implicit & explicit
Desktops & servers with Windows CP
All Windows Clients since Windows 7
All Windows Servers since 2008
Microsoft Remote Desktop Services
See how simple it is to integrate OpenOTP for Windows Logins
Frequently Asked Questions – Windows & RDS Login
Can I use Google Authenticator for Windows Logins?
Check how RCDevs' OpenOTP Token app works as a Windows login credential provider.
Can I perform a Windows Login with a Smart Card?
First, you need to configure the smart card through your MFA setup. Check the configuration documentation for smart card logins with RCDevs Security Solutions. After configuring, insert your smart card in the card reader. If the card is detected and the stored certificate can be used for logon, a new credential tile for the smart card will be prompted. You can select it and enter your PIN code. You will be logged in.
Documentation of windows login authentication with smart card.
Is a Windows Login using FIDO possible?
Unified IAM Federation
Native IAM Integration
OpenOTP is compatible with local directories such as Active Directory (AD) and LDAP, providing extensive support for on-premise environments. Additionally, it is natively integrated with EntraID, Okta, Google, Ping Identity, One Identity, and many other identity providers, enabling simple integration across diverse IAM systems.
Choose the right method
Authentication Methods
RCDevs’ IAM-MFA solutions are compatible
with Strong Authentication Technologies
A robust solution should support modern methods such as Push Notifications, FIDO2/Passkeys, YubiKeys and traditional SMS, email, and OTP. Support varies by integration (RADIUS, SAML/OIDC, desktop), client/device capabilities, and policy, meaning not every method is supported for every application.
SEEING
IS BELIEVING
Whether you are buying a car or a security solution, you always want to test drive it before signing on the dotted line. We know this and you know this.
Contact us for your Free PoC or check it out for yourself.